GLBA non-compliance fines can reach as high as $100,000 per violation. Learn how to protect both your customers and your budget with full GLBA compliance. Let’s get started! What Is the GLBA? The Gramm-Leach-Bliley Act (GLBA, for short) is a US federal law that requires financial institutions to explain their information-sharing practices to customers and safeguard sensitive data. If you’re … Read More
Self-Hosted Software vs SaaS

Your corporate data is safest when kept within self-hosted software over SaaS. But are there any other advantages, and how can you leverage them? Time to see how self-hosting compares against SaaS! Self-Hosted Software or SaaS? Companies that opt to secure their sensitive data within self-hosted software benefit in many ways compared to Software-as-a-Service (SaaS) options, even if these appear … Read More
Self-Hosted Unaffected by Global Cloudflare Outage

Millions of users were hit by the recent Cloudflare outage, resulting in massive blackouts for countless businesses. Yet, all PII Tools users remained untouched. This is how “going self-hosted” keeps you in the game. Cloudflare Outage On November 18, 2025, the global online world was suddenly struck with widespread disconnections. Thousands of popular websites were rendered useless, including everything from … Read More
The Human Factor: 10-Point Data Security Checklist
Part 3 of 3: Data Leak Prevention in 10 Easy Steps The 3rd and final article in this mini-series. Part 1 taught us the basics of data breach prevention, while Part 2 provided the ideal employee training. Now, how many of these data security points can you check off? Data Security Health Is data leak prevention a priority in your … Read More
A Beginner’s Guide to GLBA Compliance

The GLBA affects all financial institutions directly. This comprehensive guide provides an in-depth understanding of the GLBA, including all its latest updates and amendments. Let’s dive in. Intro to the GLBA The Gramm-Leach-Bliley Act (GLBA for short) is a US federal law that requires “financial institutions” – defined as companies offering customers financial products or services like loans, financial or … Read More
The Human Factor: The Perfect Employee Training

Part 2 of 3: Reducing Data Leaks + Data Security Awareness Employees are responsible for 90% of all data breaches! That’s why Part 1 of this mini-series discusses the basics of data leaks, while Part 2 tackles the source of the problem: Human error. This is the last employee training you’ll ever need! 1. Intro to Information Security All employees … Read More
Data Loss Prevention: 3 Basic Steps to Data Protection
$4.44 million. That’s the average cost of a data loss instance in 2025. Unless you’ve got that kind of cash just lying around, taking steps toward Data Loss Prevention will be your best option. But who’s keeping your data safe? Intro to Data Loss Prevention Before you get anywhere near avoiding that 4-million-dollar “hit” to the yearly budget, you first … Read More
The Human Factor: How to Eliminate Data Breaches Caused by Employees

Part 1 of 3: Data Leak Basics (Part 2, The Perfect Employee Training; Part 3, 10-Point Data Security Checklist) Nearly 90% of breach incidents are caused by human error. This 3-part mini-series tackles the subject head-on, covering everything from root causes and prevention techniques to the perfect employee training. Let’s get started. What is a Data Leak? A data leak, … Read More
Fast & Accurate Data Breach Resolution
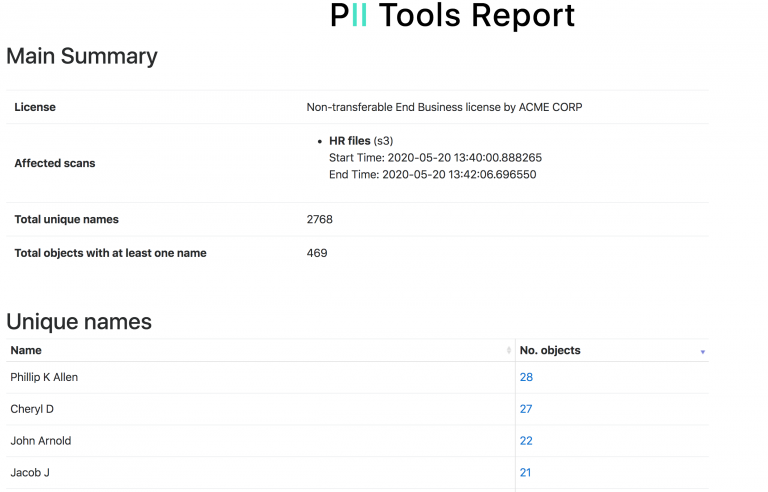
You’ve suffered a data leak, and the clock’s already ticking. Oh, and it’s a large dataset, too. Where do you even start to locate every single instance of PII involved? Let’s get into it! Breach Incident Scanner Discovering leaked sensitive information and PII by hand is completely unrealistic for large datasets, so automated solutions like PII Tools come in handy. … Read More
Can AI Accurately Identify Person Names in Text?

Detecting person names correctly while avoiding false positives is a real time-saver for breach investigations, DSARs, and regulatory compliance. But can this process be automated with AI? Let’s find out. Person Name Identifiers A person name identifier is any information that can be used to directly or indirectly identify an individual, with their actual name being the primary example. Use … Read More





