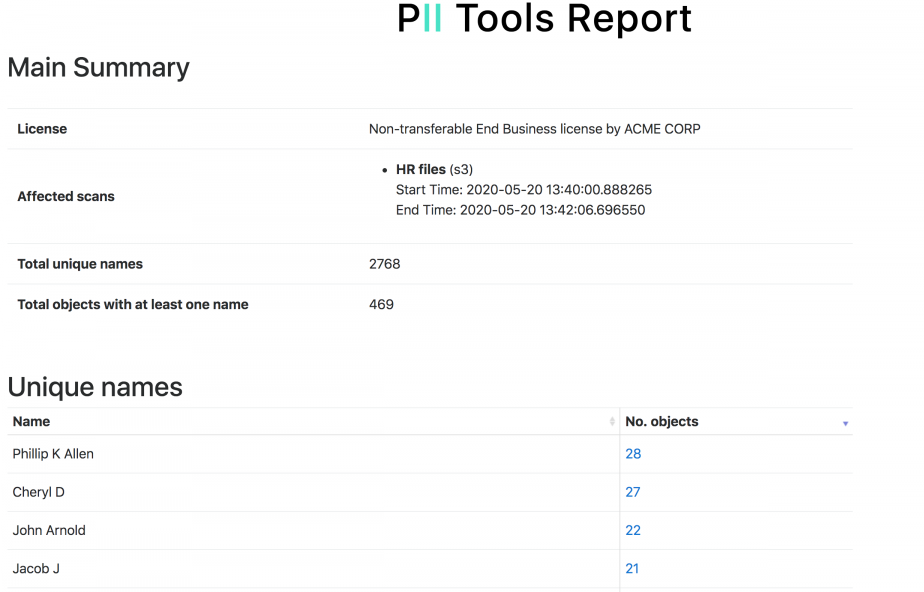
There was a data breach, the clock starts ticking. The dataset is large. How do you quickly determine who’s affected and how? Who’s Data Was Breached? Manual discovery of sensitive information is tedious and costly, so automated solutions like PII Tools come in handy. In its latest 3.7.0 release, we implemented new features in PII Tools to support breach workflows. … Read More
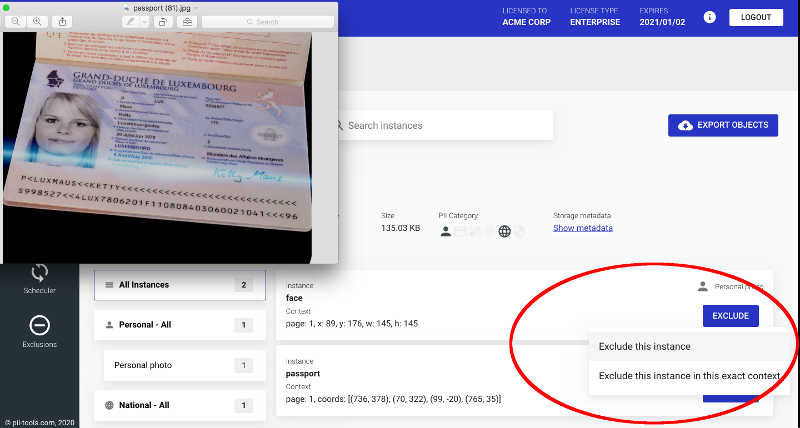
Exclude PII / PCI / PHI From a Breach Report
When responding to a breach incident, having a clear idea who’s affected and how is a matter of urgency. Manual discovery of PII information is tedious and costly, so automated solutions come in handy. But how to deal with false positives? PII Exclusions One typical task during a data review is removing unwanted data instances. PII Tools already automates PII … Read More