Over 402 million terabytes of data are generated every day. And giant companies like Google and Meta can’t wait to collect and sell as much as possible.
The first step to protecting your personal data is identifying it. This three-part mini-series will take you through the ins and outs of PII and help you safeguard what’s yours.
PII Basics
PII stands for Personally Identifiable Information and it’s essentially any personal data that can be used to identify someone. Obvious examples include your first and last name, home address, details about your family, ID number, etc.
The term ‘PII’ is also used as a sort of catch-all for personal data types. If you dive deeper into PII, you’ll discover protected data, sensitive data, protected health information (PHI), the PCI DSS (the Payment Card Industry Data Security Standard), and more. We’ll discuss these in detail below, but for now, think of PII as the umbrella under which all specific forms of personal data fall.
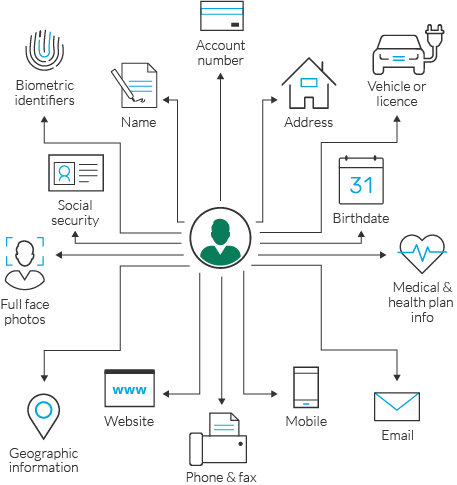
Source: Imperva
Direct vs. Indirect Identifiers
The most effective way to discover if a piece of information is PII or not is with direct and indirect identifiers.
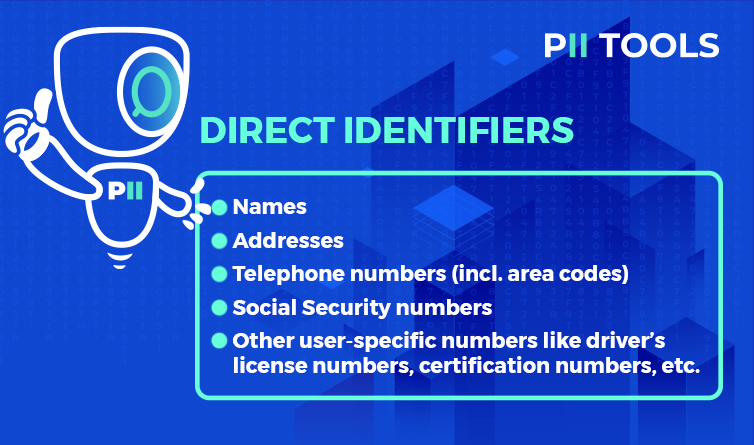
Direct identifiers are variables that point explicitly to particular individuals. If someone (or some program) can take a single piece of information and track it back to you, then that’s a direct identifier. Here are a few examples:
Direct Identifiers
- Names
- Addresses
- Telephone numbers (incl. area codes)
- Social Security numbers
- Other user-specific numbers like driver’s license numbers, certification numbers, etc.
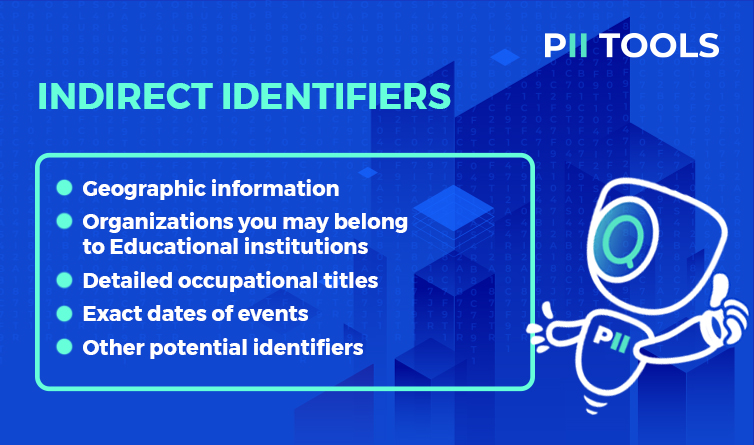
Now, the opposite. Indirect identifiers are variables that may be used together or in conjunction with other information to identify someone. Examples include:
Indirect Identifiers
- Geographic information (state, country, region, etc.)
- Organizations you may belong to
- Educational institutions (what school did you go to, where did you graduate from?)
- Detailed occupational titles (e.g., Head of Sales in Tacoma, Washington)
- Exact dates of events (birth, death, marriage, divorce, etc.)
- Other potential identifiers like detailed income information, political positions held, etc.
You may think it’s fine if someone knows where you attended university or what year you were born if they don’t know your actual name. But you’d be surprised how easy it is today to take a few indirect identifiers, add a bit of easy Googling and social media… and suddenly all your PII is out in the open.
PII vs PHI vs PCI
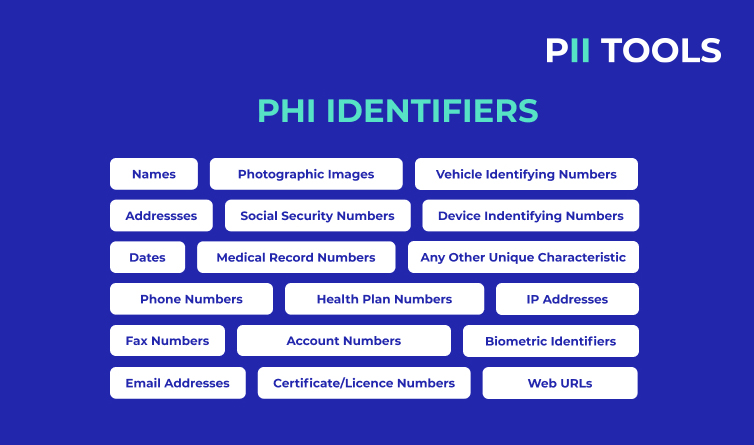
As mentioned above, PHI stands for Protected Health Information. This is a specific sub-class of PII, primarily protected under HIPAA, complete with its own identifiers. PHI identifiers are directly related to your health or the healthcare industry in some way.
A few examples include medical record numbers, biometric identifiers, and health plan data. Learn more about PHI (and its online version ePHI) here.
And next, we have the PCI, or its full version ‘PCI DSS’ (The Payment Card Industry Data Security Standard). The PCI is a standard that regulates how organizations handling major credit cards process, store, and transmit credit card information.
PII protected under the PCI include credit and debit card numbers, expiration dates, card names, PINs, etc. By placing guardrails on this sort of data, the PCI protects users from being identified by their purchases and from identity theft. For a full deep dive on the topic, be sure to check out The Basics of the PCI.

Just for Starters
With millions of terabytes of personal data being generated on a daily basis, there’s never been a more important time to protect your PII than today. Now armed with the basics of PII and its various types, we can take the next step in our Complete Guide to PII.
Be sure to check out Part Two of this series and become the master of your own personal data!
Protect Your Customers’s Info with the PII Tools Data Discovery Software!





