All it takes is one request, and poof… everything’s gone. What is the California Delete Act Sunny California has long been a leader in surfing, movie-making, and… consumer privacy? That’s right, and as of Jan. 1, 2024, the California Privacy Protection Agency (CCPA) is set to enforce a new law that could completely change data storage as we know it. … Read More
Person Cards® – The Holy Grail of Data Discovery
By 2025, the global datasphere is estimated to hold as much as 175 zettabytes of data. How can companies today possibly have a chance to organize that much information? The answer: Person Cards®. More Data, More Problems 175 zettabytes of data worldwide? Considering a single zettabyte is equal to a trillion gigabytes (yes, with a ‘T’), the actual amount of … Read More
What’s new: NIST Cybersecurity Framework 2.0
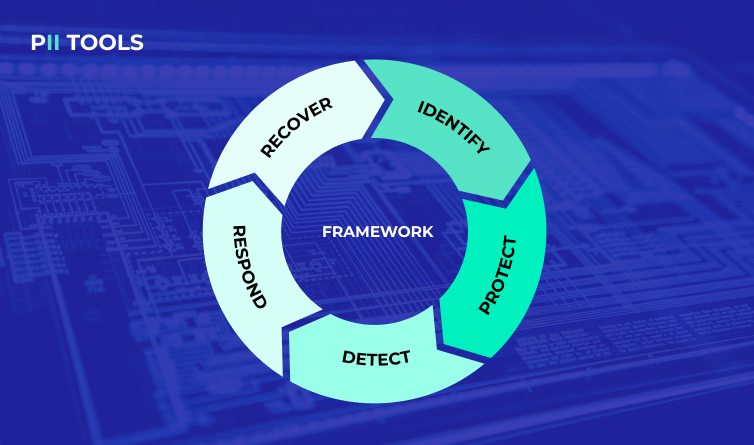
It’s been almost 10 years since the original CSF 1.0 was issued, and so much has changed since. What new guidelines does CSF 2.0 bring, and how can you implement them today? Remembering CSF 1.0 Before we get to the new stuff, let’s run through a quick recap of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) … Read More
Top Features to Look For When Comparing Data Discovery Tools

Comparing features of data discovery tools is a complex task that can easily turn into a nightmare. Here is a shortlist of the most important features to take into account when selecting the best option for your business, so you won’t get caught in the net of unimportant details and technical specifications. The main purpose of data discovery tools is … Read More
Exercising Your Right to Be Forgotten

Some people want to be remembered forever. And yet, the idea of being “completely forgotten” in today’s data-driven world might be just as appealing. So, what exactly is the Right to Be Forgotten, and how can you apply it right now? More Than A Modern Fantasy Imagine a world where you can fully disconnect, have every single instance of your … Read More
Using PII Tools on a Daily Basis

As every GRC team member knows all too well, manually sifting through the company’s seemingly infinite TB of stored data is a full-time job (or a waste of time). But now, with advances in AI-driven data discovery, what does the day of an average PII Tools user actually like? Streamlining Data Discovery The day-to-day mission of any GRC team (Governance, … Read More
The AI Revolution in Personal Data Discovery and Protection

Did somebody say AI? The world is currently experiencing a revolution of new and (slightly) worrying technology. With different implications in every field, how are personal data discovery and protection currently evolving? The Revolution Is Now Artificial intelligence, machine learning, ChatGPT, Stable Diffusion… good luck even spending five minutes online without being bombarded by these topics on every podcast, article, … Read More
Preparing for a Data Breach – Are You Ready?
“Hope for the best, prepare for the worst.” With billions of data records stolen and lost every year, these words ring truer every day. But can you ever really be “prepared” for a data breach, or are we all just waiting for the second shoe to drop? Inevitability Regarding data breaches, it seems the questions are more “when will the … Read More
A Simple Breakdown of CCPA Compliance
The CCPA can be as complicated as it is far-reaching. And with California’s population of nearly 40 million, compliance is a must for many international companies. So, what exactly is the CCPA all about, how does it pertain to you, and what does compliance mean for your business? The CCPA Explained As of Jan. 1, 2020, a new data privacy … Read More
The New CPRA Umbrella Covers HR Data
Is it too early to start talking about New Year’s resolutions? Well, come January 1st, 2023, the only goal for many HR departments will be unraveling the CPRA’s latest privacy law on HR data. So, will you wait until after Christmas to finally see what all the fuss is about, or will you dive into the CPRA deep end while … Read More





