The California Consumer Privacy Act puts consumers back in the driver’s seat of their own sensitive information, while also requiring a lot from businesses. Let’s discuss the details. CCPA In 2018, the State of California Department of Justice approved the implementation of the California Consumer Privacy Act. In many ways, this data privacy regulation is similar to the GDPR, however, … Read More
PII De-Identification vs. Masking vs. Redaction
There’s a fine balance between processing users’ PII and storing it safely. The primary ways to encrypt information are Data De-Identification, Data Masking, and Data Redaction. But how exactly do they work? Let’s explore. Data De-Identification To put it plainly, data de-identification is the process of removing personally identifiable information (PII) from data. The purpose of data or PII de-identification … Read More
AI and Machine Learning in Sensitive Data Management

With more tools at our disposal than ever before, how can you use artificial intelligence and machine learning to handle PII and sensitive data effectively? Modern AI & Machine Learning At this point, artificial intelligence (AI) and machine learning (ML) don’t need much of an introduction. Our phones, cars, televisions… even some smart refrigerators come equipped with AI and ML … Read More
The Evolution of PII Protection: From Paper to Digital

PII has come a long way in a relatively short time, yet protecting it fully is like trying to shield a moving target. But sometimes the best way to choose a path forward is to peek at the past and learn from its evolution. Humble Beginnings It’s hard to think about PII, or rather Personally Identifiable Information, without also imaging … Read More
3 Major Changes with PCI DSS v4.0.1

The long-awaited update to version 4 of the PCI DSS has only been in force since spring 2024. And already it’s been revised into v4.0.1. Let’s take a look at 3 changes you need to know about. First There Was v4 Before we get too deep into this latest revision, it’s important we’re all up to speed on this set … Read More
Understanding PCI DSS v4.0

Understanding PCI DSS v4.0 The latest update to the PCI DSS is finally in full force. Discover the ins and outs of this sometimes tricky regulation and make sure you’re processes are still up-to-date. Let’s get into it! A Quick Refresher If your business accepts cards in any way, it’s safe to guess you’re already well familiar with the PCI … Read More
How to: Protecting ePHI

The average healthcare breach exposes 3+ million private patient records. What are you doing to discover, store, and protect ePHI? Why the ‘e’ in ‘ePHI’? HIPAA, PHI, PII, GDPR, ePHI… Where would we be without our acronyms? If you’re interested in protecting ePHI, it’s safe to say none of these are entirely new to you. The most important to our … Read More
Data Redaction: The Essential Guide to Protecting Sensitive Data
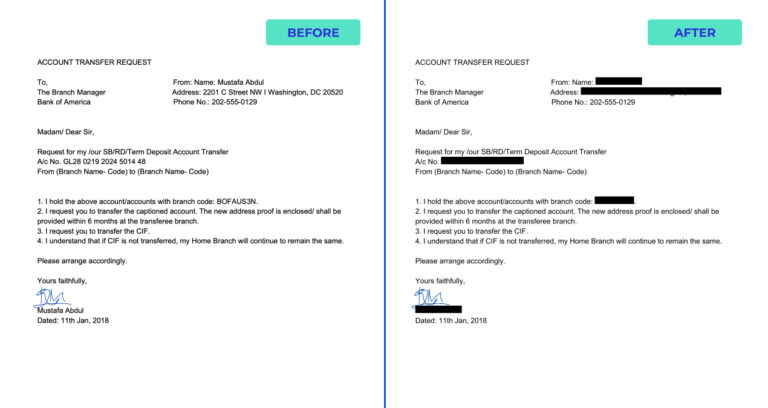
The long-awaited data redaction feature by PII Tools is finally here. Generate new, AI-driven PDFs from original files with all personal data automatically blacked out – this is the future of genuinely efficient data redaction. What Does Data Redaction Mean At PII Tools, we’ve made it our calling to create AI-driven software to maximize data discovery and the remediation of … Read More





