You've suffered a data leak, and the clock's already ticking. Oh, and it's a large dataset, too. Where do you even start to locate every single instance of PII involved? Let's get into it!
Breach Incident Scanner
Discovering leaked sensitive information and PII by hand is completely unrealistic for large datasets, so automated solutions like PII Tools come in handy. This sensitive data discovery software comes packed with automated and accurate features to make locating and remediating PII as simple and fast as possible.
Data breaches are serious, and like a hole in a water dam, they're getting worse with every second left unresolved. That's why PII Tools doubles as a powerful Breach Incident Scanner. This on-prem PII scanner quickly identifies exposed personal data, generates interactive drill-down reports and Excel reports, and streamlines your response process.
Because when a data leak hits, you need to seal it instantly—no manual reviews required.
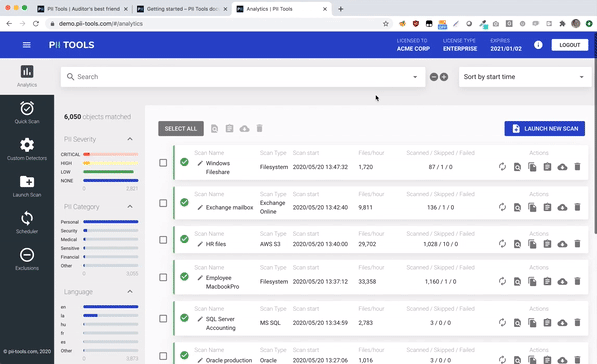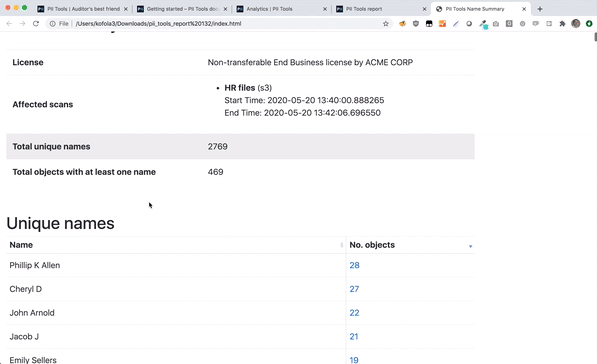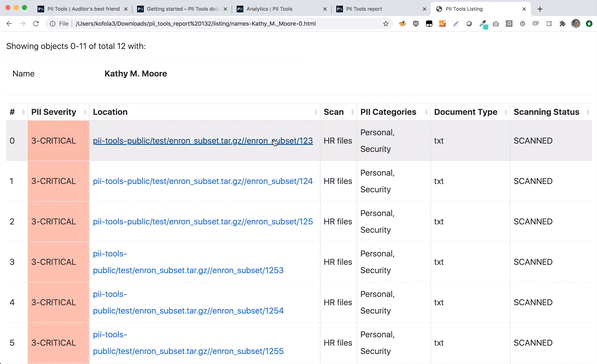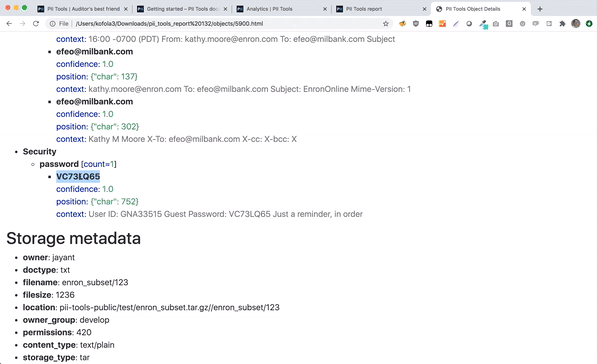
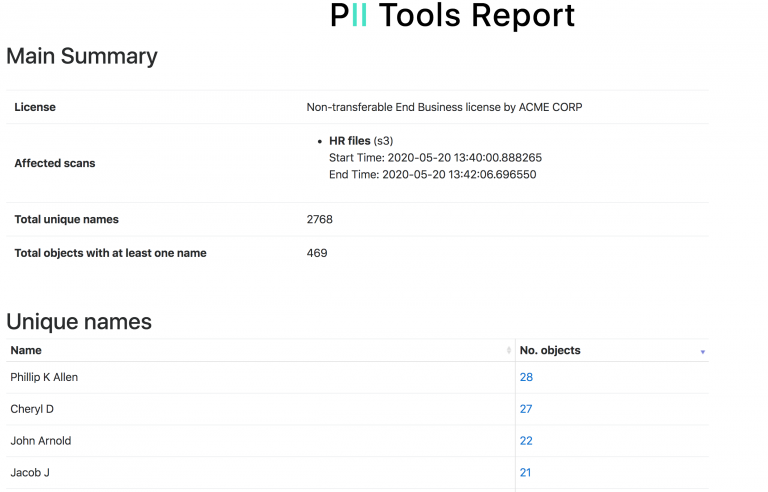
PII Tools lets you export an interactive drill-down report, summarizing all people affected by a data breach.
Person Cards®
One of PII Tools' most recent and effective features for dealing with data breaches and data loss is known as Person Cards®. These are a complete game-changer for breach investigations as they automatically link up all PII, PCI, and PHI that the AI detectors located on each affected data subject.
That information includes their name, email, DoB or credit card, from both structured and unstructured data, files, emails and databases. The resulting rolled-up Person Cards® can be exported into a spreadsheet for easier import into Relativity and other eDiscovery platforms.
Person Cards® also work great in conjunction with the PII analytics dashboard, where you can select which files to view and export using advanced filters.
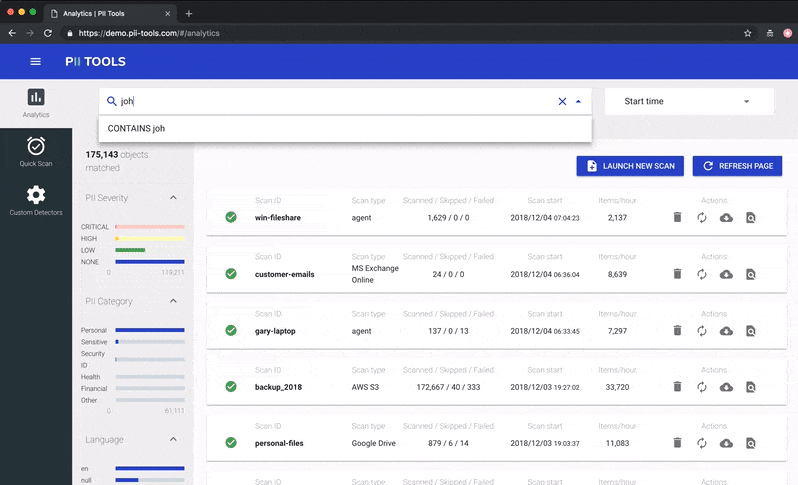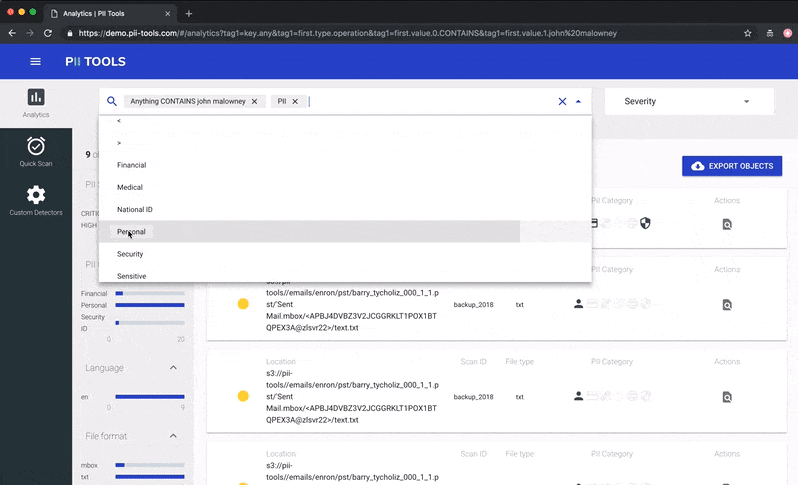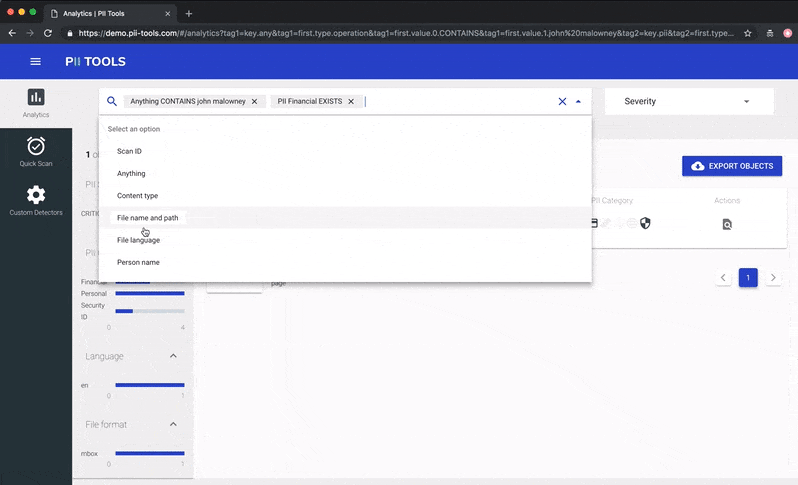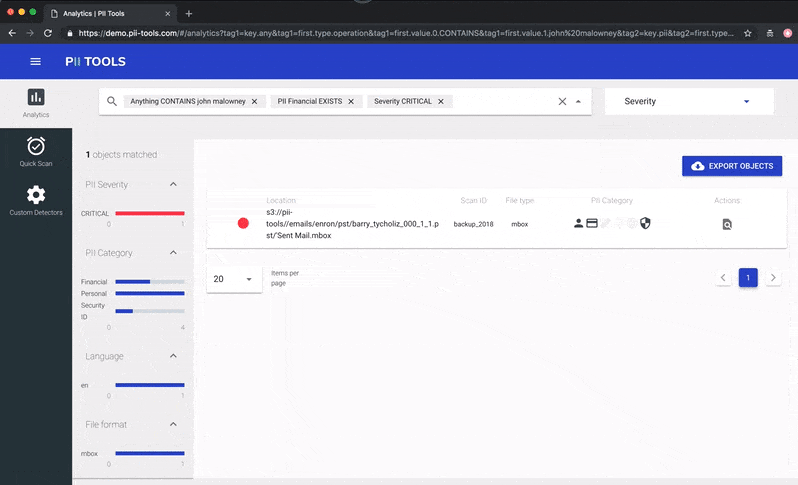
Slice & dice your data using filters in PII Analytics, then export the result into a clear report.
Data Breach Resolution
With PII Tools' AI-driven features, users can pinpoint all information affected in a data breach. This accelerates the data leak resolution process exponentially, allowing you to plug the hole as soon as possible while feeling confident thanks to its 99+% accuracy.
It's time to take your PII security seriously. With this Breach Incident Scanner, you can handle any data breach with speed and efficiency. Then, continue to use PII Tools to greatly minimize the likelihood of it ever happening again.
Put the power of data security back in your own hands!
This is an article about PII Tools, our on-prem (self-hosted) software for accurate personal and sensitive data discovery. PII Tools uses proprietary context-aware AI technology to make the life of CISO, Security, Legal & Privacy teams easier.
Learn More about Data Breach Prevention: Breach Incident Management.