Fines, penalties, fees… Oh my! But by mismanaging PII, we stand to lose more than just money. It’s time to look at what’s at stake and learn how to avoid these numerous pitfalls. It’s All About the Money Unfortunately, for many people and companies, the only time they actually start to care is the moment their wallet gets involved. Taking … Read More
How to: Protecting ePHI
The average healthcare breach exposes 3+ million private patient records. What are you doing to discover, store, and protect ePHI? Why the ‘e’ in ‘ePHI’? HIPAA, PHI, PII, GDPR, ePHI… Where would we be without our acronyms? If you’re interested in protecting ePHI, it’s safe to say none of these are entirely new to you. The most important to our … Read More
How To: Understanding RoPA and Achieving Compliance
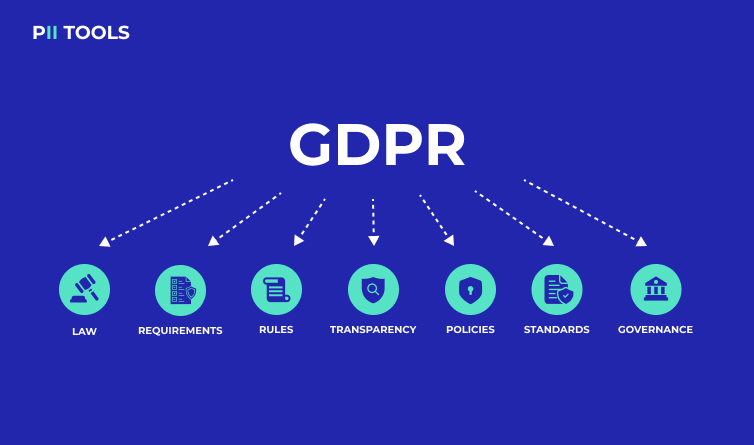
Did you know the GDPR has 99 different articles and over 250 pages? You’ll likely never know each provision individually, but there’s at least one article worth paying extra attention to. Meet Article 30: RoPA. The GDPR If you’re the kind of person interested in articles about sensitive data and compliance, we sure hope you’re already well aware of the … Read More
Regular Audits: Do You Really Need Them?
There’s nothing worse than wasting time and money, so is there any benefit to reviewing the data you store? Well, unless you want to be like the kid who never studies for tests, regular audits may be the only thing keeping you out of the principal’s office. To Audit or Not to Audit? By this point, I would hope none … Read More
Do They Even Matter?—The 3 Largest GDPR Fines To Date
For years now, the GDPR has been criticized for offering more bark than bite. As the fines stand, many mega-companies like Amazon and Google are simply getting away without a scratch. All this has left us wondering, what are the 3 biggest GDPR fines so far, and do any of them actually matter? Knowing the GDPR Before we get to … Read More
PII Examples
Below you’ll find a list of made up PII examples to help you better understand what PII looks like in the real world. You’ll also find a downloadable file attached to each point with specified (fake) PII examples you can then use to test your discovery solution. Enjoy. PII includes, but is not limited to: Names: Full name, First name, … Read More
How To: Understanding HIPAA Compliance
For many readers, when they hear the words “the Health Insurance Portability and Accountability Act (HIPAA)”, their eyelids immediately start to droop. But I’m sure getting slapped with an annual $1.5 million fine would wake them up! Whether you’re the one handling the data or the actual patient looking to protect your rights, it’s time to become a HIPAA expert … Read More
How to Identify Leaked Data
A data breach can happen to anyone at any time. Although there are many steps in responding to such a breach, the first is actually locating the data in question. If you’ve suffered a breach of information, how do you identify all affected parties? Detecting the Leak There are multiple ways you can tell you’re dealing with a data breach, … Read More