Masking sensitive data is one of the most effective methods to protect PII, however, not every technique is created equal. Learn the ins and outs of PII Masking and which form works best for you. What is PII Masking? Data or PII masking is a non-reversible transformation process that “masks” sensitive data by partially or fully replacing characters with a … Read More
Data Loss Prevention: 3 Basic Steps to Data Protection
$4.44 million. That’s the average cost of a data loss instance in 2025. Unless you’ve got that kind of cash just lying around, taking steps toward Data Loss Prevention will be your best option. But who’s keeping your data safe? Intro to Data Loss Prevention Before you get anywhere near avoiding that 4-million-dollar “hit” to the yearly budget, you first … Read More
Scan Microsoft 365 Copilot for Sensitive Data & PII

Discover and remediate personal and sensitive data inside Microsoft 365 Copilot accounts. This includes both structured and unstructured data in Microsoft OneDrive, Microsoft Exchange Online, and SharePoint Online. Full Microsoft 365 Copilot Support Microsoft’s AI chatbot, known as Copilot, recently became an integral part of Office 365. The official name is now Microsoft 365 Copilot, and PII Tools is still … Read More
Securing Data Against AI Applications, Part II

AI Data Protector safeguards your sensitive data and company information from 3rd-party AI models. Increase efficiency AND keep your private data private!
Securing Data Against AI Applications, Part I

Use AI to discover and remediate at-risk information with an AI Data Protector. Increase security, raise efficiency, and avoid potential data disasters!
The Evolution of PII Protection: From Paper to Digital

PII has come a long way in a relatively short time, yet protecting it fully is like trying to shield a moving target. But sometimes the best way to choose a path forward is to peek at the past and learn from its evolution. Humble Beginnings It’s hard to think about PII, or rather Personally Identifiable Information, without also imaging … Read More
How To: Understanding RoPA and Achieving Compliance
Did you know the GDPR has 99 different articles and over 250 pages? You’ll likely never know each provision individually, but there’s at least one article worth paying extra attention to. Meet Article 30: RoPA. The GDPR If you’re the kind of person interested in articles about sensitive data and compliance, we sure hope you’re already well aware of the … Read More
Classify Data in 3 Easy Steps
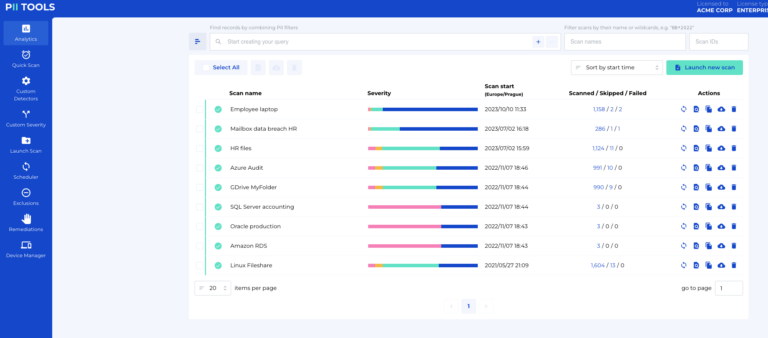
Quick scans, Custom Detectors, and Custom Severity. Learn to classify information automatically and guarantee every piece of your data protection puzzle is perfectly in place. Why Classify Data? Before we get to the details, it’s worth mentioning the main reasons why you should even bother to classify different types of personal data. On average, companies keep over 2 PB of … Read More
Person Cards® – The Holy Grail of Data Discovery
By 2025, the global datasphere is estimated to hold as much as 175 zettabytes of data. How can companies today possibly have a chance to organize that much information? The answer: Person Cards®. More Data, More Problems 175 zettabytes of data worldwide? Considering a single zettabyte is equal to a trillion gigabytes (yes, with a ‘T’), the actual amount of … Read More
What’s new: NIST Cybersecurity Framework 2.0
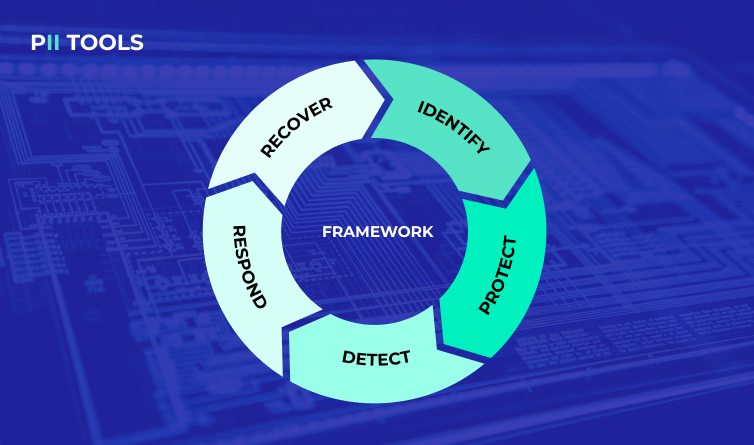
It’s been almost 10 years since the original CSF 1.0 was issued, and so much has changed since. What new guidelines does CSF 2.0 bring, and how can you implement them today? Remembering CSF 1.0 Before we get to the new stuff, let’s run through a quick recap of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) … Read More
- Page 1 of 2
- 1
- 2





