It’s been almost 10 years since the original CSF 1.0 was issued, and so much has changed since. What new guidelines does CSF 2.0 bring, and how can you implement them today?
Remembering CSF 1.0
Before we get to the new stuff, let’s run through a quick recap of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) version 1.0.

For years now, the CSF has acted as the world’s leading cybersecurity guidance, comprised of standards and practices that the US Government implores companies, organizations, and institutions around the world to follow. Initially intended for “critical infrastructure”, the CSF could also be applied in other sectors, albeit with a limited scope.
Later, in 2018, CSF 1.0 was modernized to CSF 1.1. This latest issue included new guidance and details on performing self-assessments, supply chain risk management, vulnerability disclosure processes, etc.
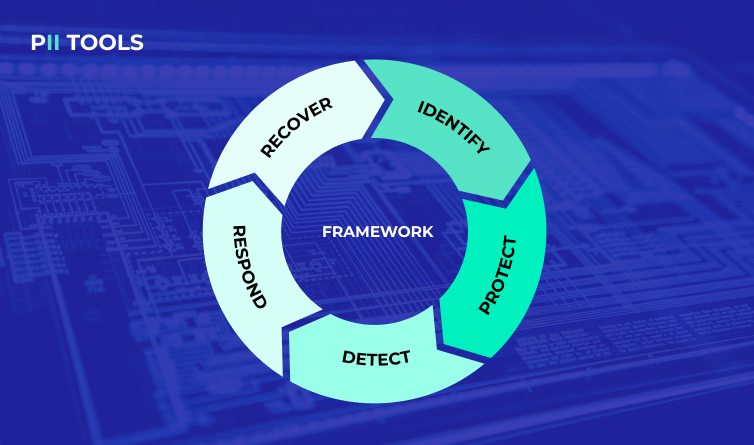
Lastly, the CSF has always been known best for its five “core functions”.
Time for an Update
Even though CSF 1.0 and later 1.1 have served well for nearly a decade now, feedback has been consistently mounting pretty much since day one. As we’re all too familiar, innovations in cybersecurity can have us feeling like our system is already outdated the same day it’s up and running.
Introducing Cybersecurity Frame 2.0, the update that many have been looking forward to for years. And CSF 2.0 doesn’t disappoint. Although imperfect, it does manage to address much of the criticism of its predecessor.
For starters, CSF 2.0 is no longer only developed with “critical infrastructure” in mind, but rather it strives to broaden its scope to pretty much anyone storing sensitive data across all platforms, whether on-premises or in the cloud.
To put it simply, NIST created its Cybersecurity Framework with government bodies in mind but later recognized that it was being implemented in sectors all over the world, including many institutions simply striving to enforce the best cybersecurity practices.
The 5 Original Pillars
As featured above, the original CSF 1.0 included 5 core functions, namely: Identify, Protect, Detect, Respond, and Recover.
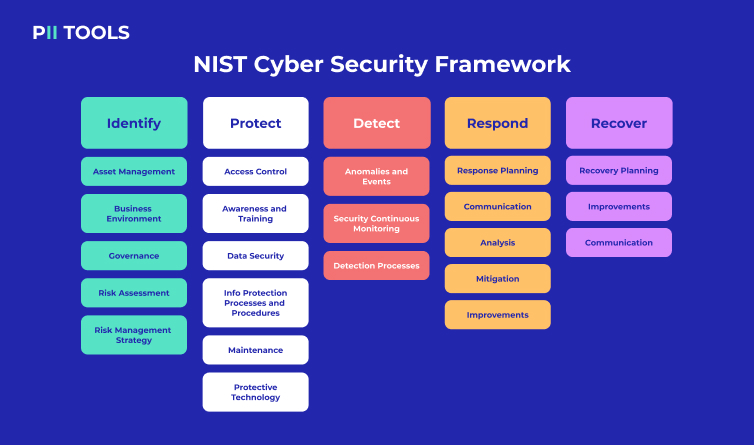
The 5 functions work as steps to correctly storing sensitive data. As we all know, you first need to Identify the type of sensitive data in storage, provide Protective measures to keep it safe, Detect potential hackers or data leaks (or data stored in incorrect locations), Respond to any issues that arise, and then Recover the data as well as your entire data storage processes.
However, with the introduction of CSF 2.0, a new member has been added to better complete these 5 functions.
The New 6th Pillar
The sixth member of CSF 2.0 is Govern. In their own words, NIST felt the new function should be added, stating: “Govern emphasizes that cybersecurity is a major source of enterprise risk and a consideration for senior leadership”.
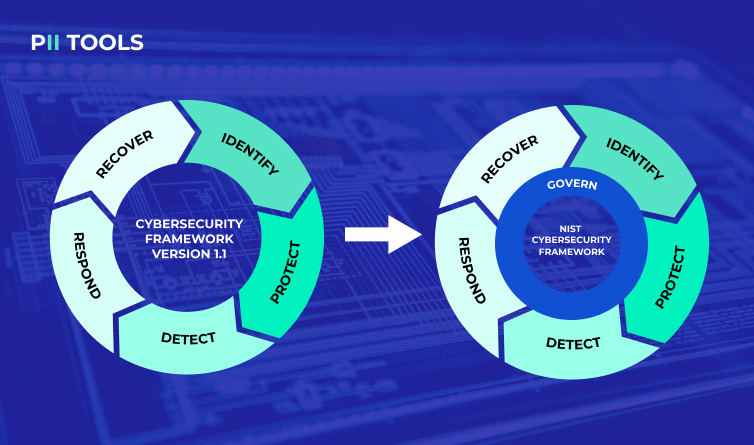
In other words, the newest core function covers how an organization can make and execute its own internal decisions to support its cybersecurity strategy. And as the convenient visual makes apparent, the Govern Function isn’t exactly a step you follow like the original five, but rather a protocol that should be implemented seamlessly throughout all five original functions.
CSF 2.0 in Practice
Unfortunately, we can’t cover the entire CSF 2.0 document and all its annexes in a single article (not one you’d actually want to read, anyway). What’s really important is that you walk away with an idea of how to follow all its recommendations.
CSF 2.0 is all about improving your cybersecurity by enhancing your system’s overall data protection and reaction capabilities. Now, this is much easier said than done. But the first step you should take when adhering to CSF 2.0 is to deploy quality data discovery software that can specifically deal with CSF compliance.
PII Tools offers this exact software, allowing you to automatically implement all 6 core functions with only a few clicks. Better yet, PII Tools supports some of the more complex aspects of CSF 2.0, like the Reference Data Set (RDS) from NIST’s National Software Reference Library (NSRL).
This newly added feature makes PII Tools the perfect software for compliance scanning and breach investigation.
CSF 2.0 Compliance
The right sensitive data discovery tool has been specially modified to provide CSF 2.0 compliance. This truly is one of the best ways to protect your company or organization while simultaneously safeguarding your stored sensitive data.
Do what’s best for your data. Discover how PII Tools can help you achieve CSF 2.0 compliance and protect everyone under your data umbrella today.
Schedule a PII Tools demo to see just how accessible CSF 2.0 compliance can be




