As every GRC team member knows all too well, manually sifting through the company’s seemingly infinite TB of stored data is a full-time job (or a waste of time). But now, with advances in AI-driven data discovery, what does the day of an average PII Tools user actually like?
Streamlining Data Discovery
The day-to-day mission of any GRC team (Governance, Risk, and Compliance) varies wildly, depending on everything from workload and company size to the type of information stored and its physical location. However, when PII Tools software is implemented, many of those data security processes start looking similar across the board.
Now, of course, no two use cases can be completely 1:1. But the daily work of searching for and discovering potentially at-risk personal data among corporate files has been streamlined by PII Tools. It’s not always just as easy as pushing a button, but automatic data discovery is as close as you can get.
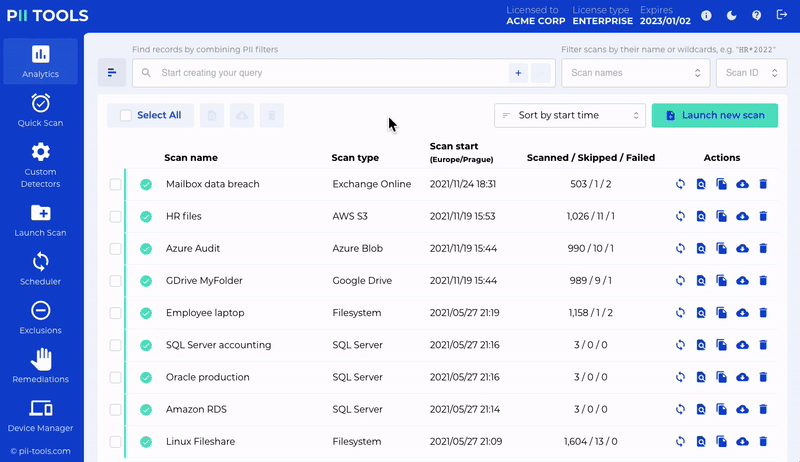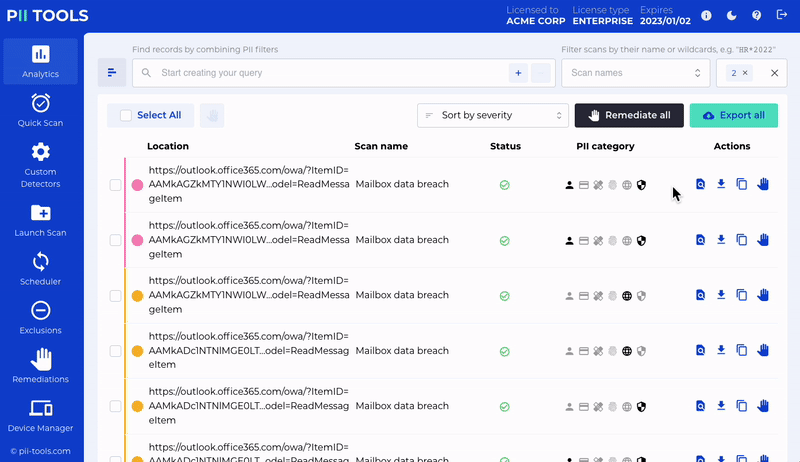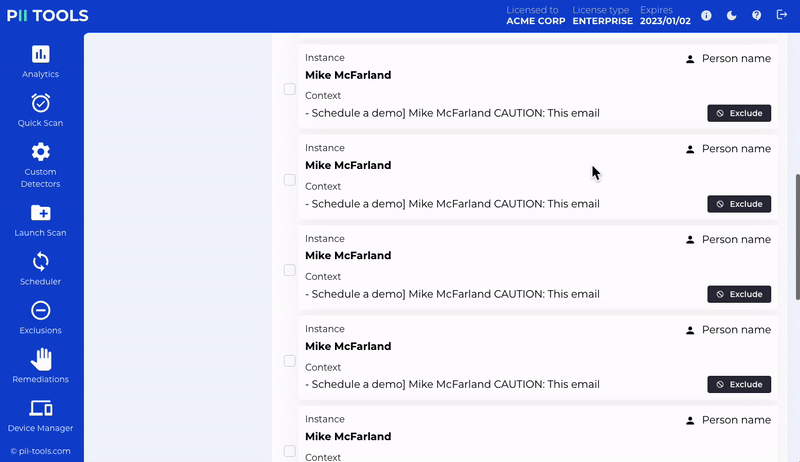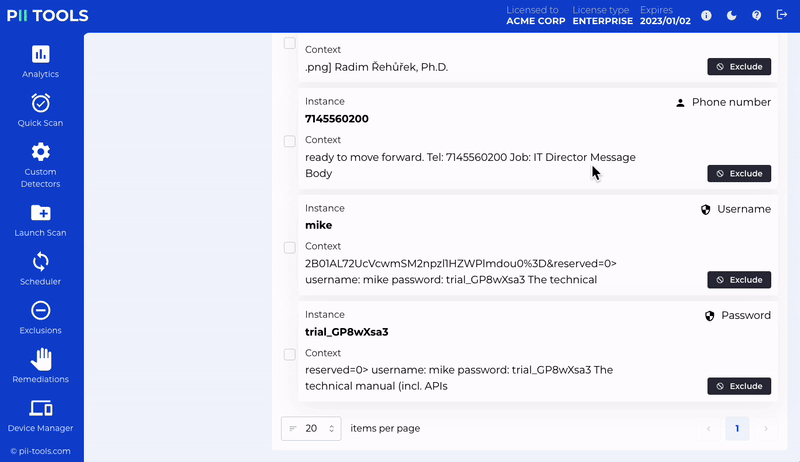

Automatic Discovery in Action
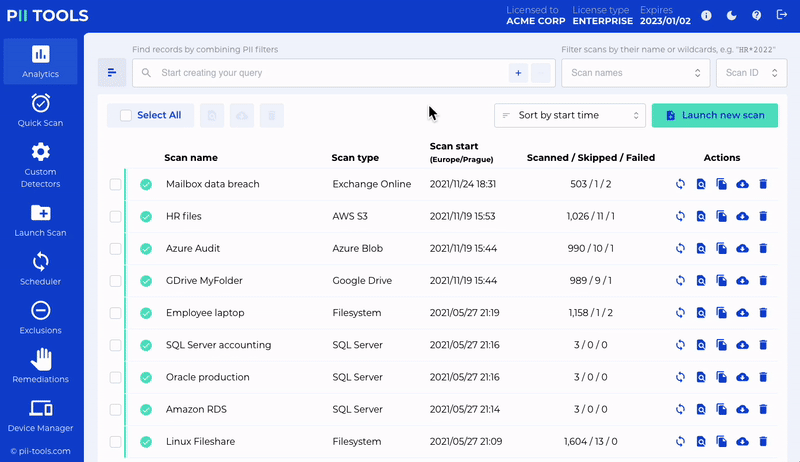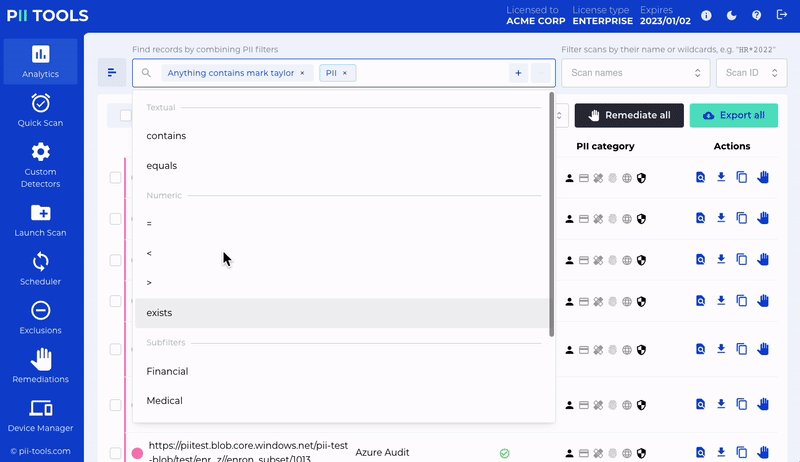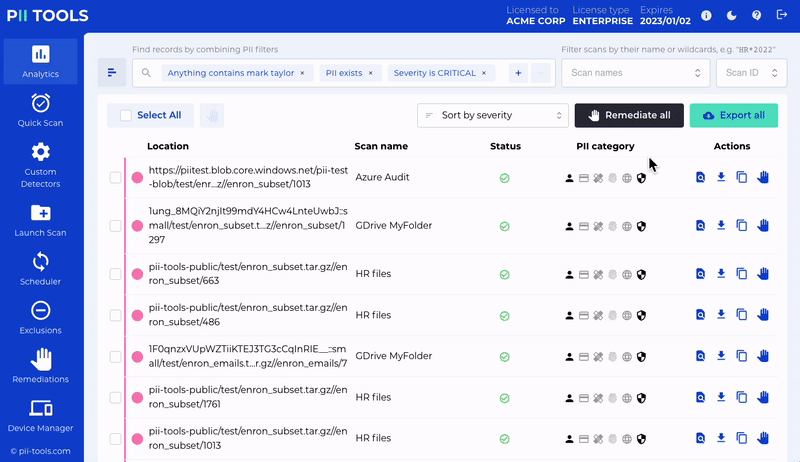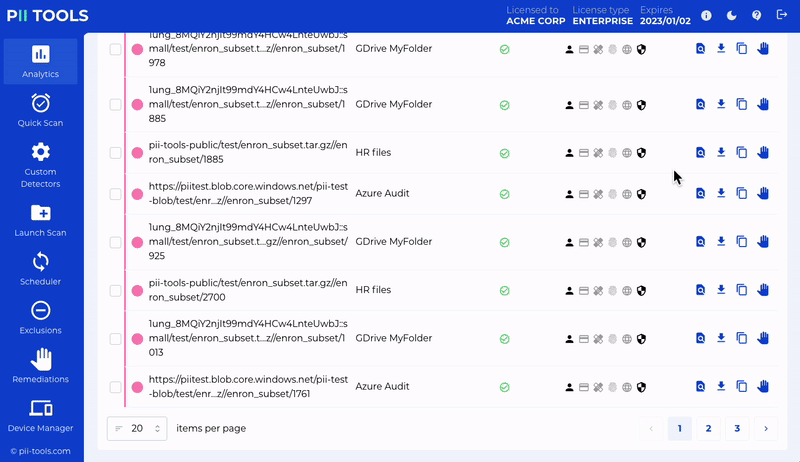
Automatic data discovery is the process of setting up a repeating scan that you want to run on a regular basis. You select the precise parameters of the scan and then sit back and let it do all the heavy lifting.
This is exactly what the retail company Woolworths did. With over 200 active stores and a busy online division, their GRC team was tasked with finding a more efficient way to search through the company’s terabytes on terabytes of stored data.
Having arranged the in-house scans to meet their specific needs (including data implicit to the PCI DSS and POPI Act), Woolworths was able to take their typical 3-4 week scan timeline and shrink it down to a single day!


But what happens after their scan is completed? Especially if some real at-risk data has been discovered?
Daily Remediation
The next major step in sensitive data discovery and protection is remediation. When a scan is finished, you’ll receive a report showing all and any at-risk files, which have then been automatically classified by their risk level.
It’s easy to see a member of a GRC team receiving a completed report and reviewing the red CRITICAL files first and foremost. They can then decide how those files should be remediated.
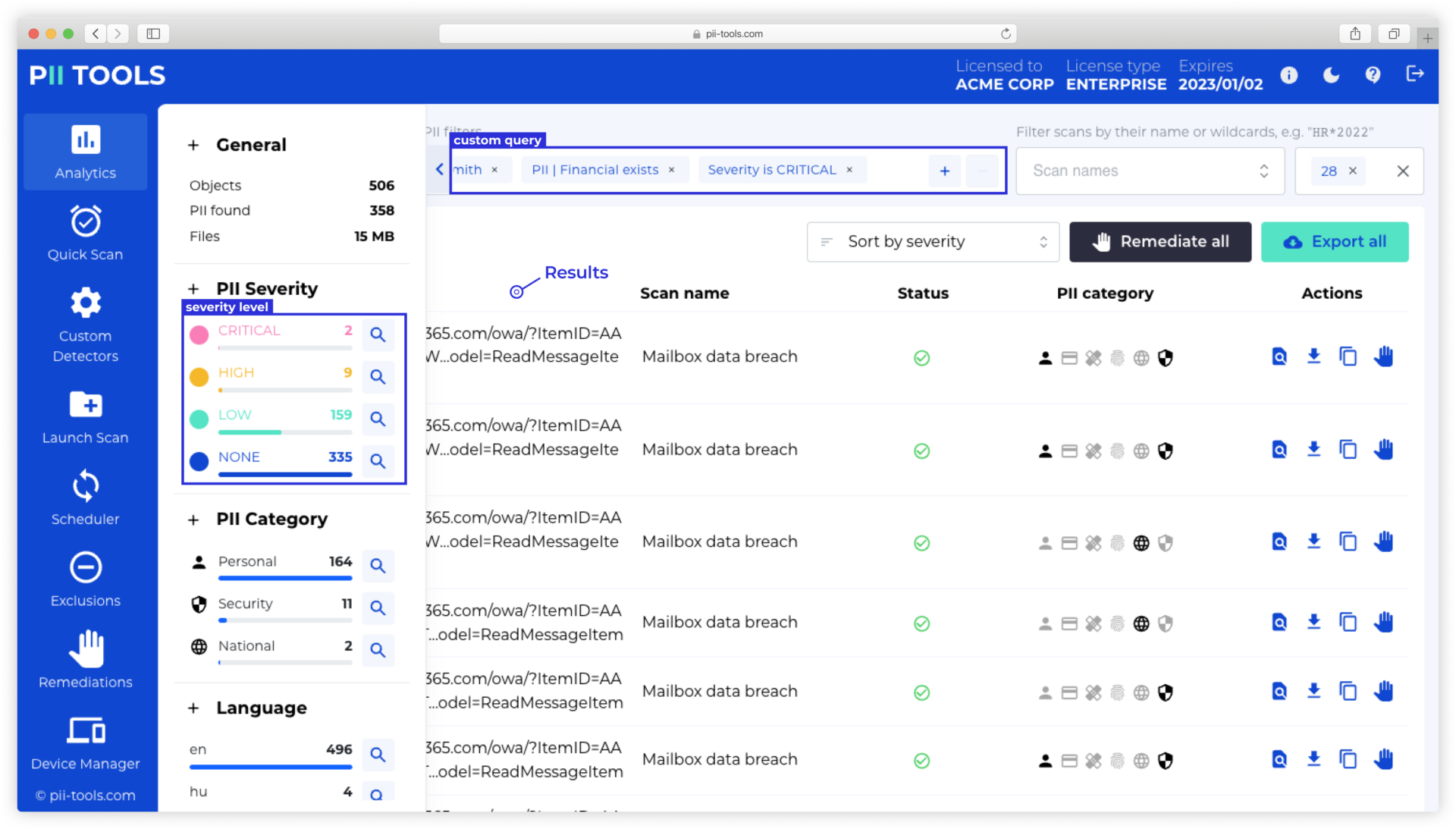

This could include moving the location of certain data to a more secure, regulation-compliant location or simply deleting them altogether. PII Tools even allows you to quarantine and redact files at any time.
Code RED: Data Breach
And that’s really all there is to it. PII Tools and its automatically scheduled scans make the work for DPOs, Information Security Analysts, IT divisions, and GRC teams easier than ever. But there are more possible scenarios in which users implement the software worldwide. For instance, what if today’s daily scanning routine is interrupted by, heaven forbid, a data breach?
Luckily, PII Tools was built to help resolve data breaches as soon as possible, and with as little headache as possible. Thanks to the software’s 99+% accuracy, rapid analytics, and ability to detect PII data in over 400 file formats, you can put a lid on any data breaches before they get out of hand (to learn more about Data Breach Management using PII Tools, check out our in-depth article on the subject).
Simplifying PII Data Discovery for All
Although the “day in the life of your average PII Tools user” can vary by company, in-house processes, scale, and scenario, PII Tools is deployed in a similar fashion to resolve countless issues.
Its AI-driven, automatic scan schedules mean that, after some initial setup, you can simply let the software take the reigns and only get involved when searching for something specific, reviewing actionable data, or reacting to a crisis situation.

But of course, PII Tools can do so much more than run automatic in-house audits on your behalf. That includes cloud data scanning, person cards reports, helping you with client assessments, and so much more. You’ll quickly find that PII Tools can be used in a plethora of ways.
So, what’s stopping you from simplifying your workflow and adding PII Tools’ tested software to improve how your company discovers, stores, and protects sensitive data on an everyday basis?
Use PII Tools to Boost Your Corporate “PII Health” with Every Passing Day!




