The final entry of our 3-part PII series. Learn how to protect your PII in this article, and see also Part 1: Identifying PII and Part 2: PII vs Personal Data.
Part 1 laid the foundation for understanding and identifying PII, while Part 2 taught the differences of personal data with practical examples. Now it’s time for the final entry in the series: Part 3 – Protecting PII.
PII Protection Rights
Despite how common it may feel today to give out information about ourselves, all of us bear an innate right to keep our PII private. And if we do choose to entrust it with someone or some company, we still keep the right to have it protected.
PII, personal data, sensitive information, and more can all be safeguarded in various ways and by various governing bodies around the world. Let’s dive into some of the most common ways personal information is protected today.
PII Regulations
The most obvious answer to any data protection question typically starts with regulations. We’ve likely all heard of the most prominent directives like the GDPR and HIPAA but there are so many more.
Each deals with a specific country or region or a certain type of PII. For instance, the General Data Protection Regulation (GDPR) handles information privacy in the EU, while the Health Insurance Portability and Accountability Act (HIPAA) protects people’s healthcare information in the US.
Then there’s the CCPA in California, the PCI DSS, the LGPD in Brazil… the list goes on. Although it may seem like a lot at first glance, these regulations ensure users’ PII is collected and stored safely and ethically. They’re the reason you feel comfortable entering your credit card details on Amazon or why you don’t think twice about telling your doctor exactly where your rash itches.
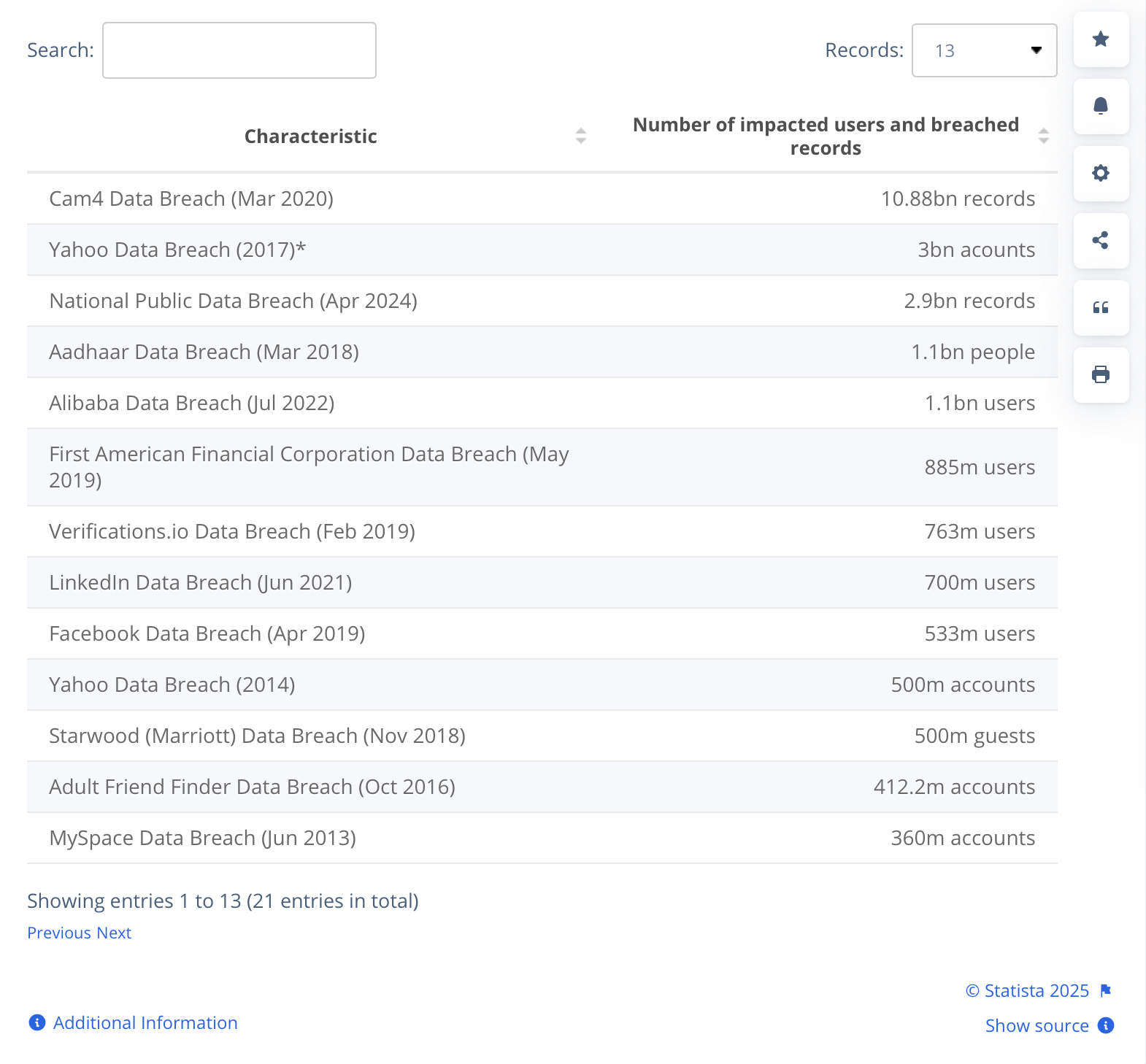
PII Data Breaches
In a perfect world, these regulations would be all we need to keep our data safe. Unfortunately, this isn’t a perfect world, and data breaches seem to almost be commonplace today. 422.61 million data records were leaked in data breaches in the third quarter of 2024 alone!
Whether the information is maliciously stolen by hackers and online thieves or, more commonly, accidentally leaked by an unattentive employee, data breaches are an unfortunate part of our lives.
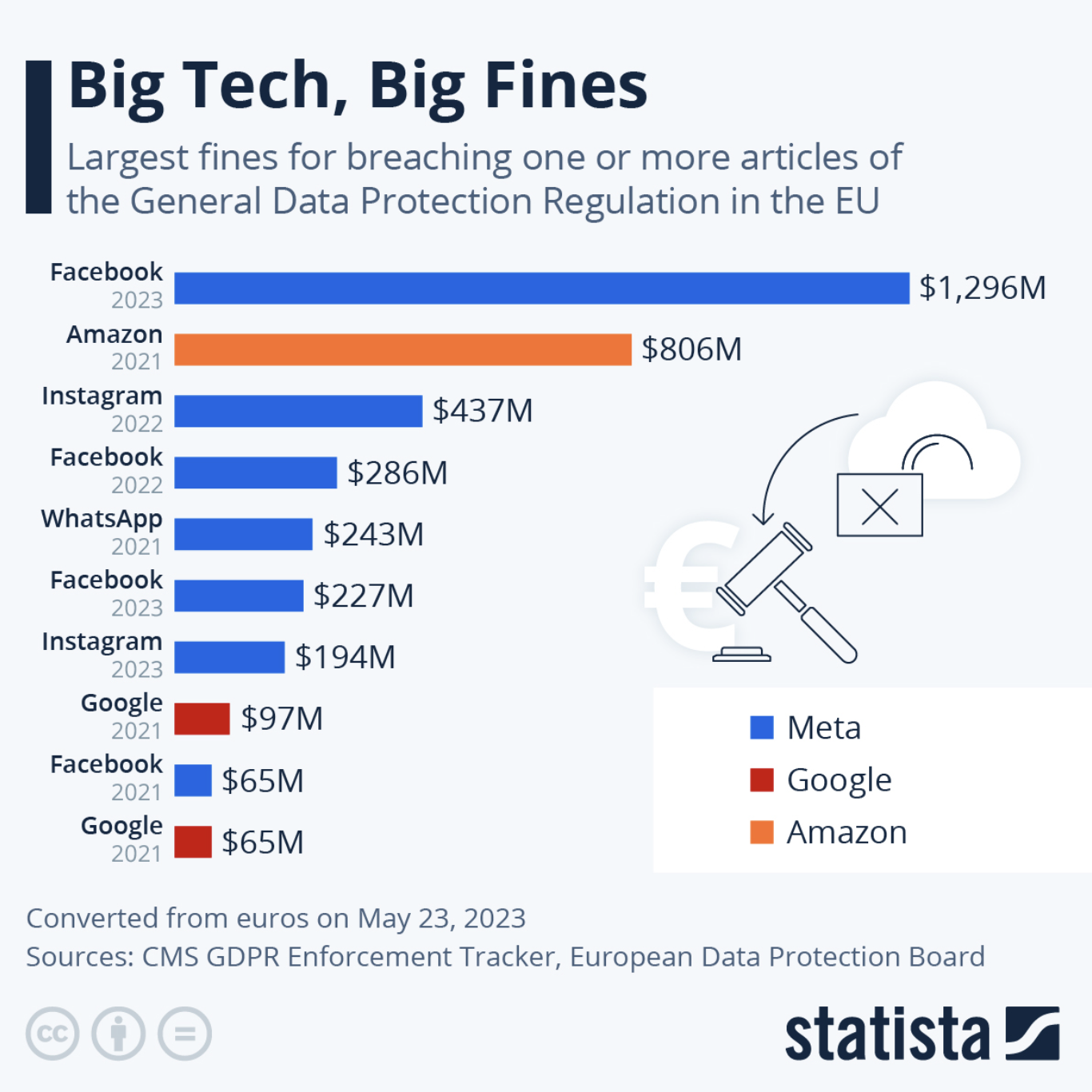
However, there are consequences for companies that leak PII, ranging from enormous fines in the hundreds of millions of dollars to federal charges. These sorts of repercussions force those storing users’ PII to better safeguard this data and take greater care when providing access to it.
Data Anonymization and De-Anonymization
Another way to protect PII is via data anonymization and de-anonymization. In short, anonymization is the process of masking users’ information as they transact in various fields, such as health services, social media, e-commerce, etc.
This information is encrypted to protect it as it passes between machines, or certain information is deleted to render what remains non-PII. However, this process isn’t bulletproof.
De-anonymizing data reverses the work done by anonymization by matching shared sets of data that have been stripped of PII with other easily accessible data sets found online. In this way, data miners can combine and connect information until they arrive at someone’s personal identity or transaction history.
With this in mind, it’s always best to safeguard any PII you may be sending with the best anonymization tools possible. But the first step to protecting your PII is to arm yourself with knowledge, which is exactly what you’ve done by reading this 3-part series.
Now, only one question remains: Why is PII even worth protecting?
Why is PII Important?
As mentioned at the start of this article, everyone has an innate right to their own private information. This right was the very inspiration for this entire series. And that right then carries over to the companies that collect, store, and sell PII.
Any time you buy something online, sign up for social media, or fill out a contact form, you’re giving your PII to someone else. It’s then up to the companies to store that PII in a secure location, to protect it from hackers, data leaks, or even from being misused in-house.
Keep that in mind the next time you sign up for that “free” newsletter or give your credit card information over the phone. Or if you work for a company that handles PII, it’s up to you to ensure the information entrusted to you doesn’t fall into the wrong hands.
And why’s that? Easy. Because it’s the right thing to do.
You Can Only Protect What You Can Find. Make PII Data Discovery Easy & Automatic with PII Tool Data Discovery Software!





