Companies often believe that by securing their sensitive data, they automatically comply with the requirements of various data privacy regulations (GDPR, HIPAA, CCPA, etc.). Unfortunately, this is not the case. Let’s take a look at these two terms to understand the difference and make sure you adhere to both.
It’s a bad habit to treat data security and data privacy as synonyms. This confusion usually goes hand in hand with a lack of knowledge and lack of tooling to cover both of these fundamental aspects of data management. A failure to comply with the legal obligations may have significant and unpleasant consequences for your business. Such a situation includes a loss of reputation, customers, business, and various sanctions from the regulatory authorities.
According to the European GDPR law, if a company doesn’t comply with privacy regulations, it may be fined up to €20 million or 4% of the business’s total annual worldwide turnover.
What’s the difference between data privacy and data security?
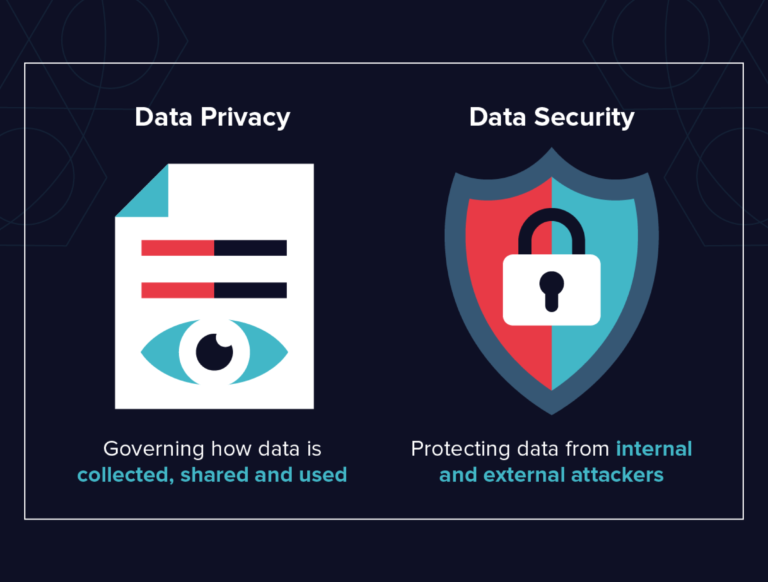
Data privacy is part of a broader range of data protection measures and deals with the secure processing, storage, and management of sensitive data. It determines how sensitive data is collected, shared, and used (privacy rights) with an individual’s consent (data owner).
Data security protects sensitive data from external attackers and internal insiders who want to seize it without proper authorization. The following table simplifies the basic differences between personal data privacy and data security.
Data Privacy
- Ensures the appropriate processing, storage, and use of personal data and defines who has the right to authorized access.
- Means the rights of individuals concerning their personal data.
- Is more about securing an individual’s personal information.
- Stays in the hands of individuals who can decide how their data may be used or shared.
- The goal is to ensure that data isn’t shared or sold without the consent of the individual.
- Is covered by regulations consisting of policies and procedures that help manage data.
- Cannot be achieved without data security.
Data Security
- Aims to protect sensitive data from unauthorized access and use.
- Is a matter of protecting data integrity and ensuring the accuracy, reliability, and availability of data to authorized parties.
- Applies to any type of sensitive data, whether personal, financial, or any other confidential information.
- Is the responsibility of the organizations that handle and use the data.
- The goal is to secure information from hackers.
- Is a mechanism to secure sensitive data against hacking or theft.
- Doesn’t necessarily involve the protection of personal data.
Failure to protect the data might be fatal to your business
Being a business owner automatically carries the responsibility of keeping your data safe and, as a result, protecting the data of your employees, customers, partners, and any other contacts. Without proper action, several negative scenarios may occur.
Cimcor states that 60% of small companies go out of business within six months of falling victim to a data breach or cyberattack.
Not having appropriate security measures in place, your business is at risk of violating regulatory requirements. Here it pays to keep in mind that your data is your most important asset, in addition to your employees. Companies often underestimate this fact: “We’ve never had a breach, so we’re not in danger, right?”. This is a great delusion. In the event of compromised data security and data privacy, the company will most likely suffer dramatically and may eventually even cease to exist. The shutdown of Jumpshot serves as a prime example.
Tools that can help you with data privacy and security
Every business is expected to have a well-thought-out scenario for maintaining the privacy and security of its data. Popular tools that can help you in this endeavor include password managers, secure email services, end-to-end message encryption, privacy-respecting browsers, web servers, search engines that don’t track your activity, file encryption software, tracking blockers, and more. Such tools increase the privacy and security of your company’s data on a personal level. Meaning it’s up to your employees to use these tools and follow all company policies.
Beyond that, businesses use more complex tools to automatically secure their collected data, such as anti-malware, anti-virus, access management security, data and event management, data loss prevention, data masking software, and digital inventory scanning tools such as PII Tools.
IBM research has shown that organizations that don’t deploy proper security AI and automation have experienced security breach costs that were up to USD 3.81 million higher than those in organizations with fully deployed security AI and automation.
The bottom line
Although data privacy and data security ultimately differ, one thing should be clear: There can’t be data privacy without data security. As the value and volume of data grow exponentially, data privacy has become a problem at the board of directors’ level. It’s also a significant source of competitive advantage, which is particularly important alongside the requirement of regulatory compliance. People are becoming more sensitive and aware of their personal data so it's more and more important for them to make sure the company they buy from respects and protects their privacy.
For all industries, regulatory compliance is a must. Finance, insurance, healthcare, retail, the public sector, education, and pharmaceuticals, to name a few, have spent considerable resources over the last few years to ensure that they do not infringe any relevant regulations. It’s already certain that soon, this obligation won’t be avoided by any business sector.
Interested in discovering sensitive data across all your storages? Try out our free demo today!