There’s nothing worse than wasting time and money, so is there any benefit to reviewing the data you store? Well, unless you want to be like the kid who never studies for tests, regular audits may be the only thing keeping you out of the principal’s office. To Audit or Not to Audit? By this point, I would hope none … Read More
Do They Even Matter?—The 3 Largest GDPR Fines To Date
For years now, the GDPR has been criticized for offering more bark than bite. As the fines stand, many mega-companies like Amazon and Google are simply getting away without a scratch. All this has left us wondering, what are the 3 biggest GDPR fines so far, and do any of them actually matter? Knowing the GDPR Before we get to … Read More
How To: Understanding HIPAA Compliance
For many readers, when they hear the words “the Health Insurance Portability and Accountability Act (HIPAA)”, their eyelids immediately start to droop. But I’m sure getting slapped with an annual $1.5 million fine would wake them up! Whether you’re the one handling the data or the actual patient looking to protect your rights, it’s time to become a HIPAA expert … Read More
How to remediate PII?
Within the world of sensitive data discovery, there are many roads you can take to remain compliant to mandatory regulations. Unfortunately, many of these roads can leave you with more questions than answers. If you’re looking for a simpler route to protect your company’s data, SaaS is right for you. What is SaaS? Pronounced /sæs/, SaaS stands for Software as … Read More
Creating Data Leak Reports
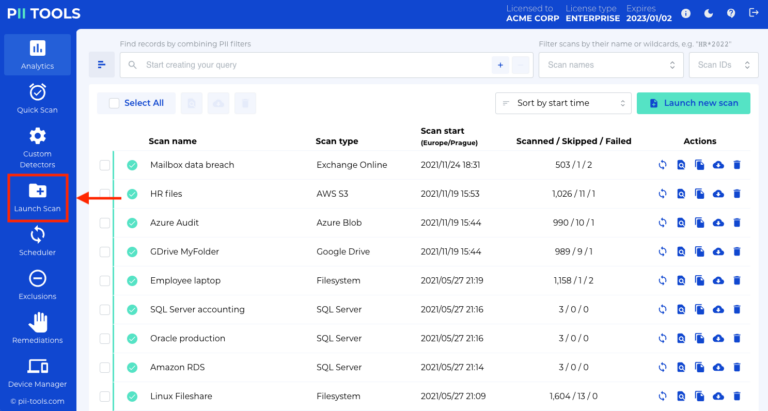
In this guide, you will learn how to create data leak reports with PII Tools. Launching a scan The first step towards the successful management of any data leak is to identify what was in the breached data. Open your PII Tools and, on the left side, select Launch Scan. If you performed the scan already, skip to the next … Read More
How to Identify Leaked Data

A data breach can happen to anyone at any time. Although there are many steps in responding to such a breach, the first is actually locating the data in question. If you’ve suffered a breach of information, how do you identify all affected parties? Detecting the Leak There are multiple ways you can tell you’re dealing with a data breach, … Read More
Discover Sensitive Data with SaaS
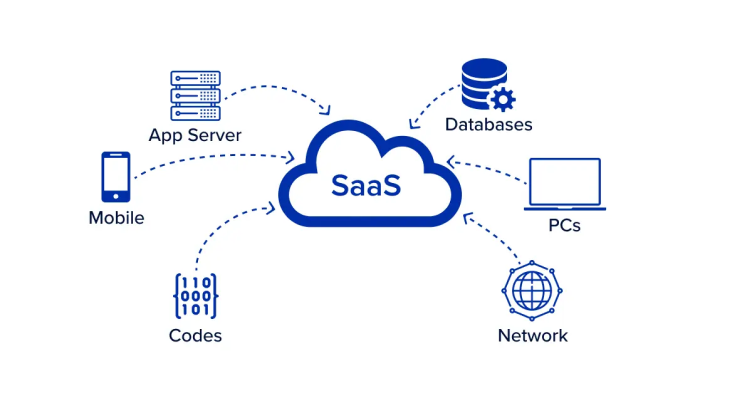
Within the world of sensitive data discovery, there are many roads you can take to remain compliant to mandatory regulations. Unfortunately, many of these roads can leave you with more questions than answers. If you’re looking for a simpler route to protect your company’s data, SaaS is right for you. What is SaaS? Pronounced /sæs/, SaaS stands for Software as … Read More
Scanning Office 365 for sensitive PII information

Discover personal & sensitive data inside Office 365 accounts and remediate it. This includes both structured and unstructured data in Microsoft OneDrive, Microsoft Exchange Online, and Sharepoint Online. What does “support Office 365” mean? With PII Tools, you directly find, review, and remediate personal and sensitive information in documents, emails, and tables shared within your company’s Office 365 accounts. No … Read More
The Basics of the PCI: What Makes It Different
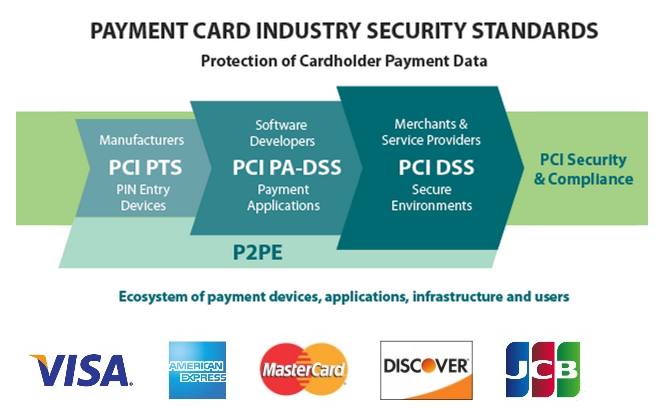
Today’s businesses are expected to adhere to many standards and regulations, everything from the notorious GDPR, to the more locally applicable LGPD. Luckily, many of the big-name data protection regulations share a similar base structure. But what about the PCI Standard? What sets it apart from the pack?
Making GDPR Compliance Simple
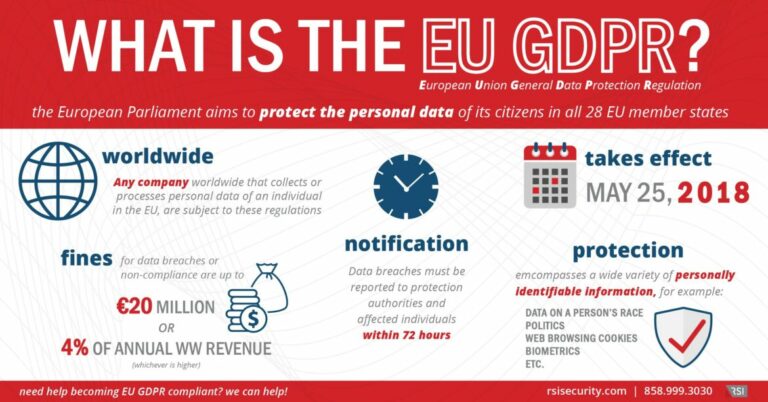
By now, we should all be well aware of the GDPR and what it means for our business. How is it then that so many companies remain GDPR non-compliant? Is the regulation too complicated, too time-consuming, or is it just a hassle? Discover everything you need to know to easily comply with the GDPR today. What is the GDPR and … Read More





