Part 3 of 3: Data Leak Prevention in 10 Easy Steps
The 3rd and final article in this mini-series. Part 1 taught us the basics of data breach prevention, while Part 2 provided the ideal employee training. Now, how many of these data security points can you check off?
Data Security Health
Is data leak prevention a priority in your business? Complete the following data security checklist and measure the health of your PII.
- 1. Data Classification: My company clearly defines Personally Identifiable Information (PII) and classifies it as sensitive data, protected data, health-related data, financial data, standard data, etc.
- 2. Regulatory Compliance: My company takes data regulatory compliance seriously, and all stored data is compliant with the relevant guidelines (GDPR, HIPAA, PCI DSS, GLBA, etc.).
- 3. Strong Access Controls: My company enforces the right to access data at various levels of sensitivity, including frequent reviews of data authorization and access privileges (including the regular removal of old accounts).
- 4. Multi-Factor Authentication: Alongside secure access controls, my company also uses multi-factor authentication for login and accessing data storages, corporate data, client data, etc.
- 5. Secure Cloud or On-Prem Storage: All data in my company is stored securely on the Cloud or locally on-premises (i.e., no sensitive data or PII stored in undocumented, unsecure locations).
- 6. Sensitive Data Discovery Software: My company deploys sensitive data discovery software to discover, analyze, and remediate sensitive data any and everywhere.
- 7. Monitor & Log Data Activity: At my company, we always track file transfers, downloads, uploads, and email forwarding. We also set alerts for unusual or high-volume data access.
- 8. Protection from AI: My company avoids leaking PII or sensitive data when using third-party AI tools by scanning and relocating all data BEFORE running it through AI models.
- 9. Employee Training and Awareness: My company holds regular employee training sessions on sensitive data, how to prevent data leaks, and our policies on data handling, access, modern cyberattack strategies, etc.
- 10. Incident Response: Even despite our best efforts, data can still be leaked. That’s why everyone at my company is fully aware of our incident response policy and how and when to report suspicious behavior.
Results
So, how’d your company fare? In an ideal world, you’d be able to check off all 10 points in this list, thus guaranteeing your sensitive data is as protected from potential data leaks as possible.
But if a few points are missing, then there’s never been a better time to remedy them than right now. And if you need help with anything from understanding PII to regulatory compliance and breach incident management, be sure to check out PII Tools.
Then you can score a full 10 out of 10 on this Data Leak Prevention Checklist in no time!
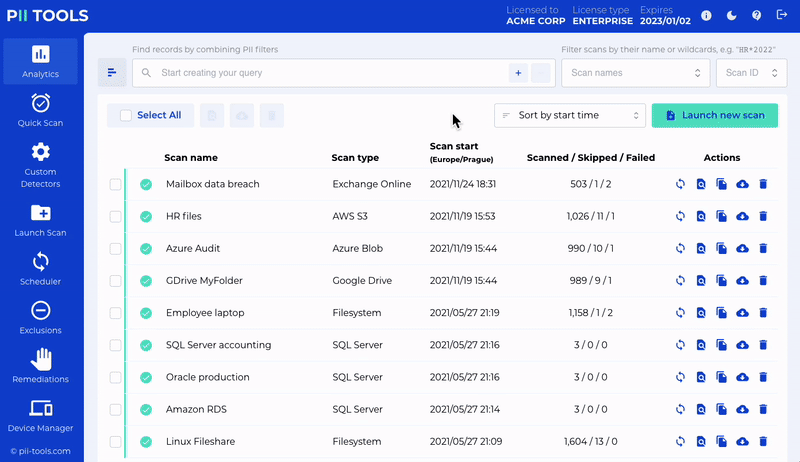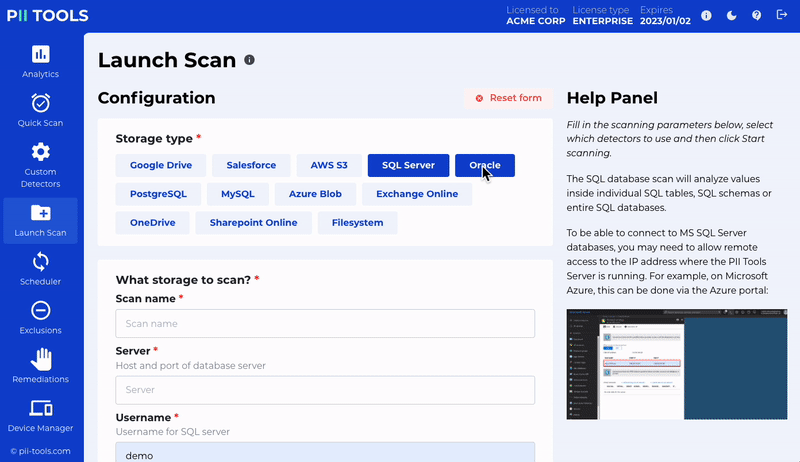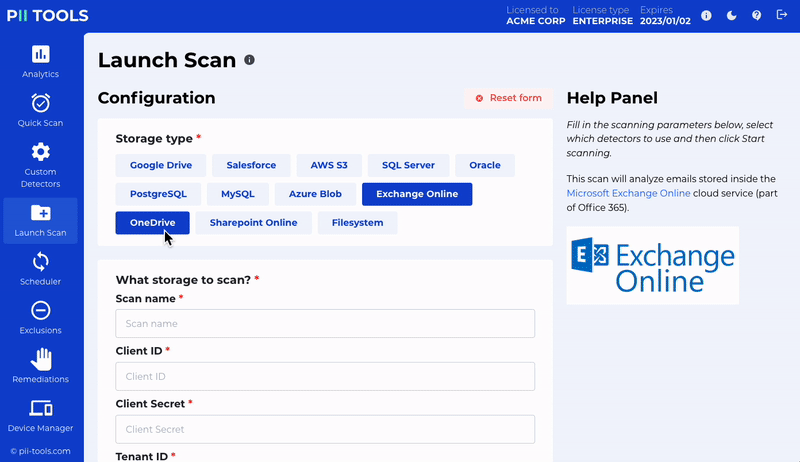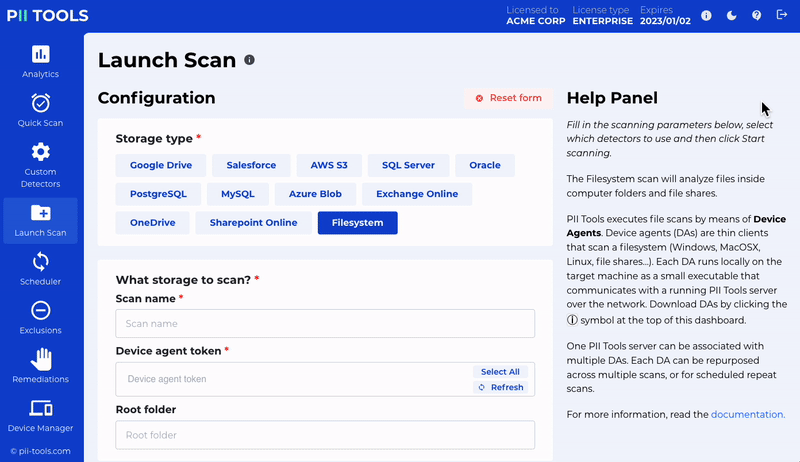
Get Hands-on Experience with PII Tools with a 100% Free Demo!