Sensitive data and personal information come in many shapes and sizes. And with so many different regulations around the globe, it’s easy to confuse one with another. These are the basics of PII and every form you’ll find it in. Let’s get into it. Understanding PII The world of sensitive data protection has its own terminology you’ll need to be … Read More
PII Examples

Below you’ll find an example list of Personally Identifiable Information, or PII, to help you better understand how it can appear in the real world. You’ll also find FREE downloadable files attached to each point with specified (fake) PII examples you can then use to test your discovery solution. Enjoy. PII includes, but is not limited to: Names: Full name, … Read More
AI and Machine Learning in Sensitive Data Management

With more tools at our disposal than ever before, how can you use artificial intelligence and machine learning to handle PII and sensitive data effectively? Modern AI & Machine Learning At this point, artificial intelligence (AI) and machine learning (ML) don’t need much of an introduction. Our phones, cars, televisions… even some smart refrigerators come equipped with AI and ML … Read More
Classify Data in 3 Easy Steps
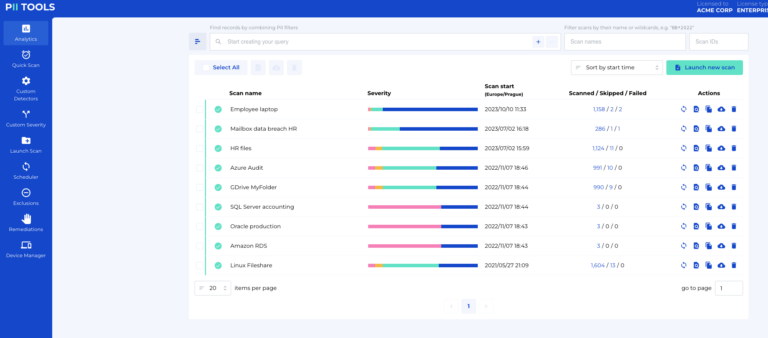
Quick scans, Custom Detectors, and Custom Severity. Learn to classify information automatically and guarantee every piece of your data protection puzzle is perfectly in place. Why Classify Data? Before we get to the details, it’s worth mentioning the main reasons why you should even bother to classify different types of personal data. On average, companies keep over 2 PB of … Read More
Data Redaction: The Essential Guide to Protecting Sensitive Data
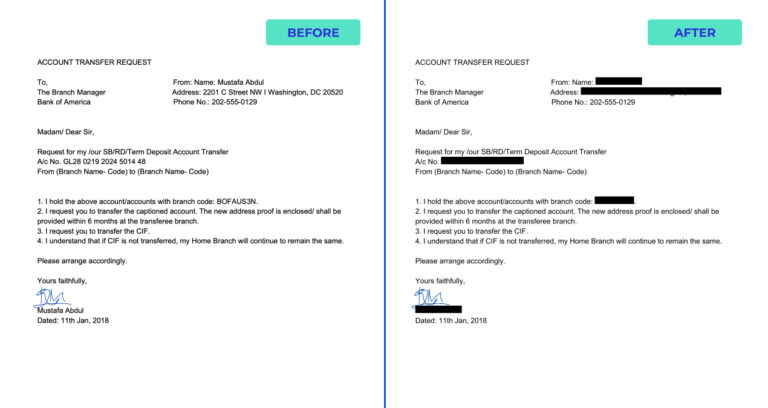
The long-awaited data redaction feature by PII Tools is finally here. Generate new, AI-driven PDFs from original files with all personal data automatically blacked out – this is the future of genuinely efficient data redaction. What Does Data Redaction Mean At PII Tools, we’ve made it our calling to create AI-driven software to maximize data discovery and the remediation of … Read More
Person Cards® – The Holy Grail of Data Discovery
By 2025, the global datasphere is estimated to hold as much as 175 zettabytes of data. How can companies today possibly have a chance to organize that much information? The answer: Person Cards®. More Data, More Problems 175 zettabytes of data worldwide? Considering a single zettabyte is equal to a trillion gigabytes (yes, with a ‘T’), the actual amount of … Read More
Regular Audits: Do You Really Need Them?

There’s nothing worse than wasting time and money, so is there any benefit to reviewing the data you store? Well, unless you want to be like the kid who never studies for tests, regular audits may be the only thing keeping you out of the principal’s office. To Audit or Not to Audit? By this point, I would hope none … Read More
Do They Even Matter?—The 3 Largest GDPR Fines To Date
For years now, the GDPR has been criticized for offering more bark than bite. As the fines stand, many mega-companies like Amazon and Google are simply getting away without a scratch. All this has left us wondering, what are the 3 biggest GDPR fines so far, and do any of them actually matter? Knowing the GDPR Before we get to … Read More
How To: Understanding HIPAA Compliance
For many readers, when they hear the words “the Health Insurance Portability and Accountability Act (HIPAA)”, their eyelids immediately start to droop. But I’m sure getting slapped with an annual $1.5 million fine would wake them up! Whether you’re the one handling the data or the actual patient looking to protect your rights, it’s time to become a HIPAA expert … Read More
How to Identify Leaked Data

A data breach can happen to anyone at any time. Although there are many steps in responding to such a breach, the first is actually locating the data in question. If you’ve suffered a breach of information, how do you identify all affected parties? Detecting the Leak There are multiple ways you can tell you’re dealing with a data breach, … Read More
- Page 1 of 2
- 1
- 2





