Sensitive data and personal information come in many shapes and sizes. And with so many different regulations around the globe, it’s easy to confuse one with another. These are the basics of PII and every form you’ll find it in. Let’s get into it. Understanding PII The world of sensitive data protection has its own terminology you’ll need to be … Read More
How To: Understanding HIPAA Compliance
For many readers, when they hear the words “the Health Insurance Portability and Accountability Act (HIPAA)”, their eyelids immediately start to droop. But I’m sure getting slapped with an annual $1.5 million fine would wake them up! Whether you’re the one handling the data or the actual patient looking to protect your rights, it’s time to become a HIPAA expert … Read More
What Are Sensitive Data Discovery Tools and How Do They Work?
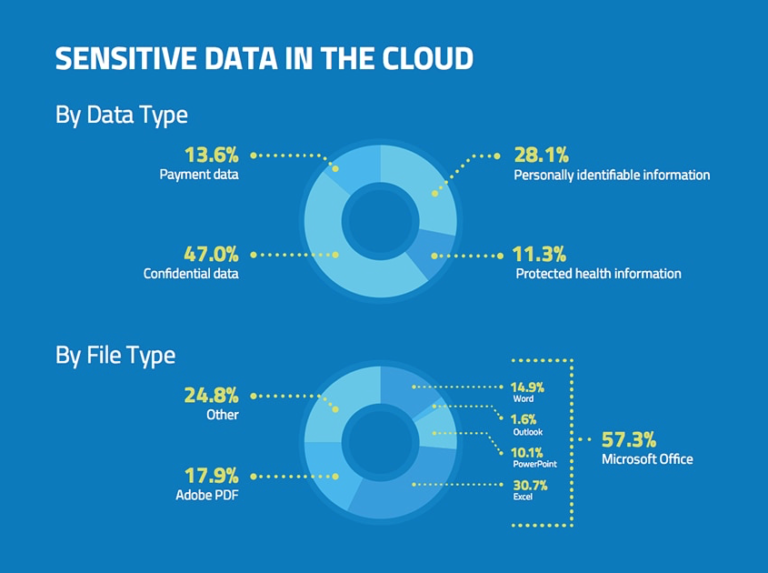
With technology progressing and changing every day, it can sometimes be difficult to keep up with the times. As a business, however, falling behind can mean letting important (and legally binding) information fall through the cracks, disappointing customers and losing the trust of business partners. This is where sensitive data discovery tools come into play. But what exactly are they … Read More
Detect person names in text: Part 2 (Technical)
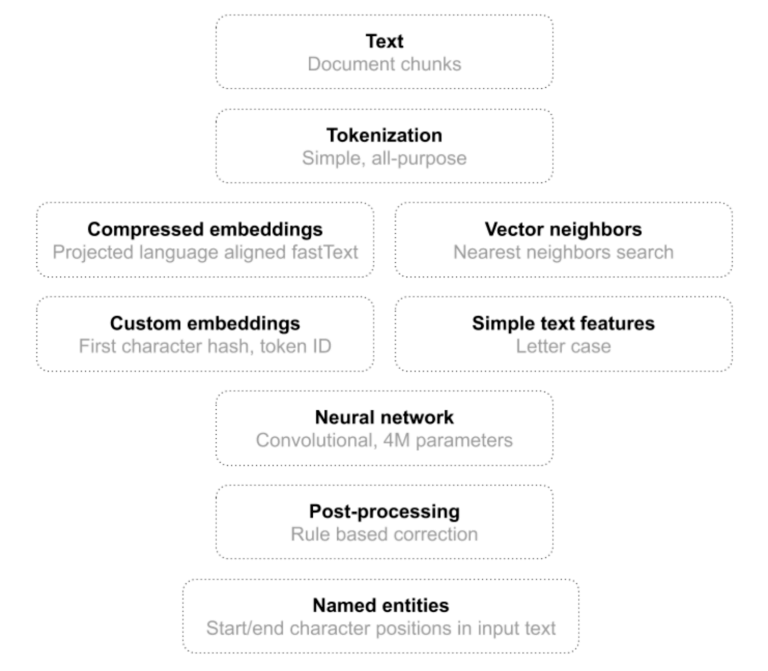
In Detect Person Names in Text: Part 1 (Results), we benchmarked our new named entity recognizer (NER) against popular open source alternatives, such as Stanford NER, Stanza and SpaCy. Today we dig a little deeper into the NER architecture and technical details. First, recall our main NER objectives. In short, we require our NER to be practical, rather than just … Read More





