Part 1 of 3: Data Leak Basics (Part 2, The Perfect Employee Training; Part 3, 10-Point Data Security Checklist) Nearly 90% of breach incidents are caused by human error. This 3-part mini-series tackles the subject head-on, covering everything from root causes and prevention techniques to the perfect employee training. Let’s get started. What is a Data Leak? A data leak, … Read More
How to Scan for PCI DSS Data

Effortlessly locate every piece of credit card data and streamline your PCI DSS compliance with PII Tools. Perform in-house audits, remediate at-risk data, and avoid potential fines. This is how. Intro to PCI DSS The Payment Card Industry Data Security Standard (PCI DSS, for short) is an information security standard organized by major credit card companies (Visa, Mastercard, etc.), aimed … Read More
Step-by-Step Employee Training: PII Protection Awareness

As much as 90% of security breaches and data leaks are caused by human error. Follow these 5 Steps to hold your own employee training on PII Protection and Cyber Awareness. Introduction to PII Personally Identifiable Information, or PII, must be a household acronym for all employees. They need to be able to recognize it immediately, as well as show … Read More
Redaction
The best way to safeguard sensitive data is to keep it out of sight — and out of reach. The 3rd and final section in this 3-part mini-series explores Data Redaction and the irreversible role it plays in PII protection. Let’s get into it. What is Data Redaction? Ever see a spy movie featuring ‘classified’ files? Pages and pages of … Read More
Data Masking

The best way to safeguard sensitive data is to keep it out of sight — and out of reach. Part 2 of this 3-part mini-series explores Data Masking and the irreversible role it plays in PII protection. Let’s get into it. What is Data Masking Data masking is a non-reversible transformation process that “masks” sensitive data by partially or fully … Read More
Data De-Identification
The best way to safeguard sensitive data is to keep it out of sight — and out of reach. This 3-part mini-series explores the 3 BEST anonymization tactics for processing and storing protected information. Let’s learn how. What is Data De-Identification? The first TOP method of data anonymization is called Data De-Identification. In layman’s terms, data de-identification is the process … Read More
Creating Data Leak Reports
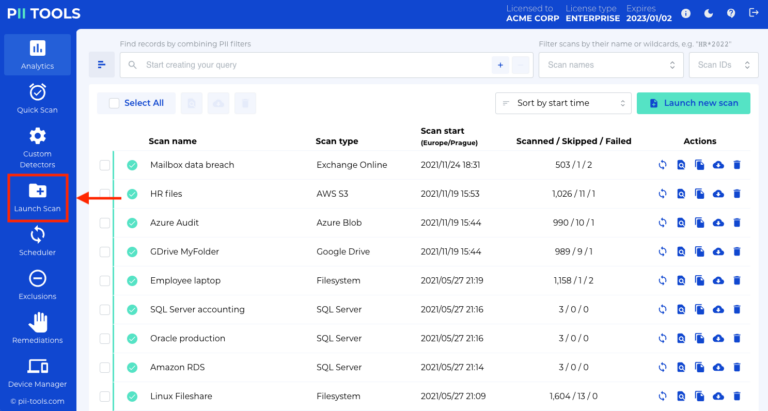
In this guide, you will learn how to create data leak reports with PII Tools. Launching a scan The first step towards the successful management of any data leak is to identify what was in the breached data. Open your PII Tools and, on the left side, select Launch Scan. If you performed the scan already, skip to the next … Read More





