Part 1 of 3: Data Leak Basics (Part 2, The Perfect Employee Training; Part 3, 10-Point Data Security Checklist)
Nearly 90% of breach incidents are caused by human error. This 3-part mini-series tackles the subject head-on, covering everything from root causes and prevention techniques to the perfect employee training. Let’s get started.
What is a Data Leak?
A data leak, often called a data breach, is the intentional or unintentional release of secure or private information to an untrusted environment (learn more about data leaks in our three recommended best practices).
Many factors cause data breaches, including hackers and computer fraud. However, as unlikely as it may seem, the number one cause of data leaks is human error.

Source: CVG Strategy
Employee Negligence
Within the category of “human” or “employee” error, you’ll find the root causes of sensitive data loss. According to Bloomberg BNS, over one-third of incidents were the result of employee negligence (compared to only 22% of external cyber attacks). Negligence comes in many forms; for example, a surprising 25% of employees don’t even lock their work computer when they leave their desk.
Employees can also be tricked by phishing attacks. Essentially, an employee receives an email from whom they believe to be their boss or CEO asking for sensitive information (passwords, regulation-protected PII, etc.). Without thinking twice, the employee emails back the requested information, and that’s all it takes. Data leaked.
Combat Employee Negligence
The most effective method for eliminating data leaks caused by human error starts at the top. If the employees intimately know not only their management team but also their boss or even the company’s CEO, they can avoid phishing attempts with ease. Did you just get an email from your “boss” asking for sensitive corporate information? If you already communicate with your boss often, you’ll have no problem recognizing a fake or suspicious email.
Once this management/boss-employee relationship is established, employees can then apply what they learned in cybersecurity training by following the example of their superiors. If they see their manager frequently speaking of proper data loss prevention techniques, they’ll remember to follow suit. This includes everything from locking their unattended computers to reporting suspicious emails/communication.
Data Leak Management
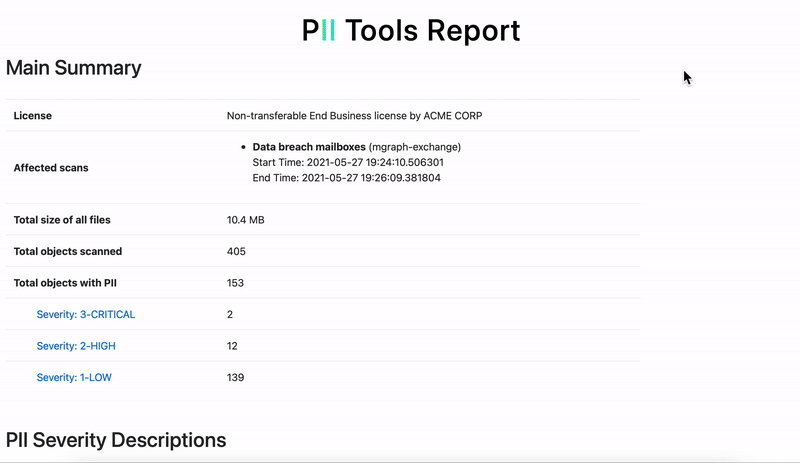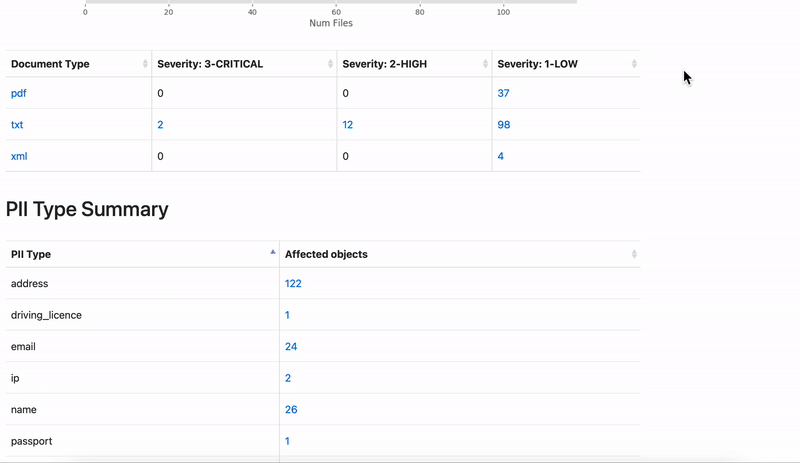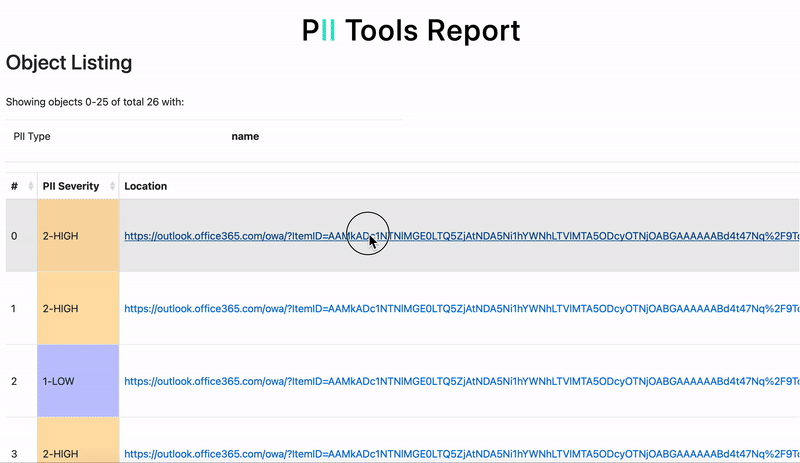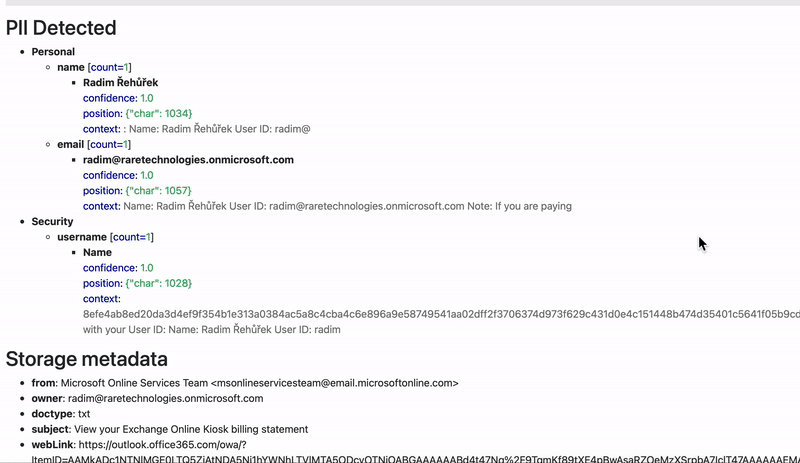
Unfortunately, data breaches still take place, no matter how well-trained employees are. Luckily, there are more measures you can implement to prevent a data leak before it happens. PII Tools is used by corporate infosec, legal and DPO teams for data protection. The software’s primary function is to provide accurate PII scans, enabling companies to discover sensitive data and take remedial action quickly.
Even after having taken these precautionary steps, data leak prevention is never 100% guaranteed. For this very reason, you’ll find the data breach management feature included in PII Tools’ arsenal. This gives you the options to:
- React quickly to identify whose data was affected
- Analyze millions of leaked files or emails for all types of PII
- Generate detailed, interactive reports about your findings
- Use those reports and information to take actionable steps to prevent data from being leaked this way again
Source: PII Tools
Prevent Data Leaks
To help eliminate data leaks of sensitive information, employees need to be trained in all the best data protection methods. And keep your eyes open for Part 2 in this series: The Perfect Employee Training: How to Avoid Data Leaks, coming soon.
Then, implement the best sensitive data discovery software available to fill in any leftover gaps. Take sensitive data protection into your own hands and educate everyone along the way. And our PII Scanner will help you on your way to full data security!
Remediate At-Risk Data and React Fast with PII Tools Breach Incident Responses.





