The average healthcare breach exposes 3+ million private patient records. What are you doing to discover, store, and protect ePHI?
Why the ‘e’ in ‘ePHI’?
HIPAA, PHI, PII, GDPR, ePHI… Where would we be without our acronyms? If you’re interested in protecting ePHI, it’s safe to say none of these are entirely new to you. The most important to our story, however, are simply PHI and its now tech-savvy brother, ePHI.
Protected Health Information (PHI) is essentially a person’s health-related Personally Identifiable Information (PII). In other words, your home address is an easy example of PII, whereas your medical records are PHI. (Here’s a great article about HIPAA and PHI.)
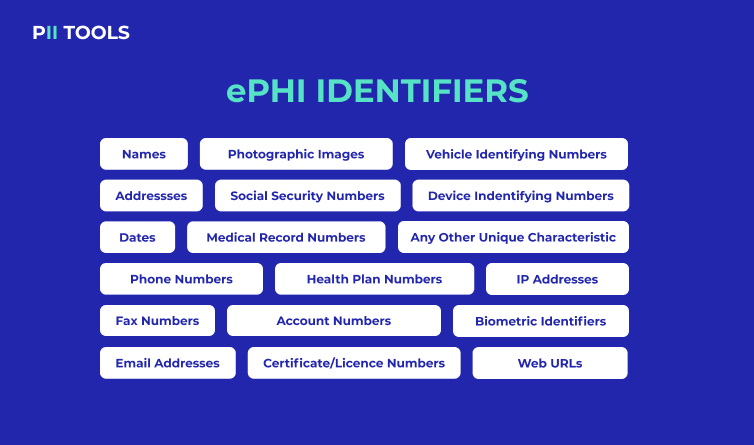
So, where does the extra ‘e’ come in? Well, it’s not the 1990s anymore. Typically, doctors aren’t faxing patients their medication lists or forwarding their medical bills by snail mail (although this still happens). As you may have guessed, the ‘e’ stands for ‘electronic’, meaning Electronic Protected Health Information, i.e., digitalized PHI.
Similar, Yet Not
“So, ePHI and PHI are basically the same thing? One’s just the old-school, physical format while the other is online?”
What a perfect question, leading us right into the next section! It’s true; PHI is any form of PHI that’s received, sent, or stored electronically. This includes everything from data in online patient records to PDFs, emails, medical devices, flash drives… you name it.
PHI and ePHI are very similar, but there’s one thing that completely separates the two: how they can be protected. Not many people can sneak into a hospital filing room after dark, flashlight in hand, and make off with your precious ePHI. On the contrary, if something is stored electronically, then it can be stolen electronically.
And that begs the question: What are the best ways to protect ePHI?
ePHI Protection in 3 Steps
One could say ePHI lives and dies by the sword. On one hand, digital tools are used to modernize the healthcare industry, making collecting and storing PHI easier than ever. And these same tools are also deployed to safeguard ePHI.
On the other hand, ePHI is vulnerable to the same cyberattacks as all the other 1s and 0s. Robust cybersecurity measures are necessary for guarding ePHI against hooded hackers looking to click and type their way into medical facilities’ patient storages.
3 main elements go into protecting ePHI, namely Administrative, Physical, and Technical safeguards. Let’s talk about each below.
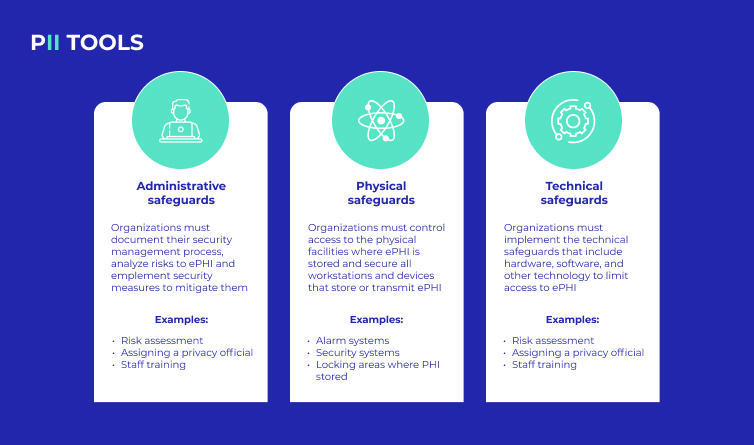
Administrative Safeguards
Policy, policy, policy. When a company sets the correct precedents right from the start, its internal processes can save a lot of future headaches. Declaring a Security Officer or Data Protection Officer is a great first step.
Other admin protections include access management, where you ensure only the right people have access to ePHI, as well as HIPAA-specific training. ePHI is less likely to end up on the wrong side of human error if everyone knows how to handle it correctly.
Physical Safeguards
Like a heavy-duty lock on a safe, there are physical ways to ensure ePHI never makes it into the wrong hands. This type of safeguard varies greatly by business, given that some have remote workers with devices that could be lost or stolen, while others may choose to keep matters strictly online.
Or one company may need to provide a keycard-accessed locking system on any storage terminals storing ePHI. This could even require hiring an actual security guard or team and using cameras to monitor all locations managing ePHI.
For smaller businesses, however, physical safeguards can be as simple as wiping the hardware of any ePHI before it’s disposed of or given to another user with lesser access permissions.
Technical Safeguards
Because ePHI is PHI in an electronic format, the best way to safeguard it is by implementing the right tech.
You can use a tool that helps monitor user access and verification, preferably one that offers automatic time-outs if something goes wrong or a user stays on a page too long without activity. Then there are integrity controls because even people with the “right pay grade” can make mistakes, leading them to accidentally (or maliciously) alter, exfiltrate, or improperly delete ePHI.
Lastly, one of the most effective tools used to technical safeguard ePHI is sensitive data discovery software. Of course, there are many options when choosing such software, but you should only ever select one that locates, analyzes, and remediates any instances of non-regulatory ePHI in your storages.
From a technical standpoint, the best way to protect ePHI is to ensure it’s only ever in the right location. And a sensitive data discovery tool that also lets you perform in-house audits is perfect for this.
A Worthy Investment
Protecting data – no matter what kind – should always be your main priority. Not only does this help ensure you stay out of any legal trouble, but, more importantly, it secures those who have trusted you with their information.
And this sentiment rings even more true with PHI and ePHI. Nobody ever wants their sensitive data leaked, but few things are worse than having your sensitive HEALTH data leaked. It’s almost like having a complete stranger sit in with you and your doctor during an exam, taking notes to exploit you with later.
Do what’s best for you, your company, and your users by investing in ePHI safeguards on every level. Now, that’s money well spent.
Experience True ePHI-specific Protection with the FREE PII Tools Demo!





