Part 2 of 3: Reducing Data Leaks + Data Security Awareness Employees are responsible for 90% of all data breaches! That’s why Part 1 of this mini-series discusses the basics of data leaks, while Part 2 tackles the source of the problem: Human error. This is the last employee training you’ll ever need! 1. Intro to Information Security All employees … Read More
Data Loss Prevention: 3 Basic Steps to Data Protection
$4.44 million. That’s the average cost of a data loss instance in 2025. Unless you’ve got that kind of cash just lying around, taking steps toward Data Loss Prevention will be your best option. But who’s keeping your data safe? Intro to Data Loss Prevention Before you get anywhere near avoiding that 4-million-dollar “hit” to the yearly budget, you first … Read More
Fast & Accurate Data Breach Resolution
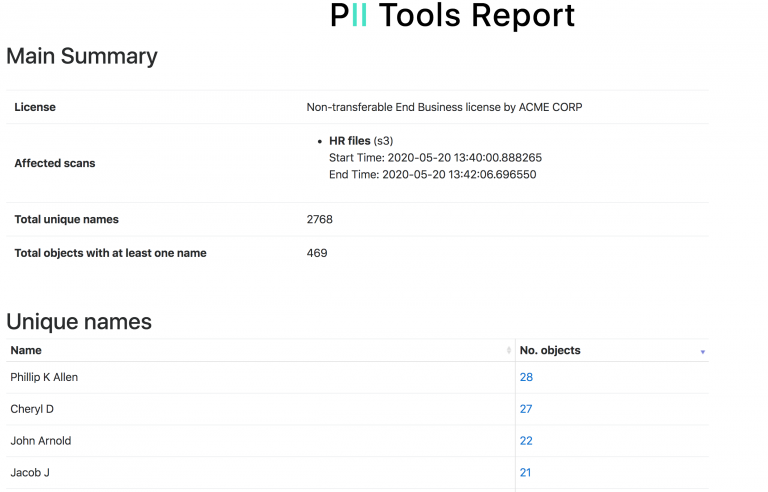
You’ve suffered a data leak, and the clock’s already ticking. Oh, and it’s a large dataset, too. Where do you even start to locate every single instance of PII involved? Let’s get into it! Breach Incident Scanner Discovering leaked sensitive information and PII by hand is completely unrealistic for large datasets, so automated solutions like PII Tools come in handy. … Read More
Employee Training: PII Security and Data Management

The vast majority of mistakes that lead to breached data are accidental and caused by human error. What are the best ways to train employees to handle PII and build unshakable security awareness? Accidental Data Leaks Humans are imperfect. Even if you have 20+ years of experience in data security and breach prevention, you can still slip up and make … Read More
Preparing for a Data Breach – Are You Ready?
“Hope for the best, prepare for the worst.” With billions of data records stolen and lost every year, these words ring truer every day. But can you ever really be “prepared” for a data breach, or are we all just waiting for the second shoe to drop? Inevitability Regarding data breaches, it seems the questions are more “when will the … Read More
Exclude PII / PCI / PHI From a Breach Report
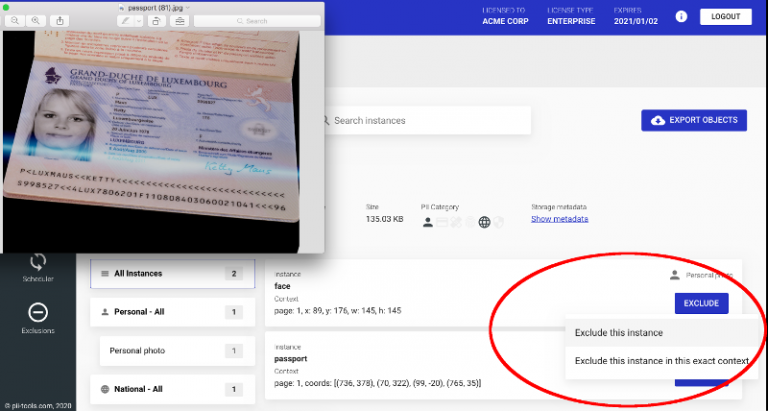
When responding to a breach incident, having a clear idea who’s affected and how is a matter of urgency. Manual discovery of PII information is tedious and costly, so automated solutions come in handy. But how to deal with false positives? PII Exclusions One typical task during a data review is removing unwanted data instances. PII Tools already automates PII … Read More





