The new year is already upon us, and it comes stocked with sweeping PII protection and data security updates. These are the TOP 3 data regulation changes you need to know for your business in 2026 and beyond! #1. The AI Act Starting in the European Union, we already have the enforcement date for The AI Act: August 2, 2026. … Read More
Self-Hosted Software vs SaaS

Your corporate data is safest when kept within self-hosted software over SaaS. But are there any other advantages, and how can you leverage them? Time to see how self-hosting compares against SaaS! Self-Hosted Software or SaaS? Companies that opt to secure their sensitive data within self-hosted software benefit in many ways compared to Software-as-a-Service (SaaS) options, even if these appear … Read More
Securing Data Against AI Applications, Part II

AI Data Protector safeguards your sensitive data and company information from 3rd-party AI models. Increase efficiency AND keep your private data private!
Securing Data Against AI Applications, Part I

Use AI to discover and remediate at-risk information with an AI Data Protector. Increase security, raise efficiency, and avoid potential data disasters!
The Complete Guide to PII – Part 3

Better understand PII and how it differs from Personal Data. Complete with helpful PII examples, free to download. Part 2 of 3.
The Complete Guide to PII – Part 2

Better understand PII and how it differs from Personal Data. Complete with helpful PII examples, free to download. Part 2 of 3.
The Complete Guide to PII – Part 1

Over 402 million terabytes of data are generated every day. And giant companies like Google and Meta can’t wait to collect and sell as much as possible. The first step to protecting your personal data is identifying it. This three-part mini-series will take you through the ins and outs of PII and help you safeguard what’s yours. PII Basics PII … Read More
10 Reasons YOU Should Be Using PII Tools Right Now!

There are plenty of reasons to use PII Tools Data Discovery Software, but we’ve managed to narrow them down to our TOP 10. Let’s check them out! #1 Automated Scanning for 400+ File Formats The more daily tasks you can fully automate, the more time you can focus on what actually makes your company money. And with over 400 compatible … Read More
What’s new: NIST Cybersecurity Framework 2.0
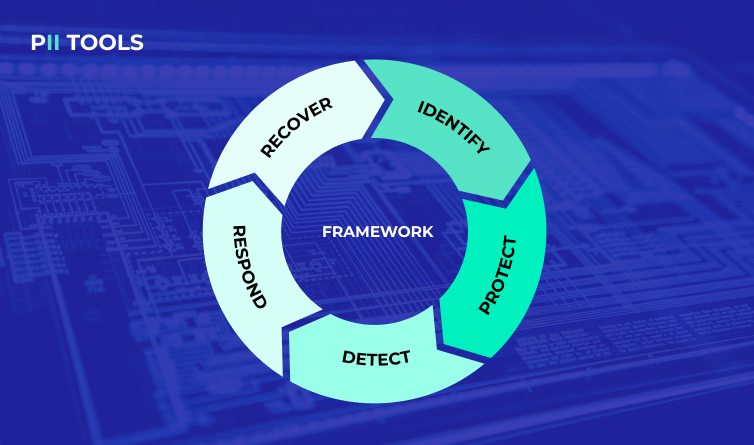
It’s been almost 10 years since the original CSF 1.0 was issued, and so much has changed since. What new guidelines does CSF 2.0 bring, and how can you implement them today? Remembering CSF 1.0 Before we get to the new stuff, let’s run through a quick recap of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) … Read More
Learning the Difference Between Data Privacy and Data Security
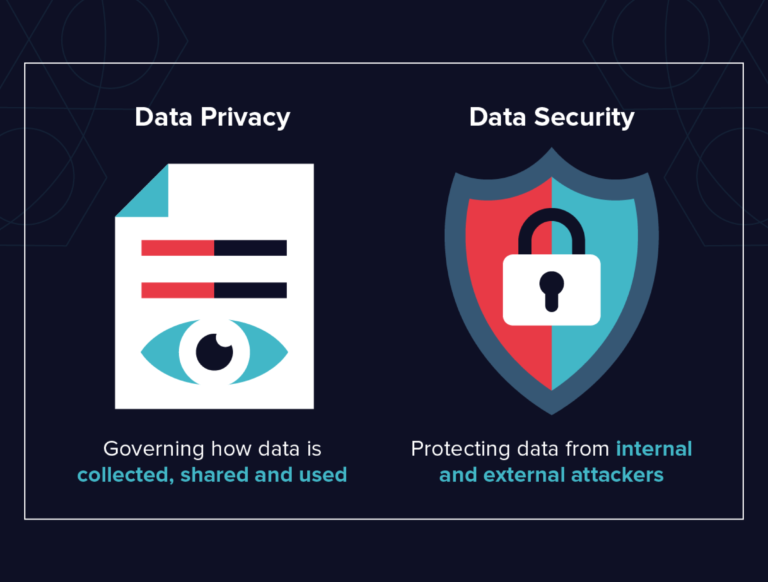
Companies often believe that by securing their sensitive data, they automatically comply with the requirements of various data privacy regulations (GDPR, HIPAA, CCPA, etc.). Unfortunately, this is not the case. Let’s take a look at these two terms to understand the difference and make sure you adhere to both. It’s a bad habit to treat data security and data privacy … Read More