Is it too early to start talking about New Year’s resolutions? Well, come January 1st, 2023, the only goal for many HR departments will be unraveling the CPRA’s latest privacy law on HR data. So, will you wait until after Christmas to finally see what all the fuss is about, or will you dive into the CPRA deep end while … Read More
Regular Audits: Do You Really Need Them?

There’s nothing worse than wasting time and money, so is there any benefit to reviewing the data you store? Well, unless you want to be like the kid who never studies for tests, regular audits may be the only thing keeping you out of the principal’s office. To Audit or Not to Audit? By this point, I would hope none … Read More
How to remediate PII?
Within the world of sensitive data discovery, there are many roads you can take to remain compliant to mandatory regulations. Unfortunately, many of these roads can leave you with more questions than answers. If you’re looking for a simpler route to protect your company’s data, SaaS is right for you. What is SaaS? Pronounced /sæs/, SaaS stands for Software as … Read More
Creating Data Leak Reports
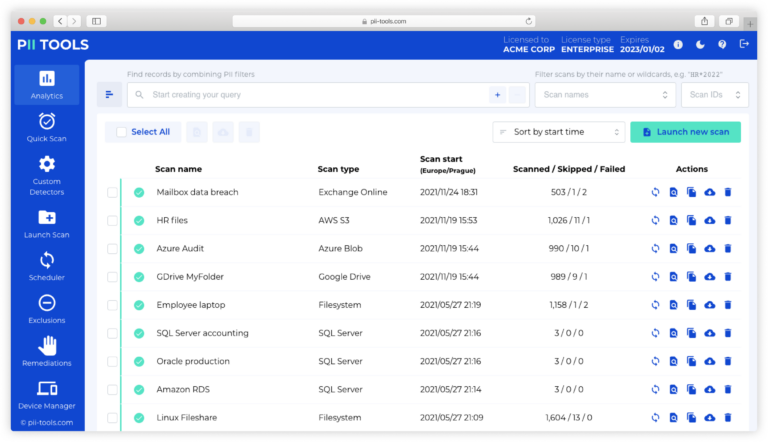
In this guide, you will learn how to create data leak reports with PII Tools. Launching a scan The first step towards the successful management of any data leak is to identify what was in the breached data. Open your PII Tools and, on the left side, select Launch Scan. If you performed the scan already, skip to the next … Read More
Learning the Difference Between Data Privacy and Data Security
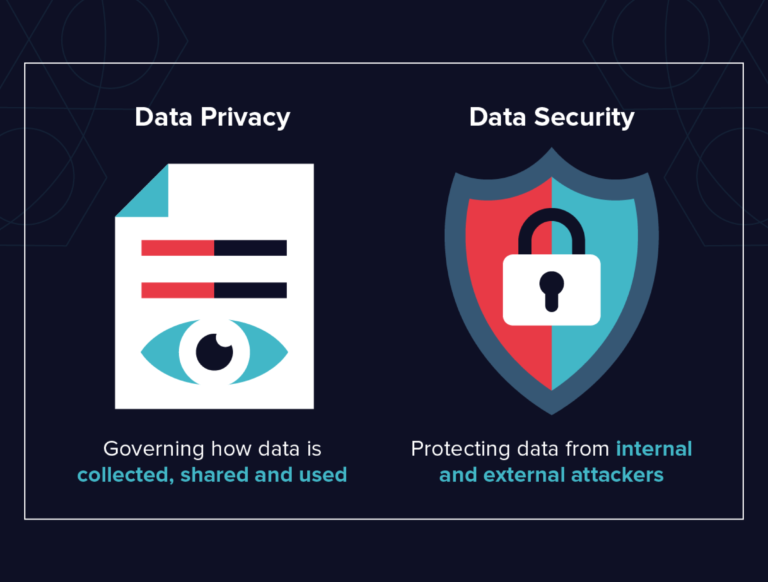
Companies often believe that by securing their sensitive data, they automatically comply with the requirements of various data privacy regulations (GDPR, HIPAA, CCPA, etc.). Unfortunately, this is not the case. Let’s take a look at these two terms to understand the difference and make sure you adhere to both. It’s a bad habit to treat data security and data privacy … Read More
NEW PII Drill-Down Reports – Export for Better PII Insights
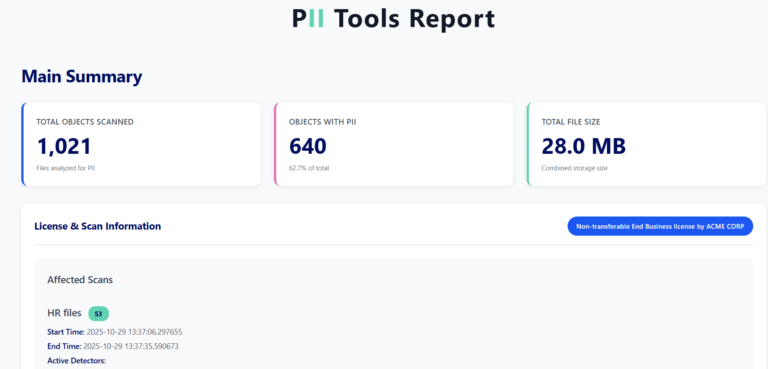
In the latest February release (version 2.4.0), we combined Personal Data Analytics search with dynamic HTML report generation to make GDPR compliance and auditing easier. PII Tools already supports dynamic PII Analytics queries to locate personal, sensitive, and intimate information. It also generates drill-down PII audit reports for completed data scans. In the latest release, we combined these two capabilities. You can … Read More
Personal Data Analytics
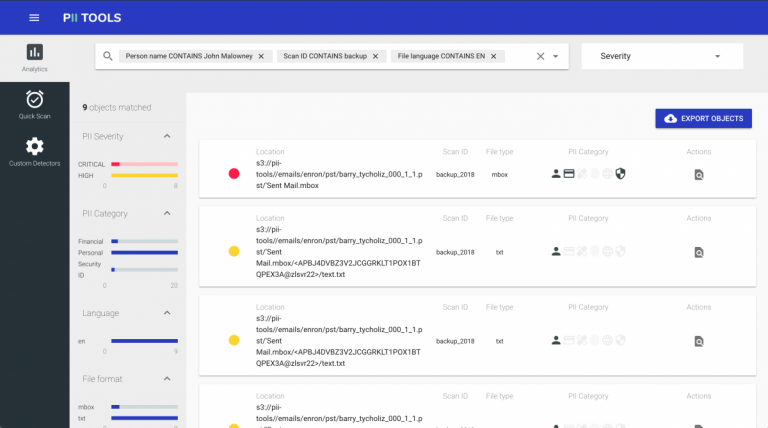
The latest 2.0 release of PII Tools brings a brand new SAR dashboard, allowing targeted personal data search, filtering and analytics. Search for all files on John that contain any financial information, while restricting the results to CRITICAL severity only. Locating Information for Data Subject Access Requests What if you want to find all data related to a specific person … Read More
- Page 2 of 2
- 1
- 2




