Part 3 of 3: Data Leak Prevention in 10 Easy Steps The 3rd and final article in this mini-series. Part 1 taught us the basics of data breach prevention, while Part 2 provided the ideal employee training. Now, how many of these data security points can you check off? Data Security Health Is data leak prevention a priority in your … Read More
A Beginner’s Guide to GLBA Compliance

The GLBA affects all financial institutions directly. This comprehensive guide provides an in-depth understanding of the GLBA, including all its latest updates and amendments. Let’s dive in. Intro to the GLBA The Gramm-Leach-Bliley Act (GLBA for short) is a US federal law that requires “financial institutions” – defined as companies offering customers financial products or services like loans, financial or … Read More
Scan Microsoft 365 Copilot for Sensitive Data & PII

Discover and remediate personal and sensitive data inside Microsoft 365 Copilot accounts. This includes both structured and unstructured data in Microsoft OneDrive, Microsoft Exchange Online, and SharePoint Online. Full Microsoft 365 Copilot Support Microsoft’s AI chatbot, known as Copilot, recently became an integral part of Office 365. The official name is now Microsoft 365 Copilot, and PII Tools is still … Read More
How to: Protecting ePHI

The average healthcare breach exposes 3+ million private patient records. What are you doing to discover, store, and protect ePHI? Why the ‘e’ in ‘ePHI’? HIPAA, PHI, PII, GDPR, ePHI… Where would we be without our acronyms? If you’re interested in protecting ePHI, it’s safe to say none of these are entirely new to you. The most important to our … Read More
Using PII Tools on a Daily Basis

As every GRC team member knows all too well, manually sifting through the company’s seemingly infinite TB of stored data is a full-time job (or a waste of time). But now, with advances in AI-driven data discovery, what does the day of an average PII Tools user actually like? Streamlining Data Discovery The day-to-day mission of any GRC team (Governance, … Read More
Regular Audits: Do You Really Need Them?

There’s nothing worse than wasting time and money, so is there any benefit to reviewing the data you store? Well, unless you want to be like the kid who never studies for tests, regular audits may be the only thing keeping you out of the principal’s office. To Audit or Not to Audit? By this point, I would hope none … Read More
How to Identify Leaked Data

A data breach can happen to anyone at any time. Although there are many steps in responding to such a breach, the first is actually locating the data in question. If you’ve suffered a breach of information, how do you identify all affected parties? Detecting the Leak There are multiple ways you can tell you’re dealing with a data breach, … Read More
The What, Why, and How of PII Auditing
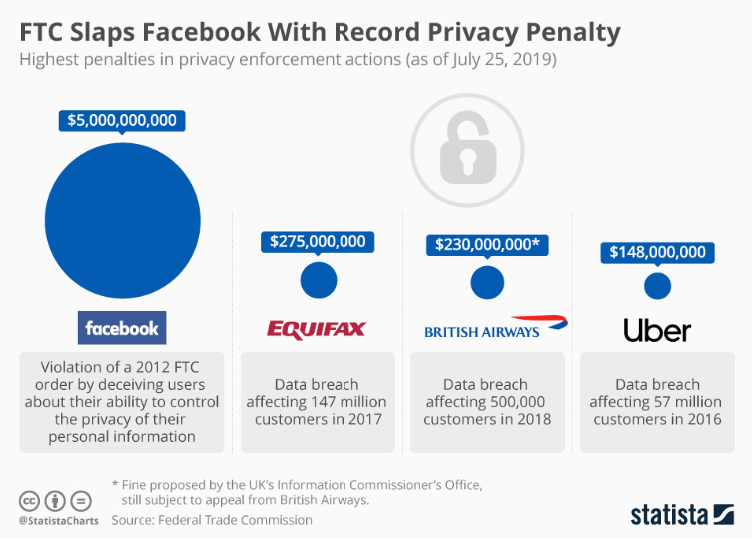
You’ve heard stories of companies running into trouble by not maintaining PII compliance and suffering severe legal ramifications. But what does that mean for you? Out of all the data you have, you’re sure you don’t have any PII lurking around in unwanted or even unlawful areas, right…? Ready or not, your next scheduled PII audit is around the corner. … Read More