Part 1 of 3: Data Leak Basics (Part 2, The Perfect Employee Training; Part 3, 10-Point Data Security Checklist) Nearly 90% of breach incidents are caused by human error. This 3-part mini-series tackles the subject head-on, covering everything from root causes and prevention techniques to the perfect employee training. Let’s get started. What is a Data Leak? A data leak, … Read More
Fast & Accurate Data Breach Resolution
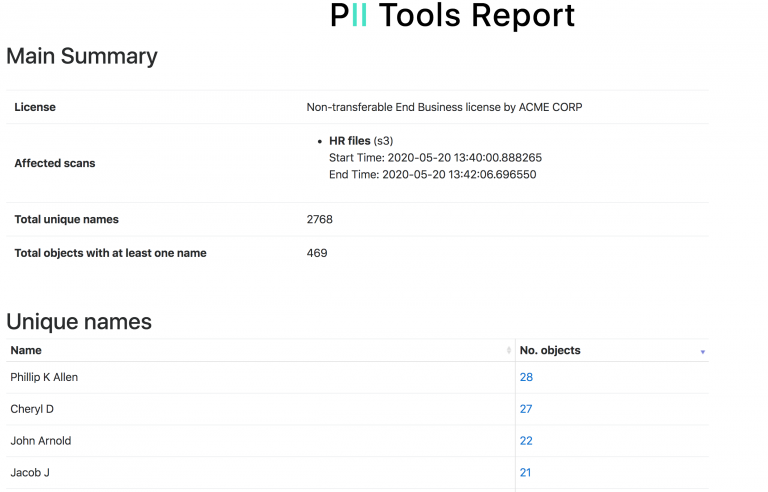
You’ve suffered a data leak, and the clock’s already ticking. Oh, and it’s a large dataset, too. Where do you even start to locate every single instance of PII involved? Let’s get into it! Breach Incident Scanner Discovering leaked sensitive information and PII by hand is completely unrealistic for large datasets, so automated solutions like PII Tools come in handy. … Read More
Exclude PII / PCI / PHI From a Breach Report
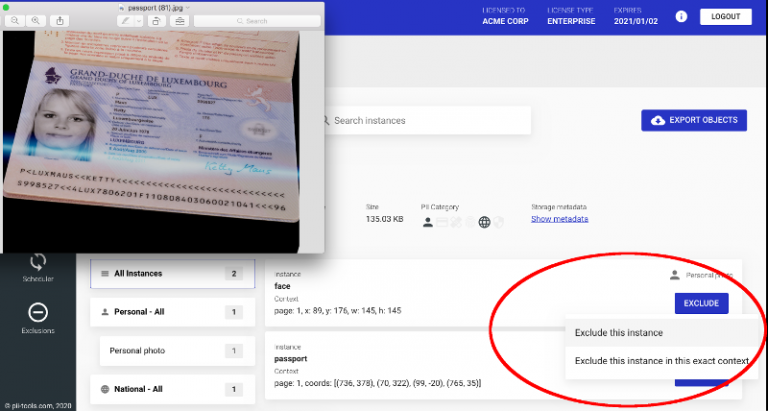
When responding to a breach incident, having a clear idea who’s affected and how is a matter of urgency. Manual discovery of PII information is tedious and costly, so automated solutions come in handy. But how to deal with false positives? PII Exclusions One typical task during a data review is removing unwanted data instances. PII Tools already automates PII … Read More





