Fines, penalties, fees… Oh my! But by mismanaging PII, we stand to lose more than just money. It’s time to look at what’s at stake and learn how to avoid these numerous pitfalls. It’s All About the Money Unfortunately, for many people and companies, the only time they actually start to care is the moment their wallet gets involved. Taking … Read More
Understanding PCI DSS v4.0

Understanding PCI DSS v4.0 The latest update to the PCI DSS is finally in full force. Discover the ins and outs of this sometimes tricky regulation and make sure you’re processes are still up-to-date. Let’s get into it! A Quick Refresher If your business accepts cards in any way, it’s safe to guess you’re already well familiar with the PCI … Read More
10 Reasons YOU Should Be Using PII Tools Right Now!

There are plenty of reasons to use PII Tools Data Discovery Software, but we’ve managed to narrow them down to our TOP 10. Let’s check them out! #1 Automated Scanning for 400+ File Formats The more daily tasks you can fully automate, the more time you can focus on what actually makes your company money. And with over 400 compatible … Read More
FERPA, Compliance, and Everything in Between

Another day, another data compliance to wrap our heads around. This time, uncover the basics of FERPA, who it protects, why you should care… and everything in between. FERPA – The Champion of Students FERPA… aren’t those the local guys on Mt. Everest, carrying all the rich “mountaineers’” equipment to the top and back, with no oxygen tank or fancy … Read More
How to: Protecting ePHI

The average healthcare breach exposes 3+ million private patient records. What are you doing to discover, store, and protect ePHI? Why the ‘e’ in ‘ePHI’? HIPAA, PHI, PII, GDPR, ePHI… Where would we be without our acronyms? If you’re interested in protecting ePHI, it’s safe to say none of these are entirely new to you. The most important to our … Read More
Intro to Integrated Risk Management
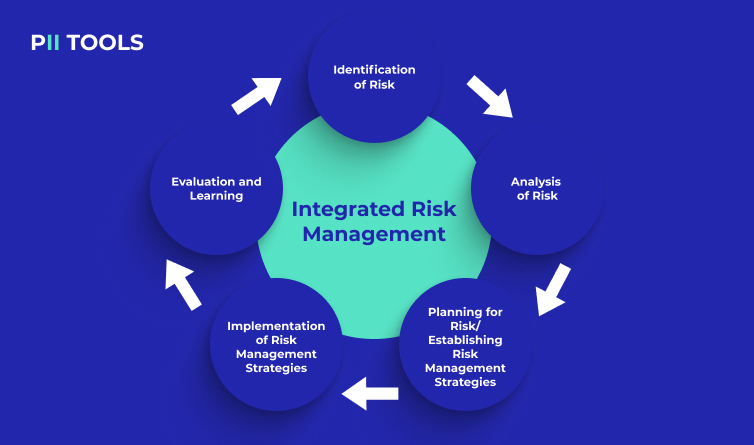
What’s the worst thing about risks? They’re often hiding where you’d least expect them. So, let’s review a few best practices for finding and eliminating them. IRM 101 Few words captivate audiences more than Integrated Risk Management (IRM). It’s easy to picture them displayed on a corporate slideshow for a room full of less-than-enthused paper pushers just waiting for their … Read More
The Best Protection Against AI Attacks
Cyber-attacks are at an all-time high, and AI has only made them more rapid and efficient than ever. What are the best ways to protect yourself when “fighting against the machines”? A Newest Calamity In 2020, the World Economic Forum issued its yearly Global Risks Report, claiming cyber-attacks now stand alongside natural disasters and climate change as one of humanity’s … Read More
How To: Understanding RoPA and Achieving Compliance
Did you know the GDPR has 99 different articles and over 250 pages? You’ll likely never know each provision individually, but there’s at least one article worth paying extra attention to. Meet Article 30: RoPA. The GDPR If you’re the kind of person interested in articles about sensitive data and compliance, we sure hope you’re already well aware of the … Read More
Classify Data in 3 Easy Steps
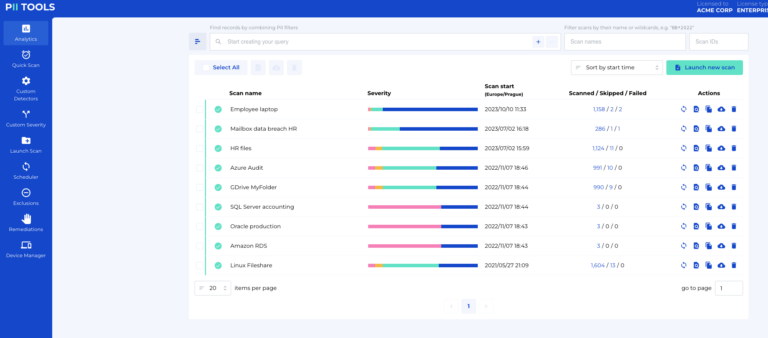
Quick scans, Custom Detectors, and Custom Severity. Learn to classify information automatically and guarantee every piece of your data protection puzzle is perfectly in place. Why Classify Data? Before we get to the details, it’s worth mentioning the main reasons why you should even bother to classify different types of personal data. On average, companies keep over 2 PB of … Read More
Data Redaction: The Essential Guide to Protecting Sensitive Data
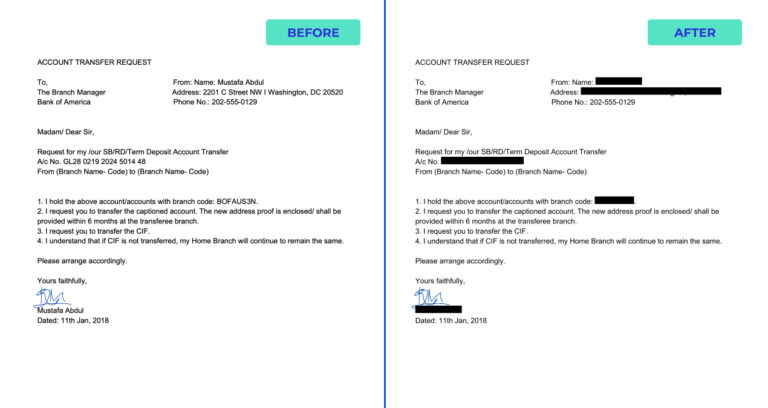
The long-awaited data redaction feature by PII Tools is finally here. Generate new, AI-driven PDFs from original files with all personal data automatically blacked out – this is the future of genuinely efficient data redaction. What Does Data Redaction Mean At PII Tools, we’ve made it our calling to create AI-driven software to maximize data discovery and the remediation of … Read More





