As much as 90% of security breaches and data leaks are caused by human error. Follow these 5 Steps to hold your own employee training on PII Protection and Cyber Awareness.
Introduction to PII
Personally Identifiable Information, or PII, must be a household acronym for all employees. They need to be able to recognize it immediately, as well as show the ability to differentiate between less at-risk instances of PII and sensitive/personal data.
Start your PII Protection Awareness training by sharing the definition of PII: Any information connected to a specific individual that can be used to uncover or steal that individual's identity.
Next, explain the difference between Direct and Indirect Identifiers. Data like Names, Addresses, Telephone Numbers, etc., are all direct identifiers.
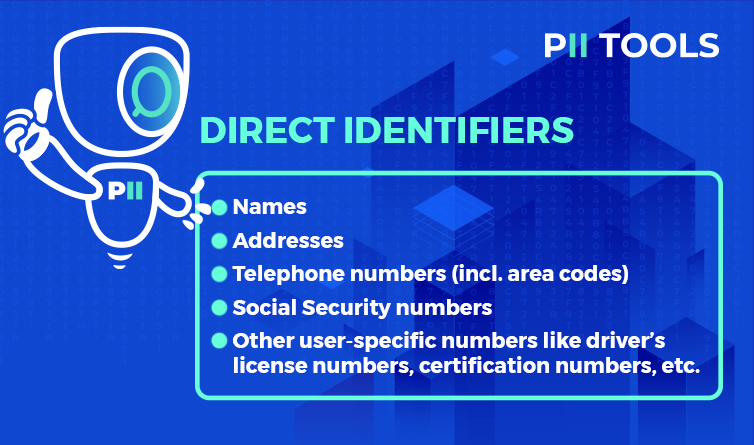
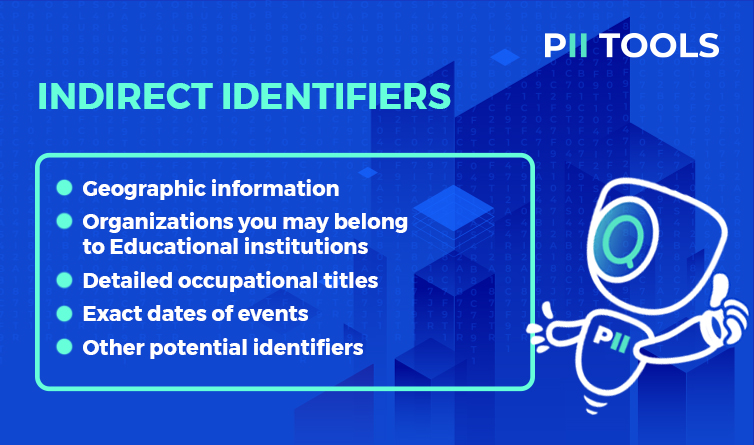
Meanwhile, event dates, occupational titles, and geographical information are indirect identifiers.
For additional teaching materials, refer to Part 1 of our The Complete Guide to PII.
Recognizing PII
With the Intro to PII out of the way, you can now test the employees’ ability to recognize PII where it stands.
We’ve prepared a full document with FREE downloadable PII examples to use in your employee training. You can go over a few examples with them, or simply jump right into a friendly game of Recognize the PII to ensure their comprehension.

And don’t forget about Direct and Indirect Identifiers. Present your employees with variations of PII instances, including obvious examples and some less notable instances.
Also, be sure to drive home the concept that a single indirect identifier may not be considered PII until grouped with other indirect identifiers that, together, make it clear who the data subject is.
Avoiding Cyberattacks
Employee security awareness is key to avoiding data loss via cyberattacks. Phishing emails, social engineering attacks, and PII-compromising malware are all common ways unsuspecting employees freely give away at-risk data.
We’ve prepared a few examples of phishing emails and other cyber-theft tactics your employees may encounter. See the image below as your first example.
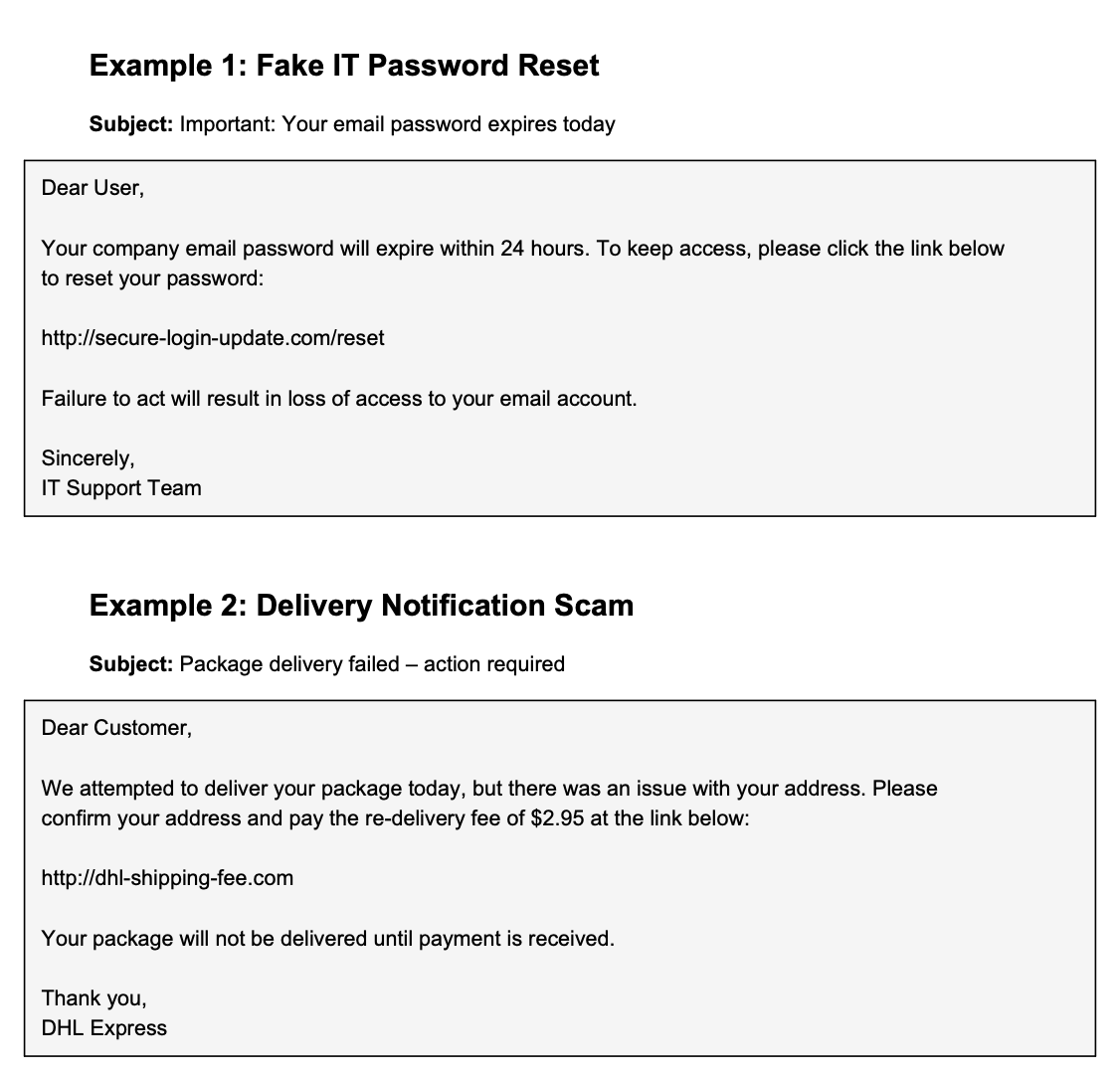
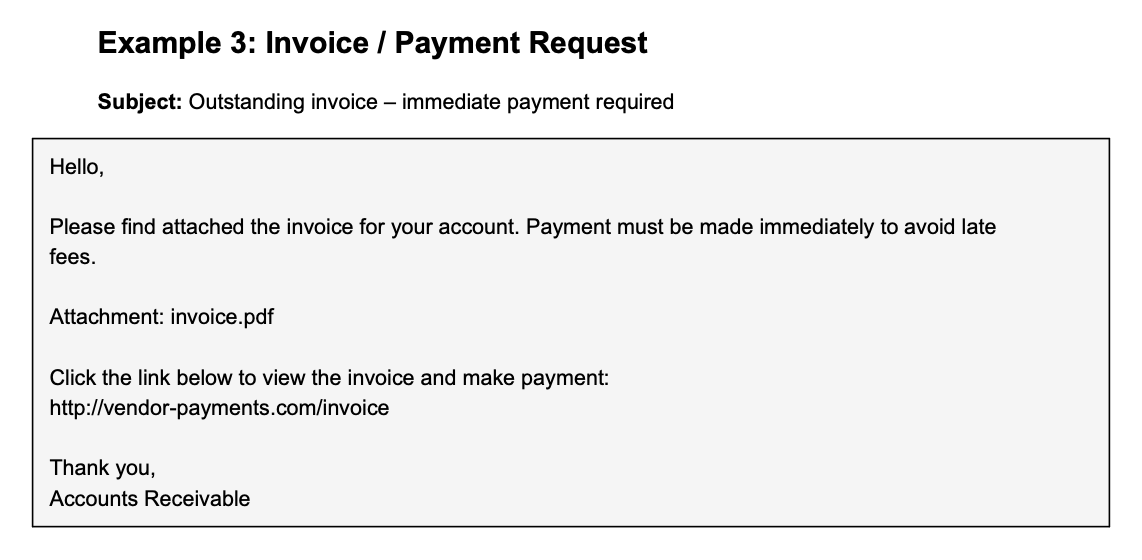
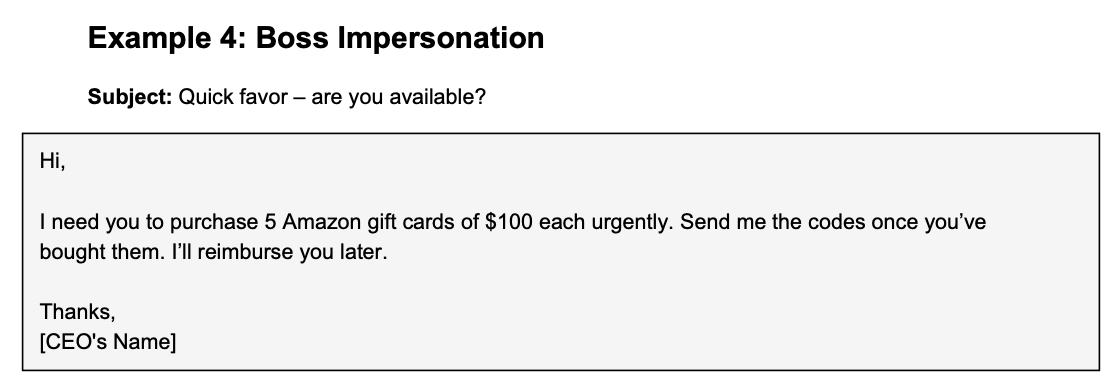
Ask the employees if they’ve ever come across any similar emails at work before, and how they chose to handle them. Then use the examples to play another round of Recognize the Phishing Email to ensure they never accidentally leak sensitive information.
Review Company Policies on PII Protection
Every organization that collects and stores potentially at-risk data needs to establish company-wide policies that cover everything from its creation all the way to its eventual deletion.
Guide the employees through your company's policies on PII protection, highlighting their individual responsibilities and accountability. This would also be a great time to dedicate leadership roles in enforcing PII protection by selecting a few reliable employees to oversee the others.
Those in leadership positions would also benefit from additional PII protection training, depending on your company’s policies and expectations. For instance, such a role may involve a new position or a pay raise, which each organization must address individually.
PII Scanner Training
The final step of your employee training should focus on how to use sensitive data discovery software, also known as a PII scanner or PII detector. Where human error is to blame for the vast majority of data leaks, such tools can help to plug up the holes.
Let’s use PII Tools Data Discovery as an example. Based on worldwide data protection regulations (GDPR, PCI DSS, HIPAA, etc.), PII Tools scans for all personal or sensitive information securely within your company’s network.
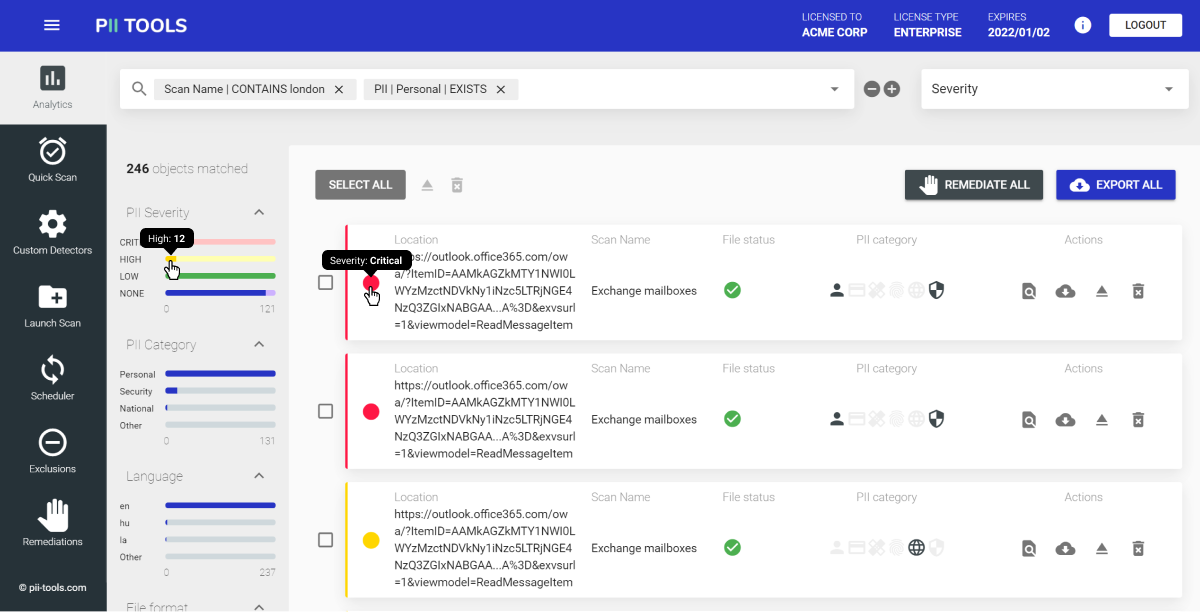
Once the scan is complete, authorised employees can review the reports to see exactly what and where at-risk PII is being stored and how urgent the situation is. PII Tools then offers various remediation options to ensure the sensitive data ends up in a secure location.
Another useful feature that employees can use is the PII Tools AI Data Protector. This tool scans company data before it's used in any third-party AI models. That means employees can continue to work efficiently with help from AI tools without accidentally leaking any sensitive PII along the way.
Employee PII Awareness
These 5 simple steps are all you need to put on a successful and easy-to-follow employee training on PII Protection.
By eliminating the common mistakes employees make, you’re company and client data will stay safe and secure. And the result is regulatory compliance and a brand users can trust with their PII. Happy training!
Equip Your Employees with the Best Tools Possible! PII Tools: Intuitive & Easy to Use!





