The best way to safeguard sensitive data is to keep it out of sight — and out of reach.
The 3rd and final section in this 3-part mini-series explores Data Redaction and the irreversible role it plays in PII protection. Let’s get into it.
What is Data Redaction?
Ever see a spy movie featuring ‘classified’ files? Pages and pages of information with all the juicy bits seemingly blacked out with a marker? For once, Hollywood’s not that far off.
Data redaction also exists outside the silverscreen, and it’s not just for shady government documents.
PII or data redaction is the irreversible process of blacking out or removing information that is personally identifiable, sensitive, confidential, or otherwise classified – typically information coming from scanned documents, images, and PDFs.
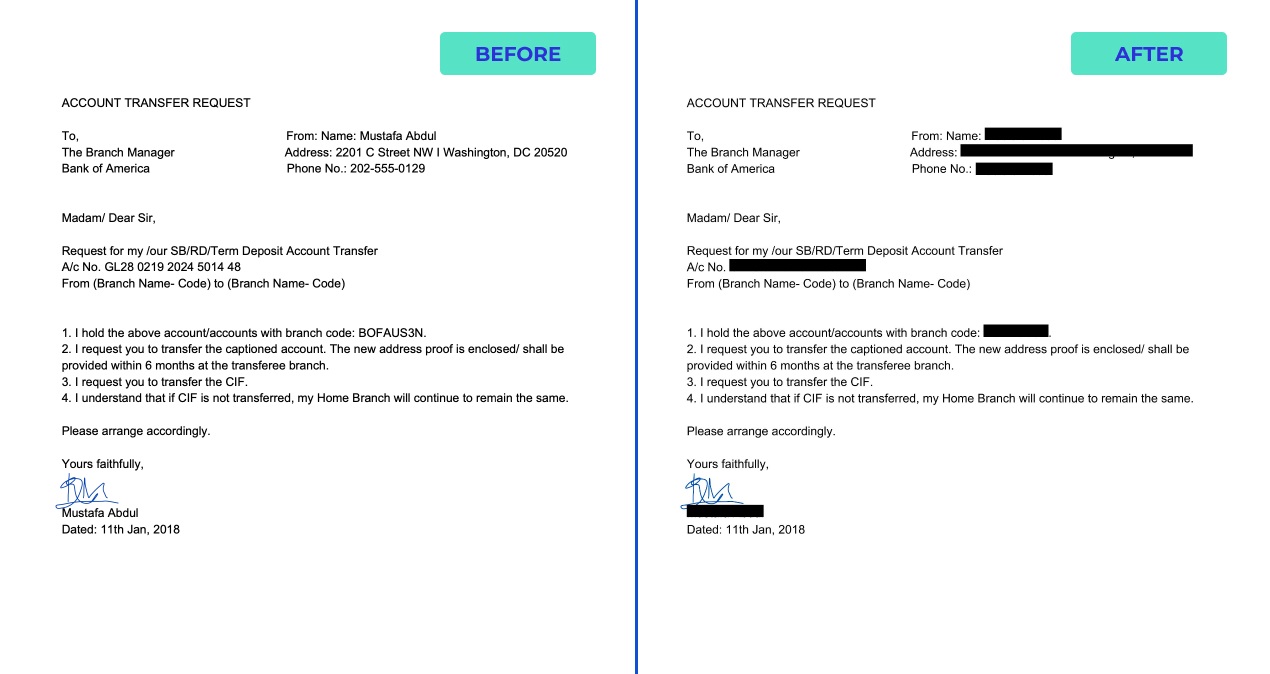
The image below provides a visual representation of how everyday businesses may choose to protect their corporate or client at-risk data by simply blocking it from sight.
Why Choose Data Redaction?
As previously mentioned in this mini-series, each type of data anonymization is most useful in specific scenarios.
Data redaction is irreversible. Choosing to redact certain parts of a document means the full, unredacted original can never be recovered. In that case, you'd better hope you’ve got copies stored somewhere safe or are fine with losing that data forever.
The most common reason for choosing data redaction over data masking, data de-identification, and other, less-permanent options (encryption, tokenization, etc.) is with the following goal in mind: Completely remove certain pieces of sensitive information so the remaining text can be released.
Possible use cases include redacting PII from a helpful document before emailing it to otherwise unauthorized employees or releasing public statements to the media or journalists without exposing at-risk data.
Data Redaction Example

The sample email above perfectly simulates how proper data redaction should look. Readers don’t need any special permission to read the email. In fact, no PII would be lost even if this email were leaked or stolen.
However, the email still provides useful context, meaning it could be used by unathorized employees without risking regulatory non-compliance. And it’s also worth noting that all kinds of data can be redacted.
Where other options, like Data Masking, for instance, are mainly used to replace at-risk data (names, addresses, credit card numbers, etc.), data redaction is great for blocking out entire sections. For instance, when a client goes into detail about their medical issues and symptoms (something protected by HIPAA).
Sensitive Data Discovery
That concludes our 3-piece mini-series on the TOP methods of data anonymization. Also, be sure to check out the first two articles if you haven’t: Data De-Identification and Data Masking.
But before you can start protecting your stored and at-risk data, you’ll first need to find it. That’s where the PII Tools sensitive data discovery software comes in. This effective tool helps you locate and remediate PII, PCI, and PHI across all your digital assets. The perfect assistant for effective data anonymization.
Loads of At-Risk Data to Redact? Start with Sensitive Data Discovery with PII Tools!