With technology progressing and changing every day, it can sometimes be difficult to keep up with the times. As a business, however, falling behind can mean letting important (and legally binding) information fall through the cracks, disappointing customers and losing the trust of business partners. This is where sensitive data discovery tools come into play. But what exactly are they and how do they work?
Intro to SDDTs
Every company holds sensitive data in one way or another. Whether that data is strictly related to the company’s employees, clientele, or both, a number of rules and regulations pertains to it. Most likely we’re all familiar with GDPR and HIPAA, but these acronyms go as far as CCPA, LGPD, or PCI DSS*. The only way a company can ensure none of the data it holds is in violation of any of these standards is to use a Sensitive Data Discovery Tool (SDDT).
An SDDT—also known as a PII scanner or PII detector—is a type of software that a company runs on its systems to locate and remediate personal data, to comply with its internal guidelines as well as the regulations mentioned above. For smaller companies, the need for specially written software just to search their personal information may seem like overkill. In these cases, as well as in years past, the only option available was to manually search for any data discrepancies or subject access requests one by one.
Thankfully, this process can now be automated, which absolutely comes in handy for medium to large business owners (small business owners are sure to appreciate the accessibility as well, of course).
When do SDDTs come in handy?
Automated discovery is essential in a number of scenarios, including:
- Data Audits – whether preventive, as a part of a certification effort, or as a response to a past data breach, understanding the risk within your data is a must.
- Subject Access Requests – any individual can ask for the report on their PII at any time. Do you know where all their data lives within your company's systems?
- Remediation – again, either as a part of a breach incident response, or a general inventory cleanup.
- Data Migrations – understand the risk in legacy data, before migrating it into the cloud.
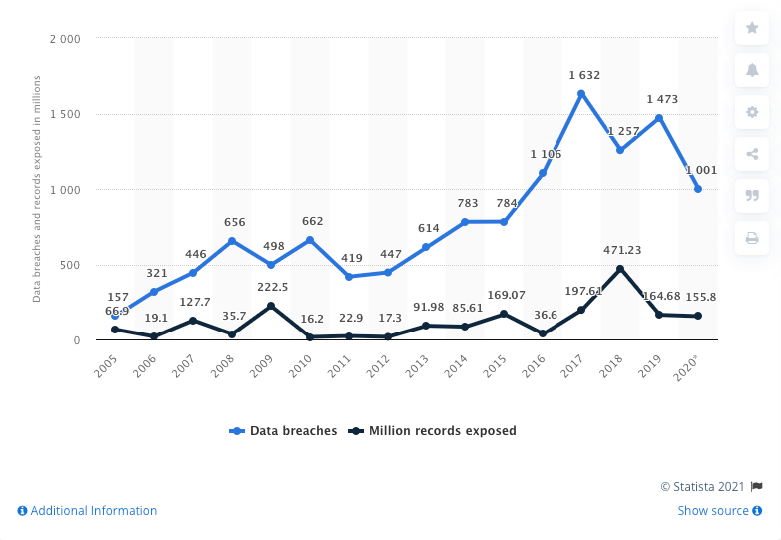
Annual number of data breaches and exposed records in the United States from 2005 to 2020 (in millions)
Source: Statista website
PII Scanner Use Cases
Apart from scanning your data, an SDDT can be useful in a number of other ways, for instance, auditing. Whether you run an auditing company or are preparing for an auditor’s visit yourself, an SDDT can automate this process for you.
Another useful feature would be ensuring only the designated people have access to certain information. For larger companies, new people are coming and going every day, being added to new and ongoing projects, with employees constantly sharing information through file shares and emails. With a PII detector in place, you can check in and see exactly what data exists where and who has access to it, and if you’re unhappy with the results, take care of the issue right away.
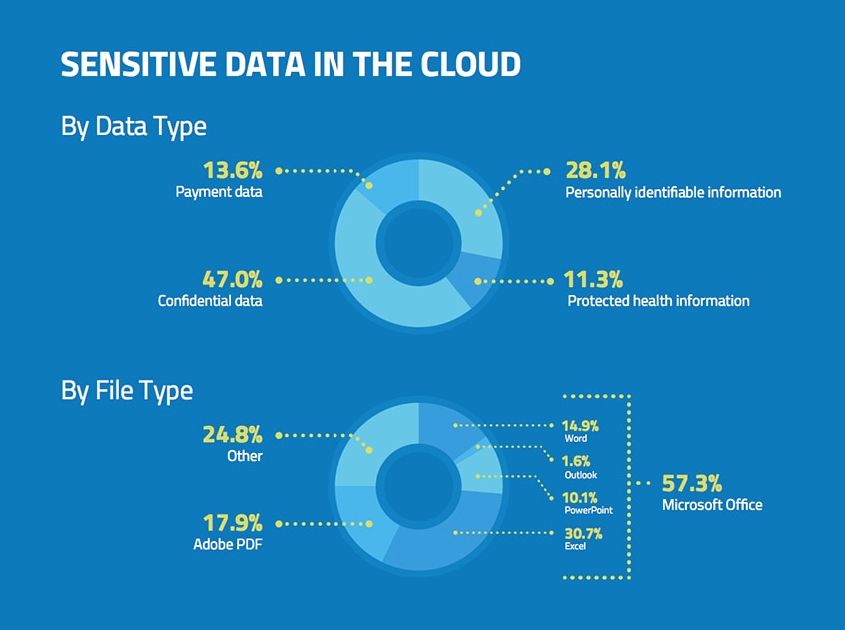
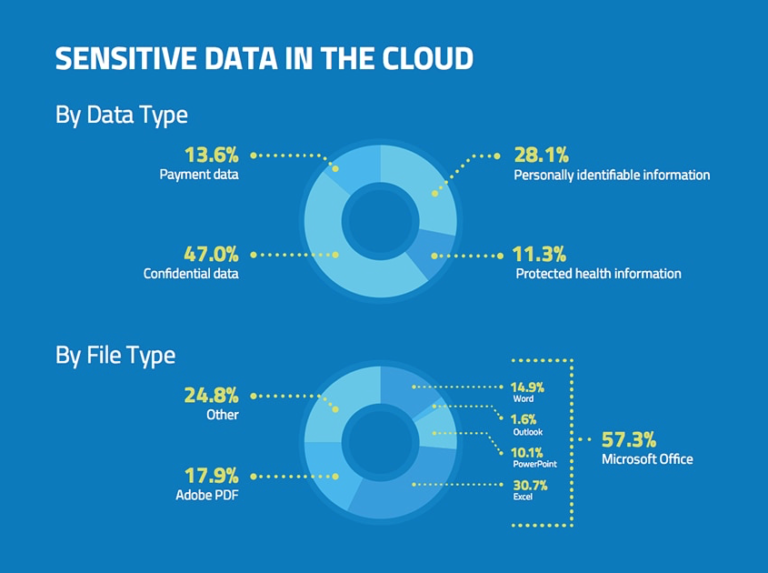
Source: McAfee
PII Tools with Plenty to Offer
The benefits of SDDTs are numerous and far-reaching. As can be expected, PII Tools makes as many of these assets available to you as possible. Besides the applications already stated above, this PII scanner also makes a point to automatically filter, review, and organise your PII analytics dashboard, implement precise AI detectors, and provide support for breach incidents.
However, one of the most sought-after features in their arsenal is the ability to scan all of your company’s systems (including employee workstations and laptops) in continuously. Not only can PII Tools scan and correct all of the data you have up to this point, but this PII scanner also does the same for the data arriving in your system over time, with delta scans. In this current world of lightning-fast connections and remote workers, this feature couldn’t have come at a better time.
Modern Solutions to Tomorrow’s Problems
It’s obvious now that mitigating business risk with sensitive data discovery tools is a must for any successful business. The fact that this can be implemented using a PII detector, in a fully automatic fashion and completely replace the previous manual discovery techniques is invaluable.
The times of "unexpected" data loss are gone, and now are the days of continuous data storage monitoring and comprehensive compliance facilitation. PII Tools can do all this and more. Don’t miss out on the chance to protect and enhance the data security of your company today.
Questions? Want to see a live demo? Get in touch.
* California Consumer Privacy Act (CCPA), Payment Card Industry Data Security Standard (PCI DSS), Brazil's Lei Geral de Proteção de Dados (LGPD). ↑ back