The landscape of data privacy has shifted. In 2026 and beyond, simply finding strings of text isn’t enough to satisfy auditors or modern regulations like the EU AI Act. Whether you’re preparing for a compliance audit or starting a trial, knowing how to evaluate sensitive data discovery software is vital. To avoid wasting time on “legacy” tools that rely on … Read More
Take Control of Your Personal Data in 2026: A Strategic Guide

In 2026, personal data is no longer just information; it’s the fuel for AI models and the primary target for sophisticated, identity-driven cyberattacks. With the EU AI Act fully active and global privacy fines hitting record highs, simply “having” a privacy policy isn’t enough. You need technical mastery over every byte of sensitive data in your ecosystem. The Problem: “Invisible” … Read More
Key Data Privacy Changes Shaping 2026
AI, Regulation, and the Rise of “Technical Truth” In 2026, data privacy is no longer a legal formality or a checkbox exercise; it’s a core component of business survival. Regulators have shifted their focus from “policies on paper” to “technical truth,” actively testing whether organizations can actually enforce the rights they claim to protect. The 2026 Regulatory Landscape: Beyond the … Read More
Fast & Accurate Data Breach Resolution
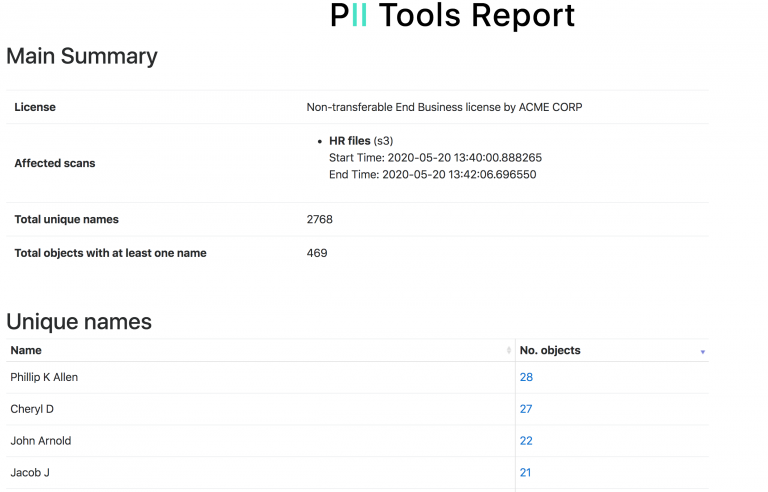
You’ve suffered a data leak, and the clock’s already ticking. Oh, and it’s a large dataset, too. Where do you even start to locate every single instance of PII involved? Let’s get into it! Breach Incident Scanner Discovering leaked sensitive information and PII by hand is completely unrealistic for large datasets, so automated solutions like PII Tools come in handy. … Read More
Can AI Accurately Identify Person Names in Text?

Detecting person names correctly while avoiding false positives is a real time-saver for breach investigations, DSARs, and regulatory compliance. But can this process be automated with AI? Let’s find out. Person Name Identifiers A person name identifier is any information that can be used to directly or indirectly identify an individual, with their actual name being the primary example. Use … Read More
PII and Its Many Forms

Sensitive data and personal information come in many shapes and sizes. And with so many different regulations around the globe, it’s easy to confuse one with another. These are the basics of PII and every form you’ll find it in. Let’s get into it. Understanding PII The world of sensitive data protection has its own terminology you’ll need to be … Read More
How to Avoid Uploading Sensitive PII to Microsoft Copilot

AI tools like ChatGPT and Microsoft Copilot can be useful time savers, but at what cost? There’s no reason you can’t get the best of both worlds—helpful AI models and secure PII. Let’s get into it. Major Copilot Concerns Estimates show that Microsoft Copilot has as many as 33 million active users. And yet, it comes with multiple security risks … Read More
Discovering Person Names in Texts Made Easy

PII Tools streamlines detecting person names with +99% accuracy, even rolling them into Person Cards® for easier export and remediation. Let’s find out how. Basics of Person Name Discovery Detecting people’s names in text is the most fundamental activity in sensitive data discovery. But there are many ways to achieve this task, some more effective than others. The main driver … Read More
PII Examples

Below you’ll find an example list of Personally Identifiable Information, or PII, to help you better understand how it can appear in the real world. You’ll also find FREE downloadable files attached to each point with specified (fake) PII examples you can then use to test your discovery solution. Enjoy. PII includes, but is not limited to: Names: Full name, … Read More
Detect person names in text: Part 1 (Results)
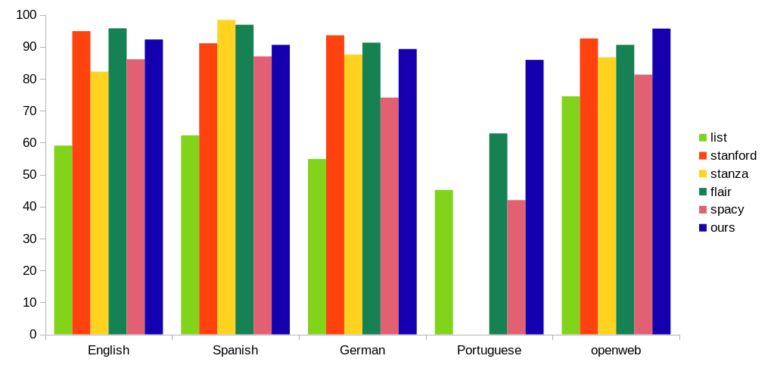
Detecting people’s names is part and parcel of PII discovery. Traditional techniques like regexp and keywords don’t work because the set of all names is too varied. How do open-source Named Entity Recognition (NER) engines compare, and can we do better? Part 1 deals with NER results and benchmarks, while Part 2 discusses technical neural network details. Or download the … Read More





