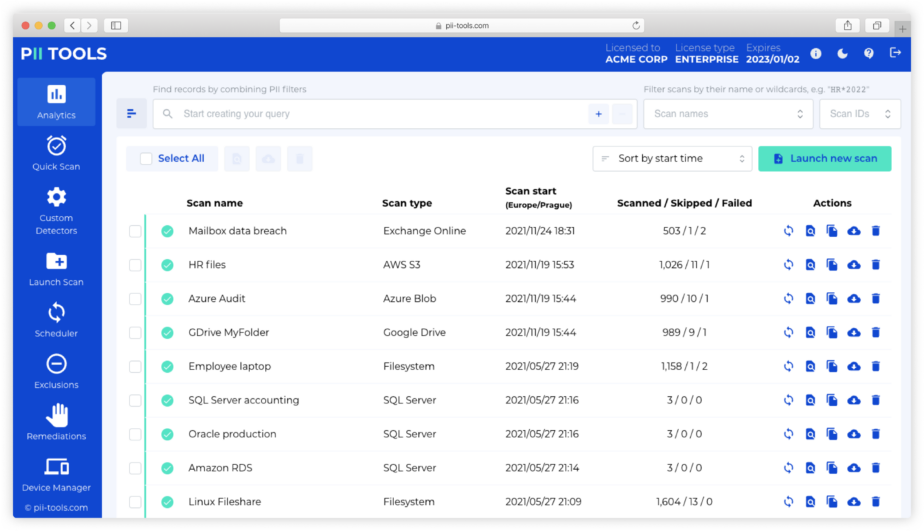
PII Tools lets you automatically quarantine, erase, and redact files and emails to sanitize high-risk data. It works equally well over local data (file shares, laptops, devices) and cloud data (including Exchange emails and their attachments, Sharepoint, OneDrive), so let’s explore how to apply remediation to your workflow. Let’s assume you’ve already identified where the sensitive data lives and which … Read More
Scanning Office 365 for sensitive PII information
Discover personal & sensitive data inside Office 365 accounts and remediate it. This includes both structured and unstructured data in Microsoft OneDrive, Microsoft Exchange Online, and Sharepoint Online. What does “support Office 365” mean? With PII Tools, you directly find, review, and remediate personal and sensitive information in documents, emails, and tables shared within your company’s Office 365 accounts. No … Read More
How to evaluate PII discovery software
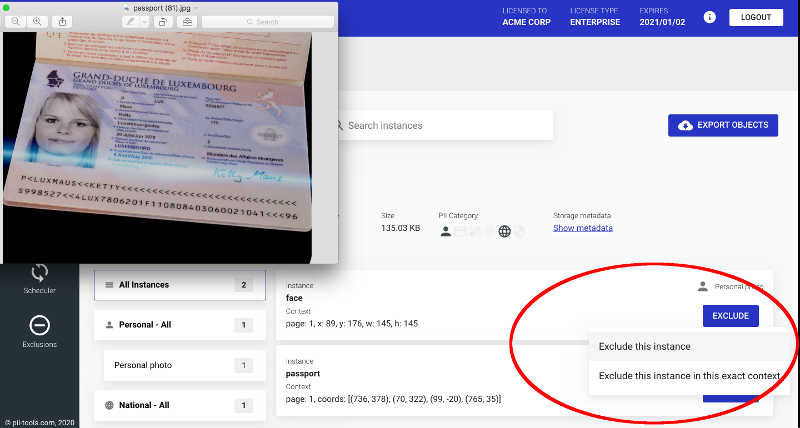
So, you’re considering buying software for discovery of PII / PCI / PHI. Or about to start your trial of PII Tools. How to test discovery SW properly? Don’ts: Careful what you test for Consider the following “passport”: Why won’t PII Tools detect the “PII” in this passport scan? This is an actual file submitted to our support team during … Read More
Finding Affected Persons in a Data Breach
There was a data breach, the clock starts ticking. The dataset is large. How do you quickly determine who’s affected and how? Who’s Data Was Breached? Manual discovery of sensitive information is tedious and costly, so automated solutions like PII Tools come in handy. In its latest 3.7.0 release, we implemented new features in PII Tools to support breach workflows. … Read More
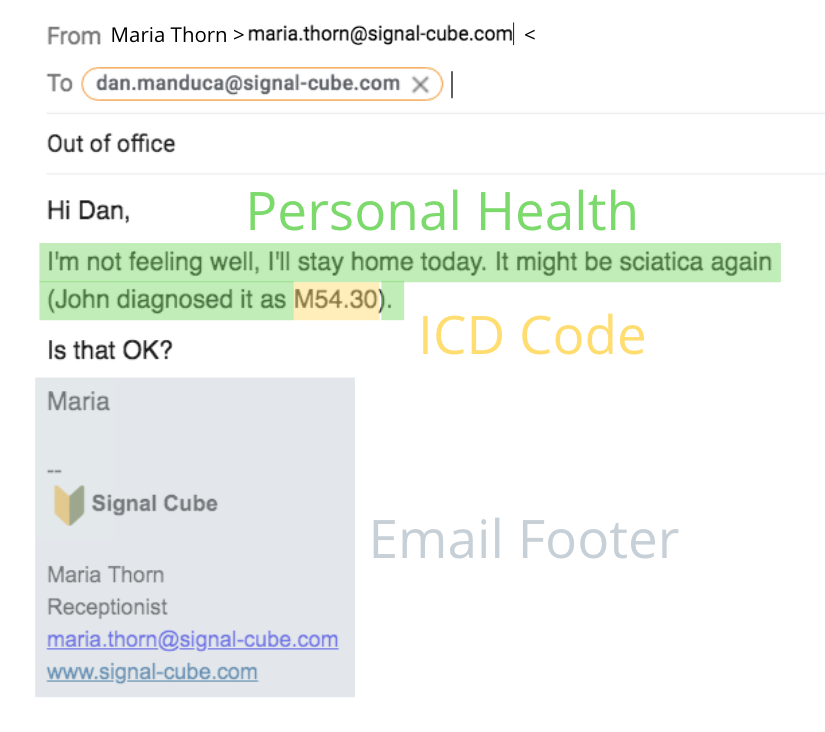
Exclude PII / PCI / PHI From a Breach Report
When responding to a breach incident, having a clear idea who’s affected and how is a matter of urgency. Manual discovery of PII information is tedious and costly, so automated solutions come in handy. But how to deal with false positives? PII Exclusions One typical task during a data review is removing unwanted data instances. PII Tools already automates PII … Read More
How To Automate Personal Data Discovery
The recent wave of privacy legislations around the world introduced new challenges to experts in litigation support, incident response and auditing. How can modern automation help with reliable PII discovery across emails, files, and databases? 3 Reasons Keywords Fail Traditional approaches based on manually defined keywords and regular expressions fail for three fundamental reasons: High cost. Keywords and regexps are … Read More
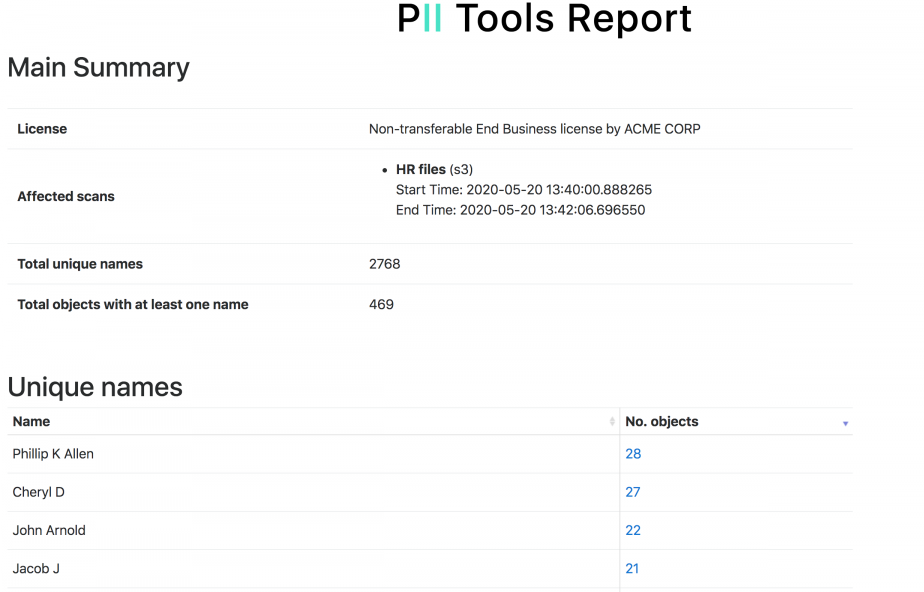
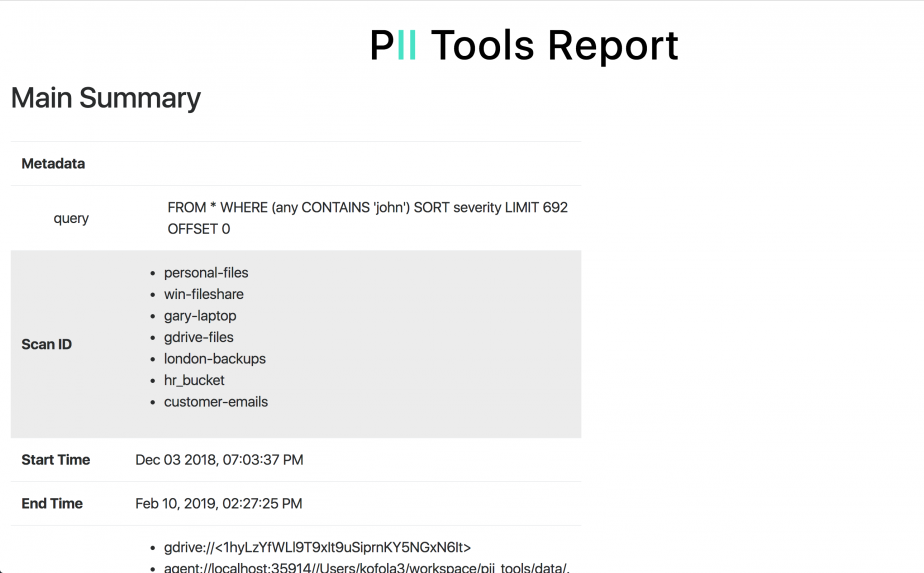
Export PII drill-down reports
In the latest February release (version 2.4.0), we combined Personal Data Analytics search with dynamic HTML report generation to make GDPR compliance and auditing easier. PII Tools already supports dynamic PII Analytics queries to locate personal, sensitive and intimate information. It also generates drill-down PII audit reports for completed data scans. In the latest release, we combined these two capabilities. You can now … Read More
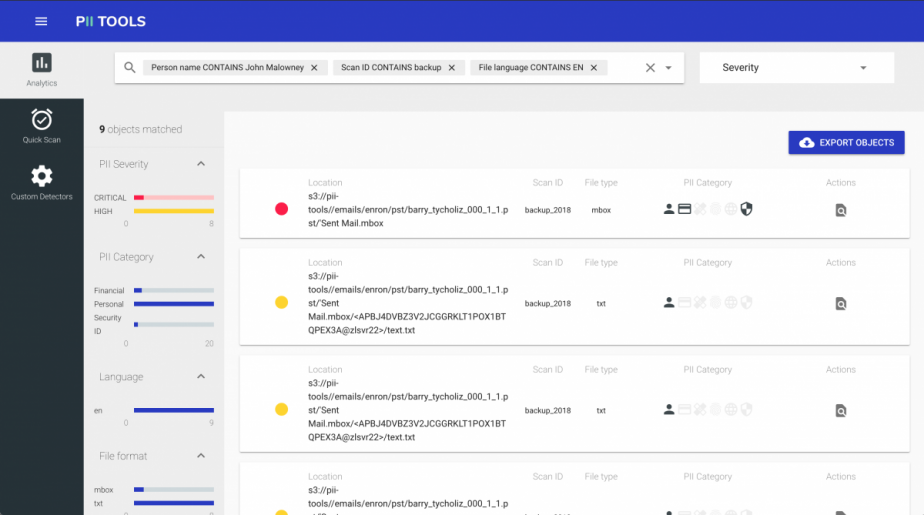
Personal Data Analytics
The latest 2.0 release of PII Tools brings a brand new SAR dashboard, allowing targeted personal data search, filtering and analytics. Search for all files on John that contain any financial information, while restricting the results to CRITICAL severity only. Locating Information for Data Subject Access Requests What if you want to find all data related to a specific person … Read More