With more tools at our disposal than ever before, how can you use artificial intelligence and machine learning to handle PII and sensitive data effectively? Modern AI & Machine Learning At this point, artificial intelligence (AI) and machine learning (ML) don’t need much of an introduction. Our phones, cars, televisions… even some smart refrigerators come equipped with AI and ML … Read More
The Evolution of PII Protection: From Paper to Digital

PII has come a long way in a relatively short time, yet protecting it fully is like trying to shield a moving target. But sometimes the best way to choose a path forward is to peek at the past and learn from its evolution. Humble Beginnings It’s hard to think about PII, or rather Personally Identifiable Information, without also imaging … Read More
Data Redaction: The Essential Guide to Protecting Sensitive Data
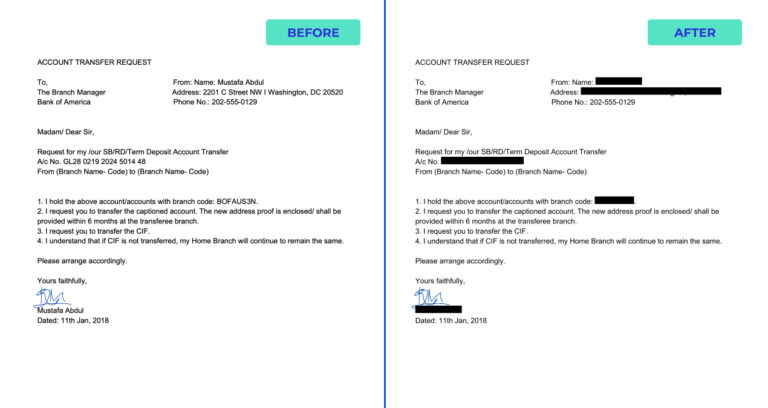
The long-awaited data redaction feature by PII Tools is finally here. Generate new, AI-driven PDFs from original files with all personal data automatically blacked out – this is the future of genuinely efficient data redaction. What Does Data Redaction Mean At PII Tools, we’ve made it our calling to create AI-driven software to maximize data discovery and the remediation of … Read More
The California Delete Act: How it affects organizations

All it takes is one request, and poof… everything’s gone. What is the California Delete Act Sunny California has long been a leader in surfing, movie-making, and… consumer privacy? That’s right, and as of Jan. 1, 2024, the California Privacy Protection Agency (CCPA) is set to enforce a new law that could completely change data storage as we know it. … Read More
Top Features to Look For When Comparing Data Discovery Tools

Comparing features of data discovery tools is a complex task that can easily turn into a nightmare. Here is a shortlist of the most important features to take into account when selecting the best option for your business, so you won’t get caught in the net of unimportant details and technical specifications. The main purpose of data discovery tools is … Read More
Exercising Your Right to Be Forgotten

Some people want to be remembered forever. And yet, the idea of being “completely forgotten” in today’s data-driven world might be just as appealing. So, what exactly is the Right to Be Forgotten, and how can you apply it right now? More Than A Modern Fantasy Imagine a world where you can fully disconnect, have every single instance of your … Read More
Using PII Tools on a Daily Basis

As every GRC team member knows all too well, manually sifting through the company’s seemingly infinite TB of stored data is a full-time job (or a waste of time). But now, with advances in AI-driven data discovery, what does the day of an average PII Tools user actually like? Streamlining Data Discovery The day-to-day mission of any GRC team (Governance, … Read More
The AI Revolution in Personal Data Discovery and Protection

Did somebody say AI? The world is currently experiencing a revolution of new and (slightly) worrying technology. With different implications in every field, how are personal data discovery and protection currently evolving? The Revolution Is Now Artificial intelligence, machine learning, ChatGPT, Stable Diffusion… good luck even spending five minutes online without being bombarded by these topics on every podcast, article, … Read More
Do They Even Matter?—The 3 Largest GDPR Fines To Date
For years now, the GDPR has been criticized for offering more bark than bite. As the fines stand, many mega-companies like Amazon and Google are simply getting away without a scratch. All this has left us wondering, what are the 3 biggest GDPR fines so far, and do any of them actually matter? Knowing the GDPR Before we get to … Read More
Scanning Office 365 for sensitive PII information

Discover personal & sensitive data inside Office 365 accounts and remediate it. This includes both structured and unstructured data in Microsoft OneDrive, Microsoft Exchange Online, and Sharepoint Online. What does “support Office 365” mean? With PII Tools, you directly find, review, and remediate personal and sensitive information in documents, emails, and tables shared within your company’s Office 365 accounts. No … Read More





