A data breach can happen to anyone at any time. Although there are many steps in responding to such a breach, the first is actually locating the data in question. If you’ve suffered a breach of information, how do you identify all affected parties?
Detecting the Leak
There are multiple ways you can tell you’re dealing with a data breach, attempted or complete. These are the more common giveaways, just to name a few:
- Policy alerts and logs full of failed access attempts.
- Bounced emails with suspicious content.
- Multiple failed login attempts from an unfamiliar remote system; unfamiliar logon notifications.
Another probable place to start is with the company’s employees. Employee negligence is responsible for more data leaks than any other factor. To learn more on how to combat employee negligence, read our article on the subject.
Identifying the Leaked Data
Once you’ve realized a data leak has taken place, it’s time to identify the actual information that was lost. Depending on the size of your company, you may already employ the specialist needed to run the software and locate the leak. This position can be filled by your DPO (Data Protection Officer), in-house audit specialist, or breach incident investigator.
Next comes the SDDT (sensitive data discovery tool). It’s safe to say the investigator doesn’t have the time or capabilities to manually go through every company file, emails or database. The investigator implements the SDDT software in definite areas where they expect the data was leaked. This depends on the specifics of each data breach.
Example: If you’re investigating a data breach you believe to be the result of a phishing attack, you use the SDDT to scan the specified mailboxes of the employees who may have responded to the nefarious email.

Sensitive Data Discovery Tools
SDDTs come with many inherent advantages that make the investigator’s job that much easier. For instance, a quality SDDT can scan all types of file formats on its search for leaked sensitive data: local or cloud-based files, databases, emails, email attachments, structured and unstructured.
It should have no problem sifting through any of the popular programs and file formats. Office 365, Linux, OneDrive, Oracle, Windows File Share, a good SDDT can scan it all. Also, the investigator is sure to appreciate the ability to identify leaked data in PDFs, pictures, and rotated images with the use of OCR and facial-recognition technology. Scanning only the text is not enough because vital information may go undetected in media files.
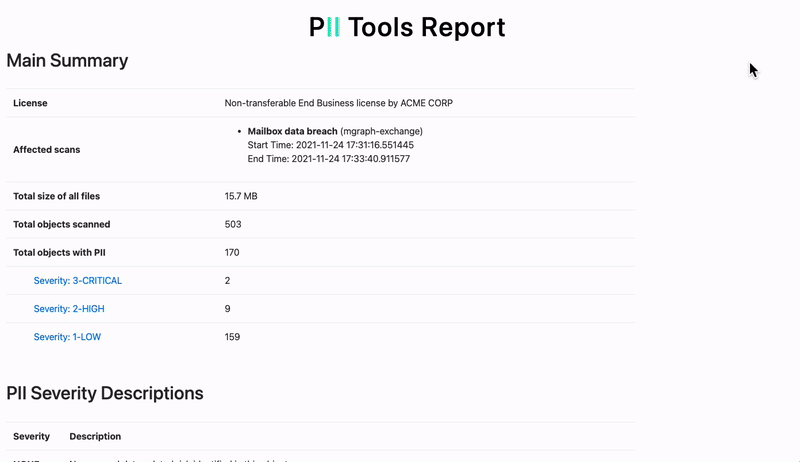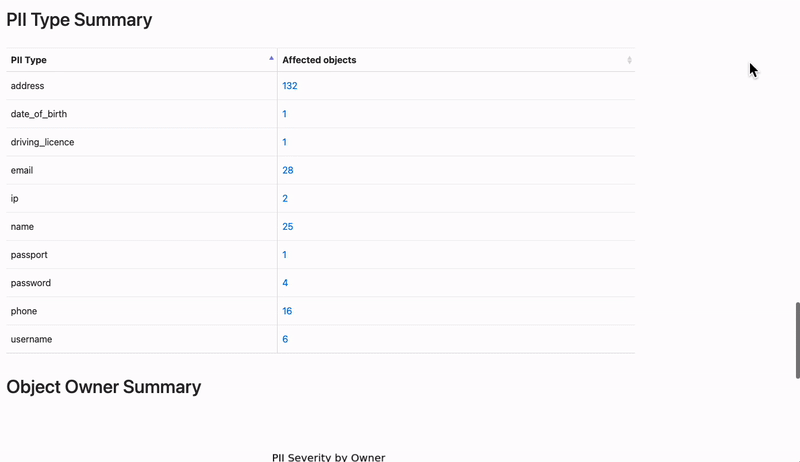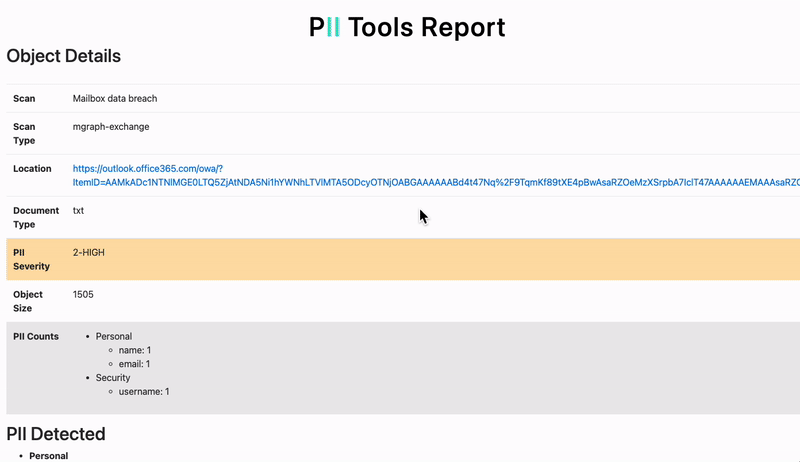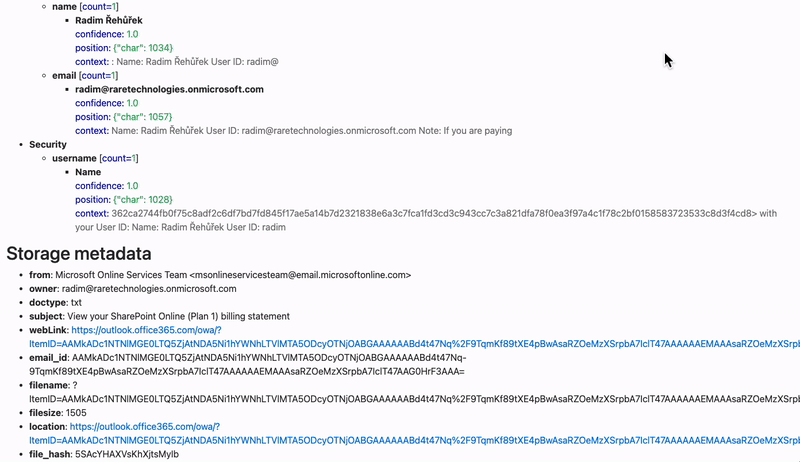
With this kind of software at hand, the auditor, DPO, or breach incident investigator will find out exactly WHAT data was leaked and WHOSE data was affected. This makes a huge difference. Now you can know if the leaked data was one of the following:
- Sensitive data
- Private data
- Customer/client health information
- Credit card information
- Corporate confidential data
Obviously, knowing the distinction of the data leaked will help the company to follow the guidelines of whichever mandatory regulation that data pertains to (GDPR, CCPA, HIPAA, PCI-DSS, LGPD, etc.).
Protection Going Forward
Once you’ve identified the leaked data, the company must notify all affected parties and regulatory bodies. Then it’s time to start the clean-up process. Hopefully, part of that process includes patching the holes that led to the leak in the first place. That may include anything from proper employee negligence training, updating the internal security guidelines, to implementing a higher level data security strategy.
One tool that helps companies correctly organize their sensitive data is the SDDT PII Tools. PII Tools is data discovery software that does everything mentioned above and more. It’s the precise tool the breach incident investigator would want to use when searching for leaked data. Learn more of what it can do for you by reading What Are Sensitive Data Discovery Tools and How Do They Work?
Effectively Identify Leaked Data Fast with PII Tools’ Data Leak Management.




