Automate Legal Data Reviews, Reduce Costs
With PII Tools, you can seamlessly automate the detection and redaction of sensitive information, streamlining your workflow and reducing costs.
Protect your clients and your reputation with a solution designed to mitigate data risks effortlessly.
Built for the Entire Legal Industry
Our Customers Say…

Mark Cassetta
SVP Strategy
“Our survey found that 22% of the time, humans failed to identify personal data in documents, while PII Tools succeeded in all scenarios. By integrating with PII Tools, Titus was able to significantly reduce the compliance risk for our customers.”


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”


Shane Reid
Group Director, CEO – North America
“Integrating PII Tools has allowed Umlaut Solutions to handle petabytes of client data seamlessly, enhancing accuracy and reducing the risk of data breaches.”

One Unique Solution for Your Data Discovery Needs
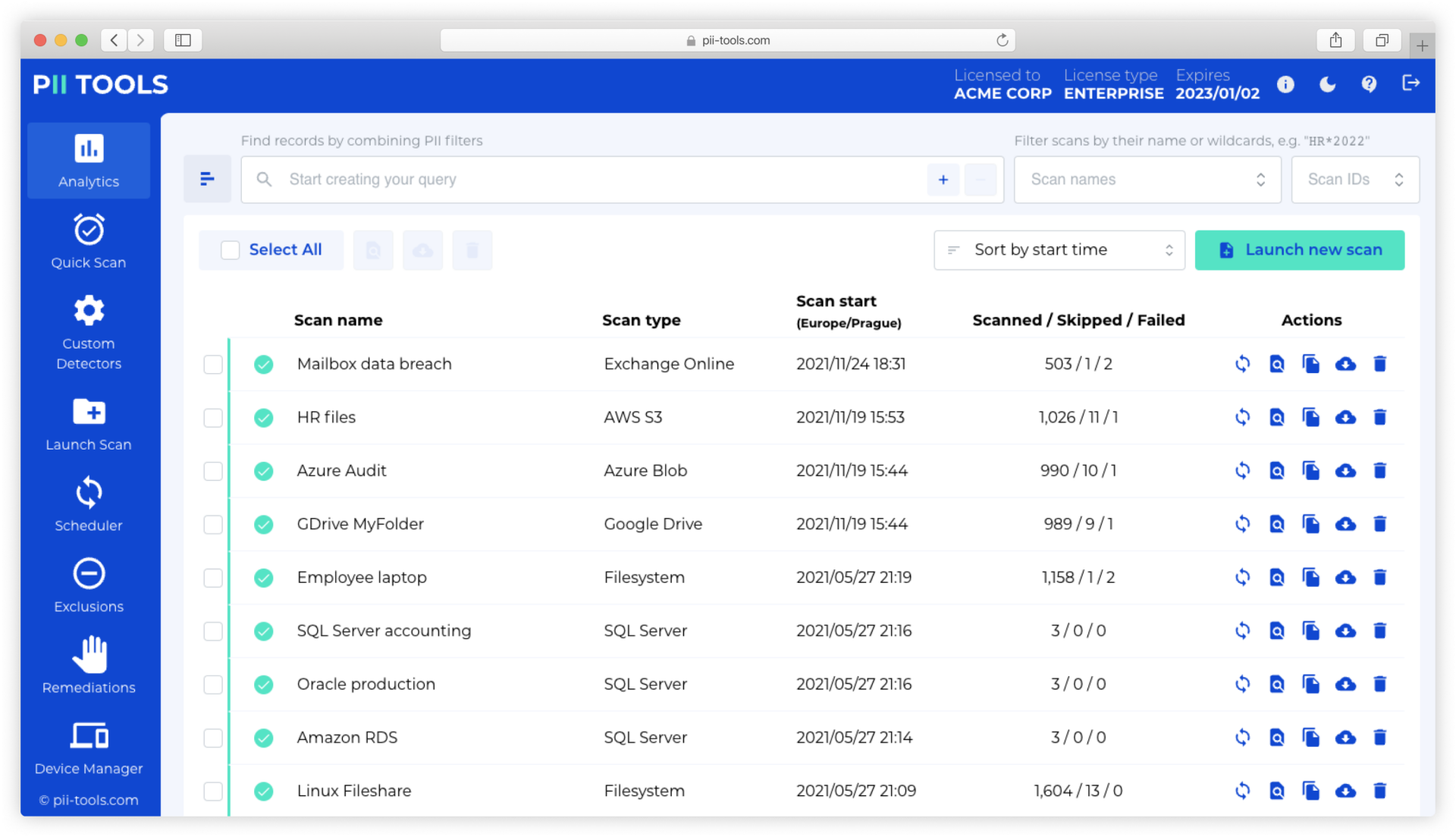
How Does PII Tools Help?
Breach Incident Management
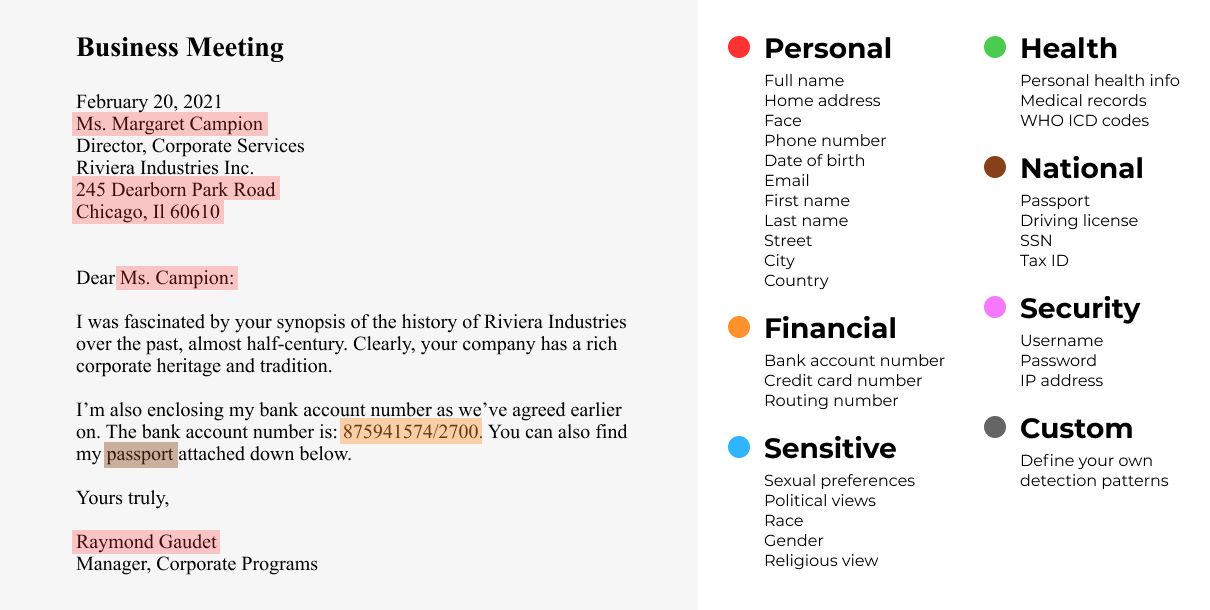
The first step to mitigate the damage is to identify what was leaked: all affected persons and their PII, PCI, and PHI. PII Tools helps incident response teams find the breached personal data in emails, files, databases, and even fully air-gapped environments.
Client Assessment
Support your clients with actionable risk evaluation based on their actual data, prepare them for an audit, or discuss their next steps over interactive data risk reports. Scan actual data content automatically and avoid human mistakes.
Risk Identification
Take control of latent risk in your data storages, no matter how large or chaotic they may seem. Discover personal and sensitive data in every file, email, database, cloud environment, and even local endpoints and devices.
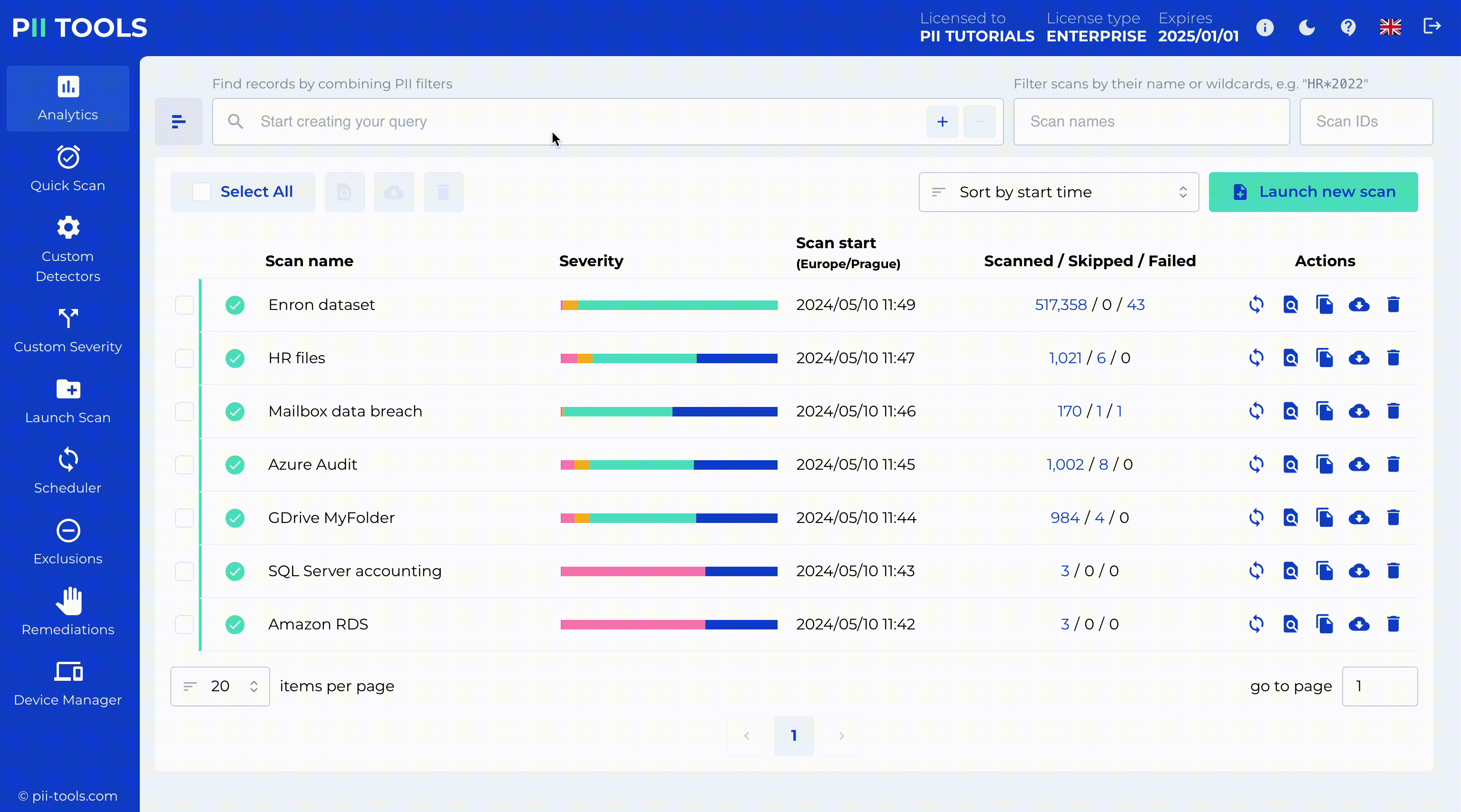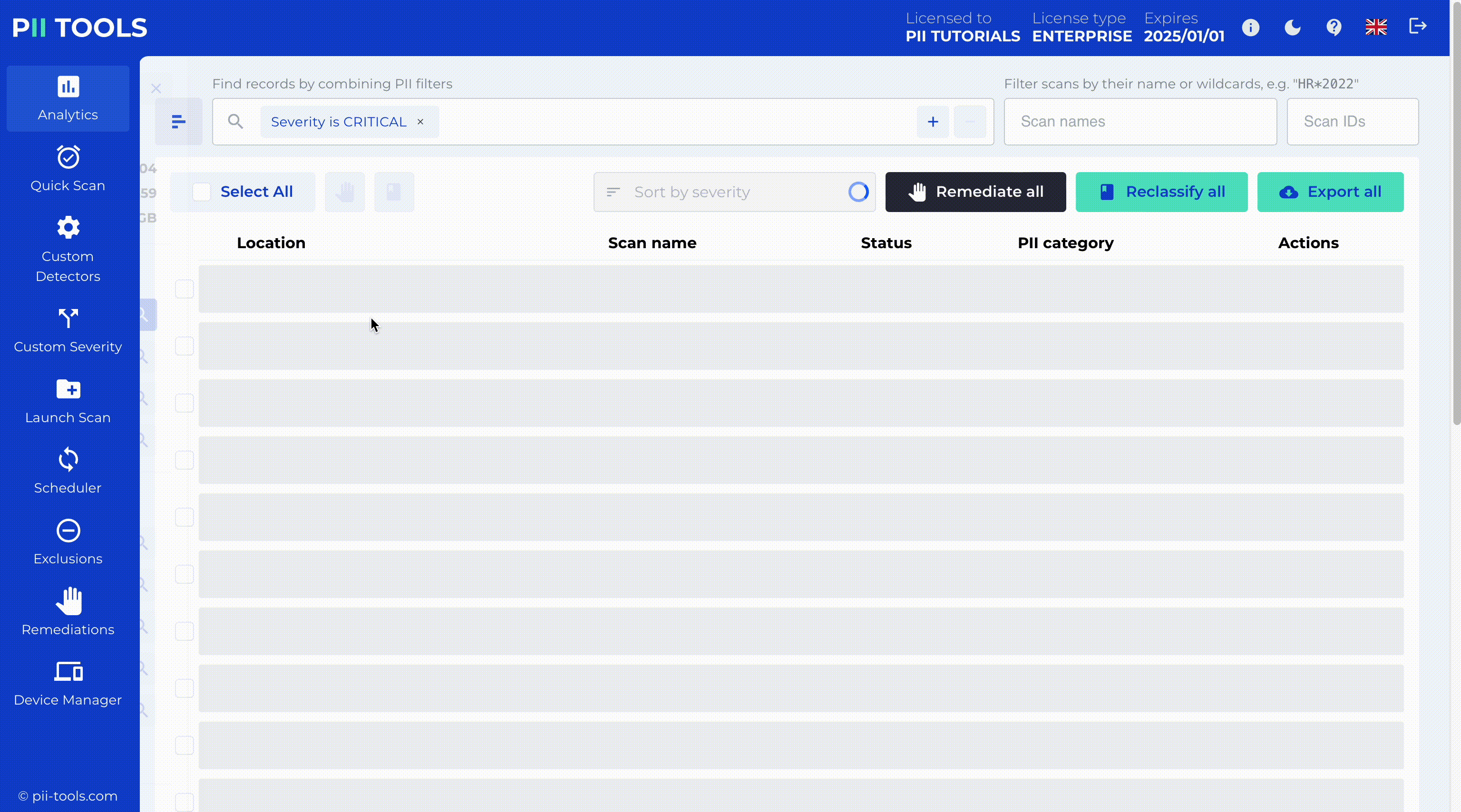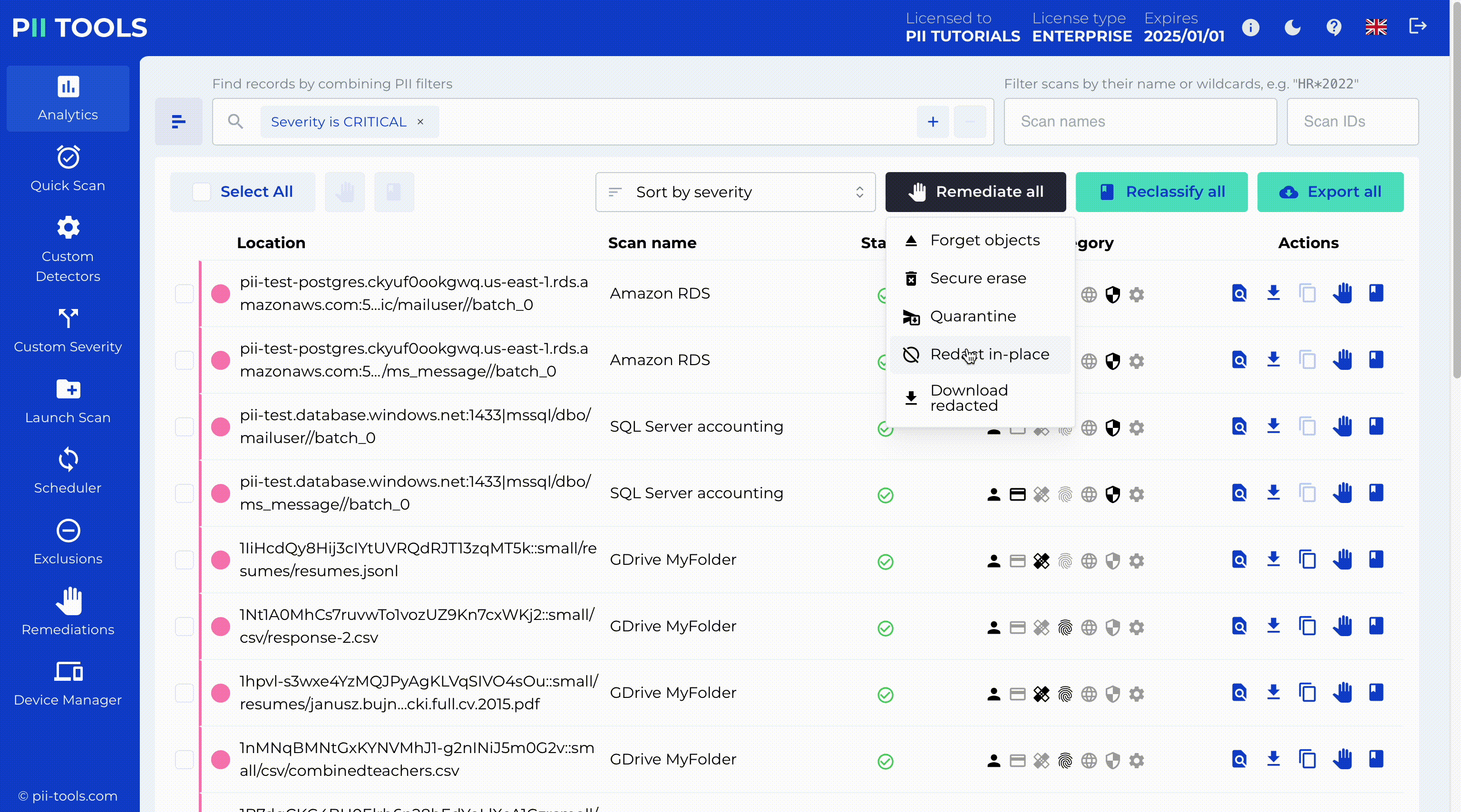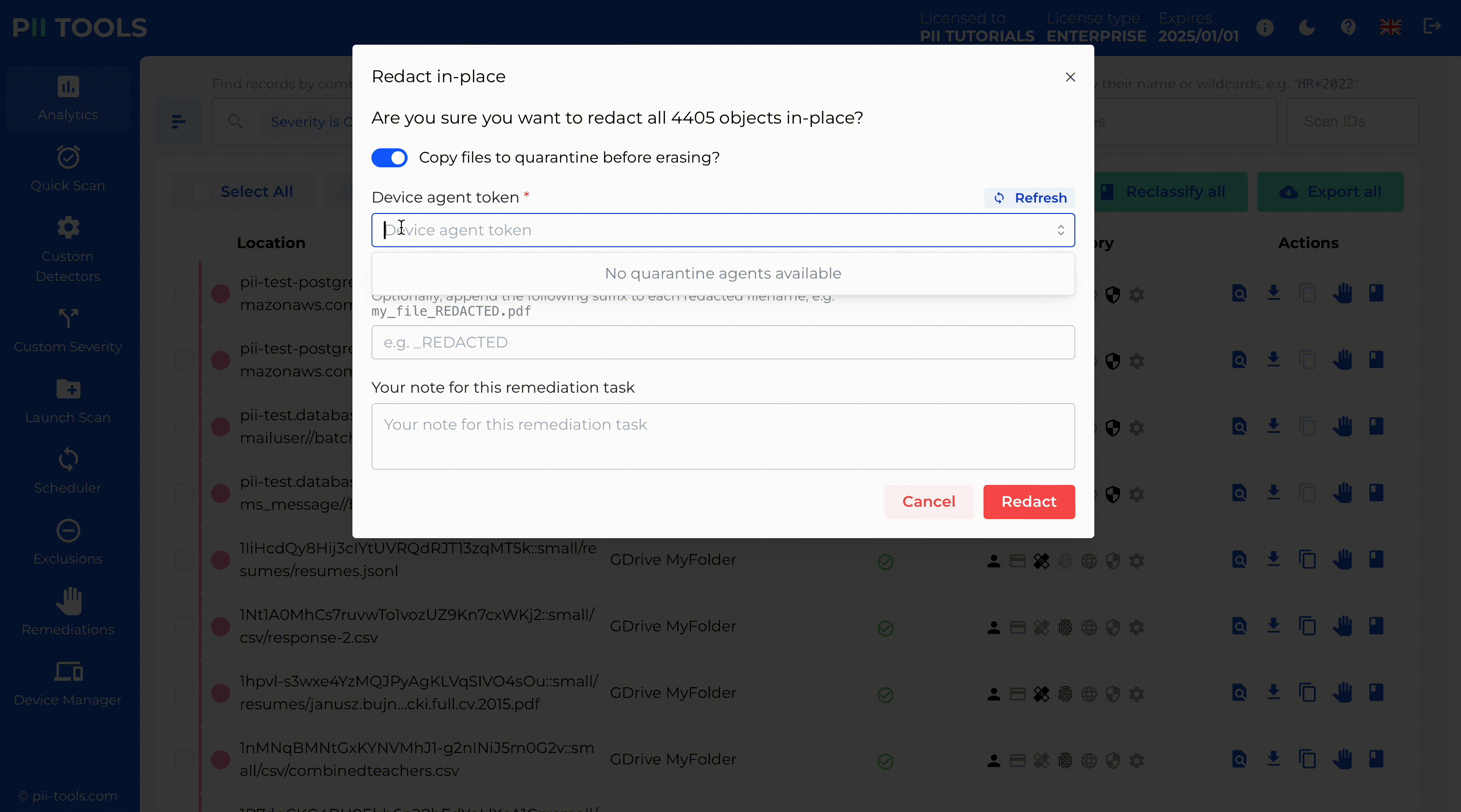
Ready For Human Review
Set up workflows that put humans in charge. Built-in analytics allow you to surgically manage and remediate (erase, quarantine, encrypt, redact, or label) every PI instance detected.
Precise Reporting
Rely on AI-driven PII scans with over 99% detection accuracy. Evaluate high-risk areas based on actual data and support the IT and GRC teams with interactive drill-down reports.

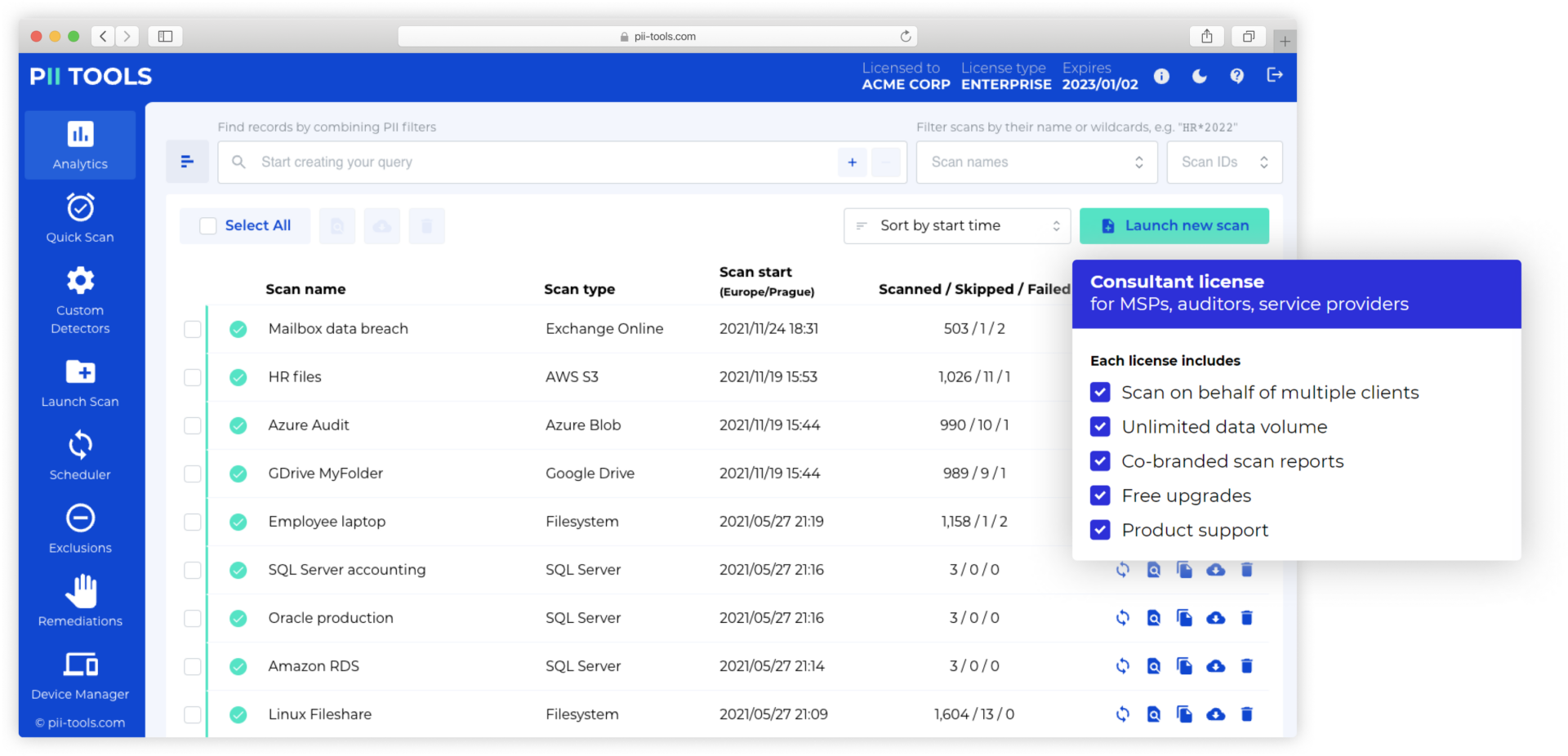
The Ideal License
Choose exactly the right license, depending on your actual requirements. We offer several licensing and integration options. And don’t worry, you can always scale up.