Suffering a data leak can be devastating. Depending on the size of your company and the amount of data you store, a single data breach could signal the end of your business. And with the number of data leaks only on the rise, it’s time to implement prevention’s best practices.
Data Leaks
Although we’ve all most likely heard of dangerous data leaks in the news, it’s important to know exactly what a data leak is and the effects it can have on you and your company. Simply stated, a data leak is the intentional or unintentional release of secure or private information to an untrusted environment.
As for the impact of having your or your company’s data breached, those can be hard to pin down. Everything depends on the size of the leak, what and whose information was leaked, and the ramifications of that data falling into the wrong hands.
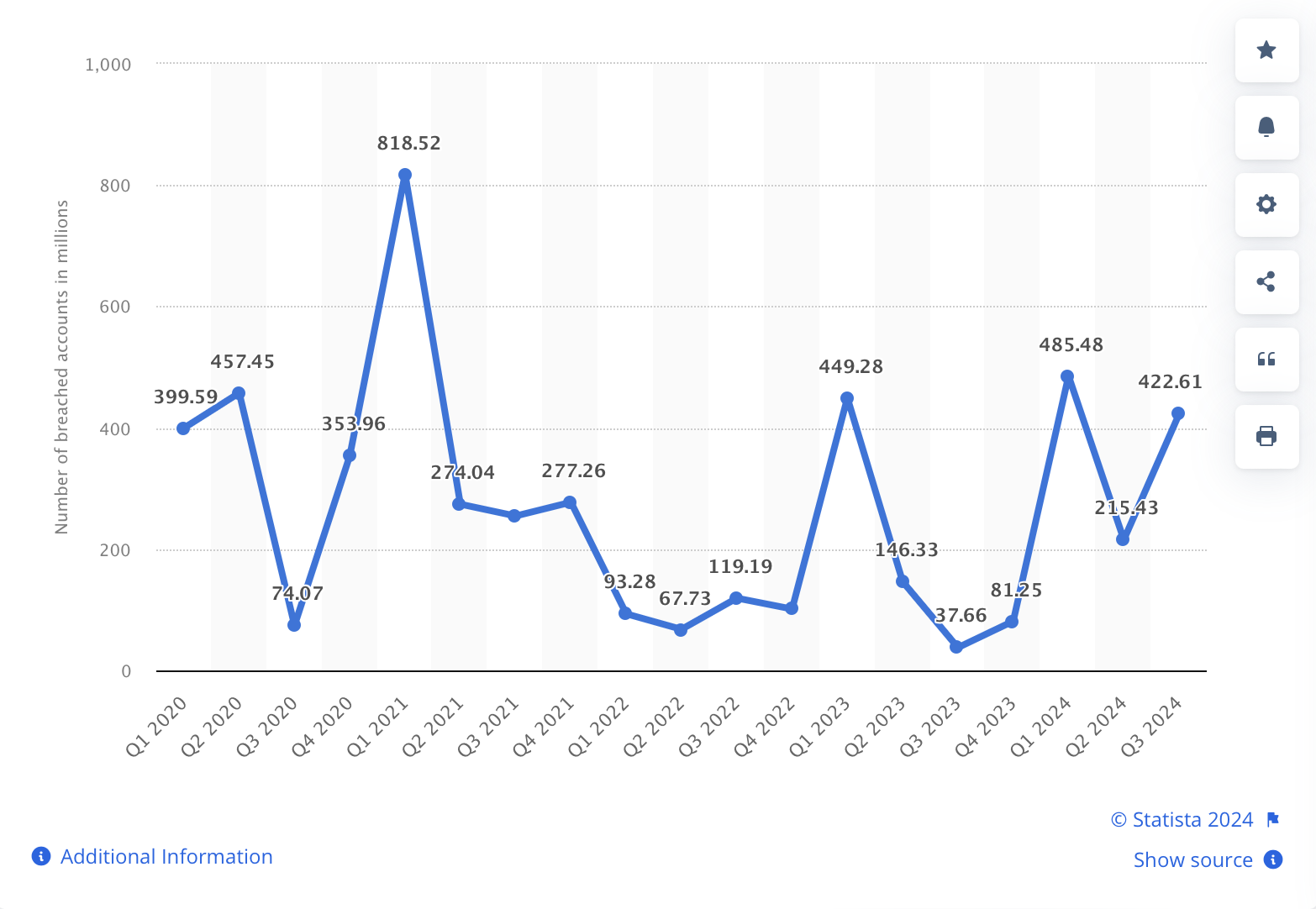
Source: Statista
The Aftermath
For many business owners, the worst consequence of a data leak is financial. Not only has the cost of a data leak increased 12% over the past five years, but you could also be fined as much as 4% of your annual global turnover or 20 Million Euros, whichever is greater. A single data leak could spell financial ruin for your business.
Unfortunately, there are many other negative impacts of data leaks, including the loss of your clients’ trust, legal action taken against you, as well as your sensitive data being sold to or used by people wishing to do you harm. Luckily, there are a number of things you can do to prevent data leaks from ever happening.
Step 1 – Audits
The first, and possibly most important, step of data leak prevention is performing regular, in-house audits of the PII, sensitive data, protected data, etc., in all your storages. To do so, you’ll need either a professional auditor or your DPO (Data Protection Officer). It’s their job to sift through the data in your company and ensure you don’t have any vulnerable information stored in some old file you forgot about long ago.
Step 2 – Assess and Remediate
After having discovered any non-compliant information or at-risk data, it’s time for the second step of data breach prevention. You now need to access and remediate problematic data. Again, your DPO or auditor will need to analyze the issues they discovered according to its severity, content, and context. From there, they can easily remediate (report, delete, quarantine) the at-risk data, moving it to a more secure location.
Step 3 – Employee Training
The third and final step involves your employees. Employees and third-party contractors are the number one cause of data leaks. The best way to prevent your employees and contractors from leaking data, whether on purpose or by accident, is to hold regular security trainings and ensure everyone is aware of the current regulations and risks. Also, just to really cover your bases, you can implement any combination of restricted end-user access, unique passwords, key cards, policy creation, and so on.
The Right Tools for the Job
Now that we’ve covered the basics of data leaks and learned a few best practices for preventing them from happening, you’re going to need to equip your DPO or auditor with the means for executing these steps. This is where PII Tools software will make your life better and your company data more secure.
PII Tools is the easiest solution for data audits and regulatory compliance. This AI-driven software performs data scans with +99% accuracy. Now you can discover any problematic or non-compliant data, access its security risk, remediate the issue, and remain up-to-date on the ever-changing regulations.

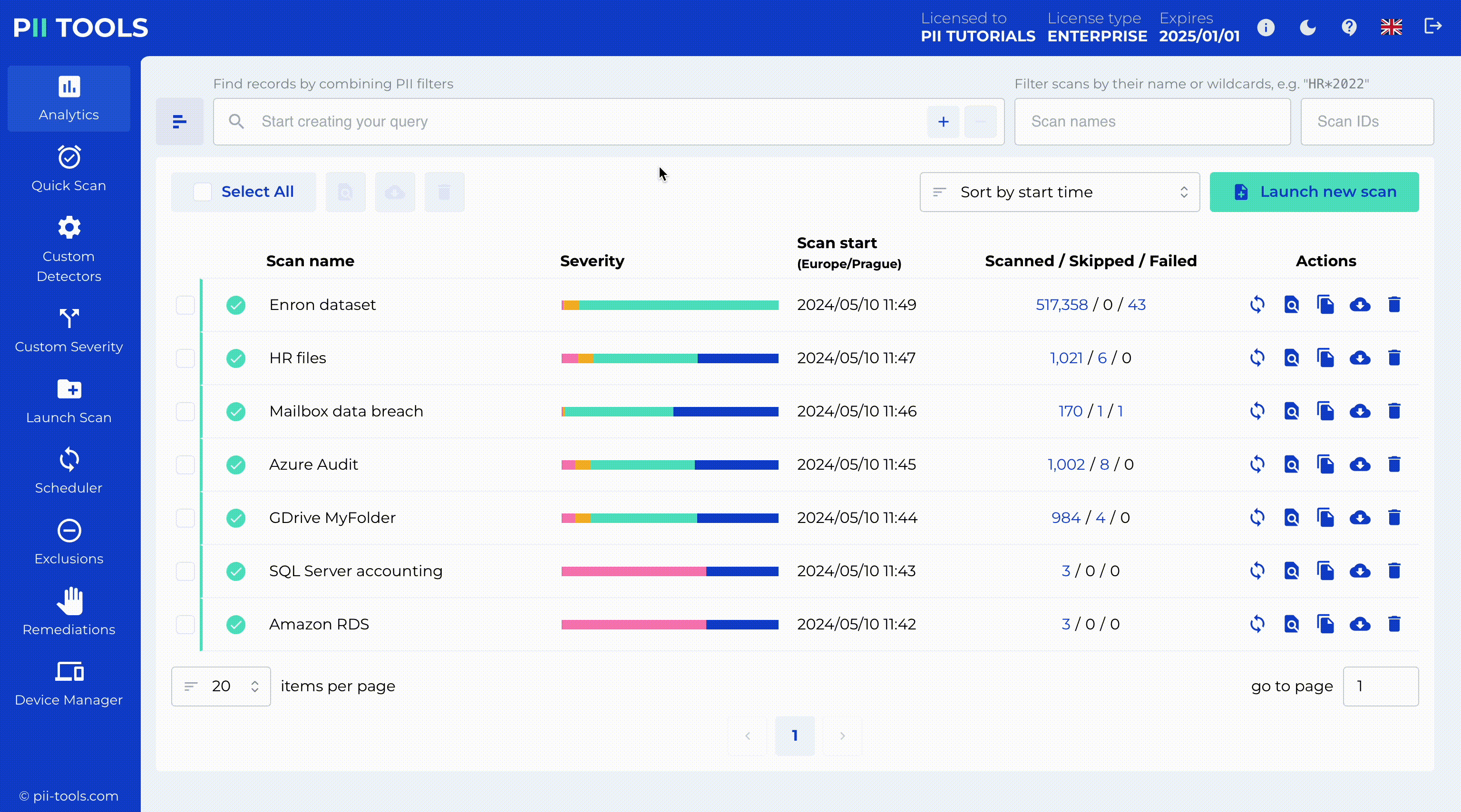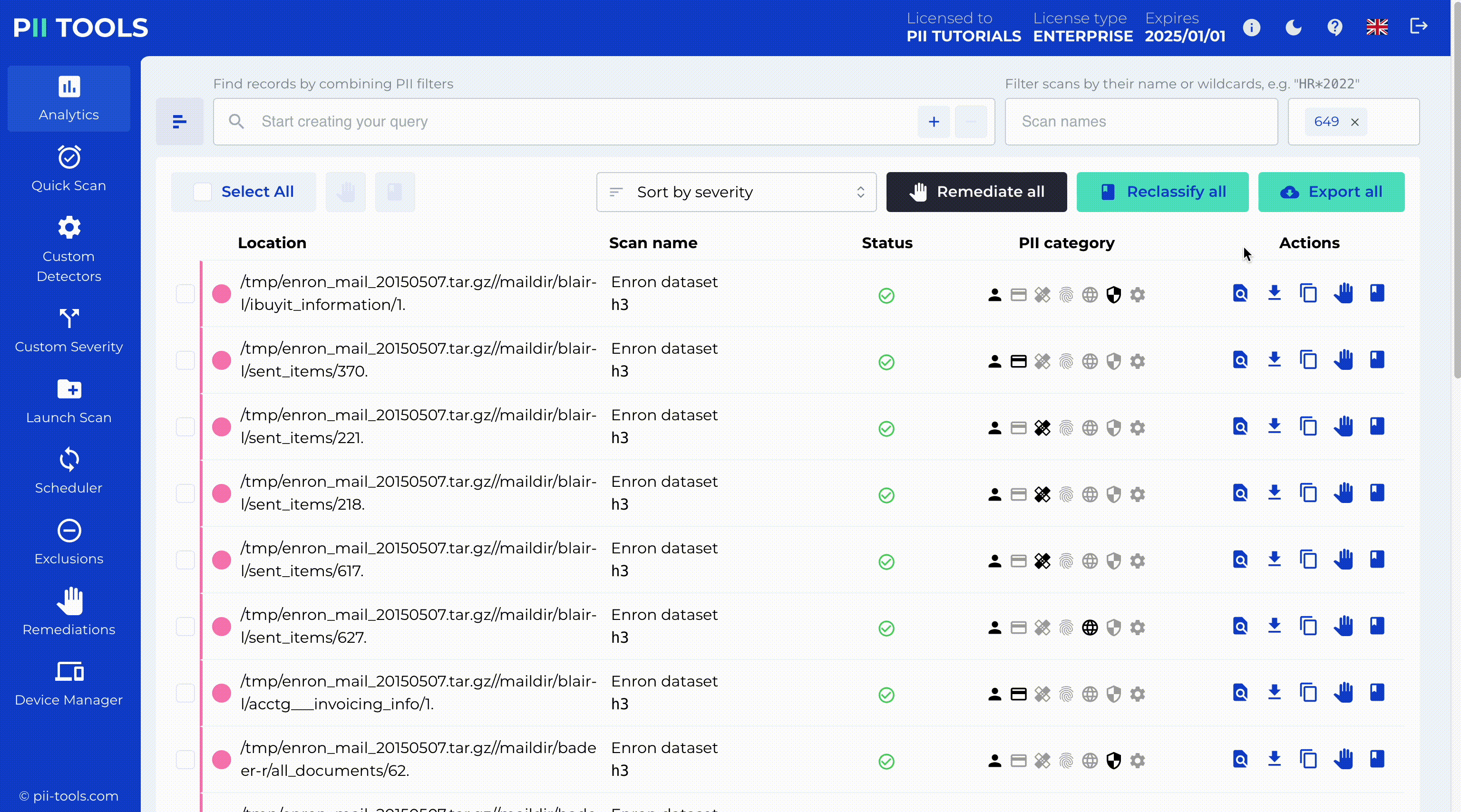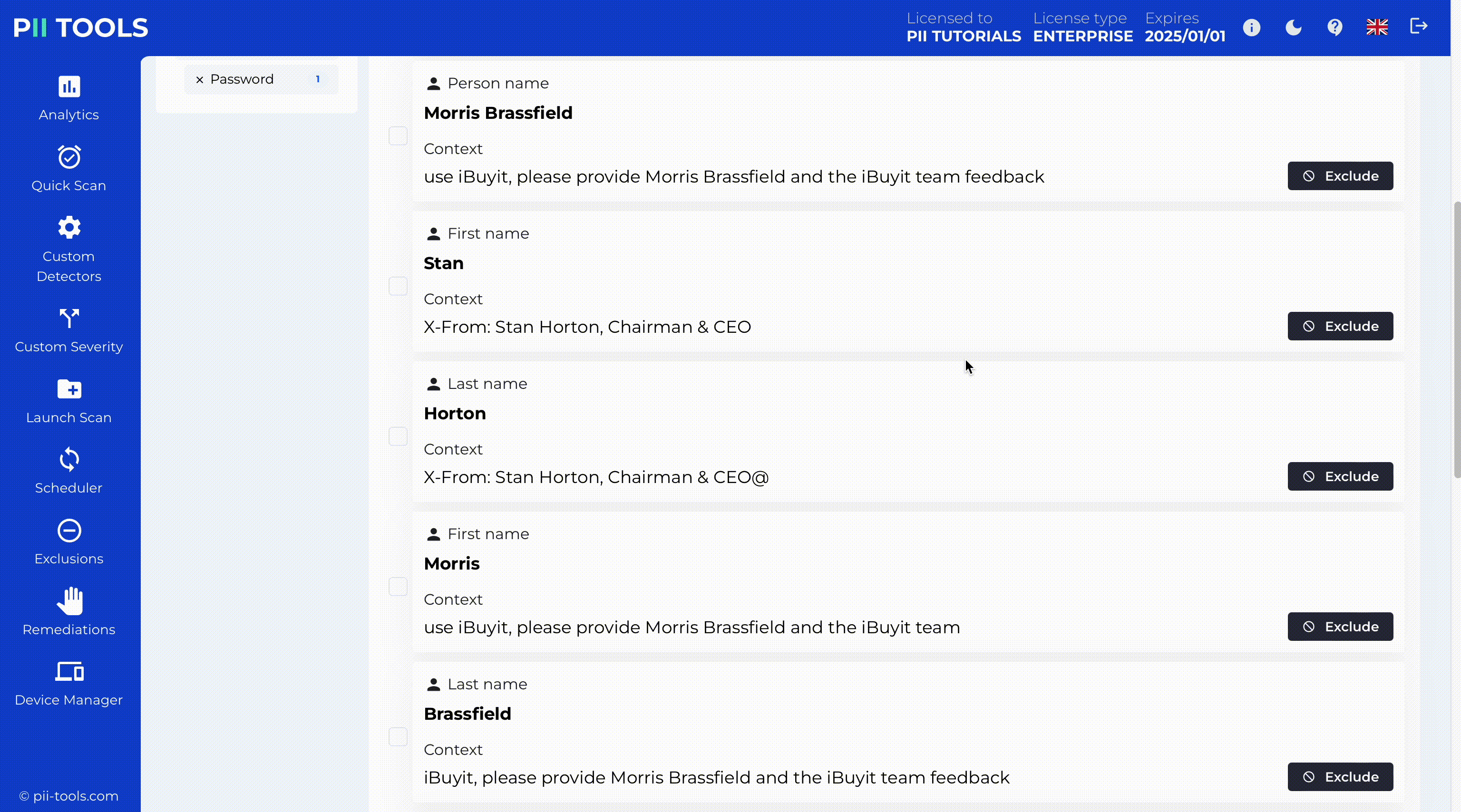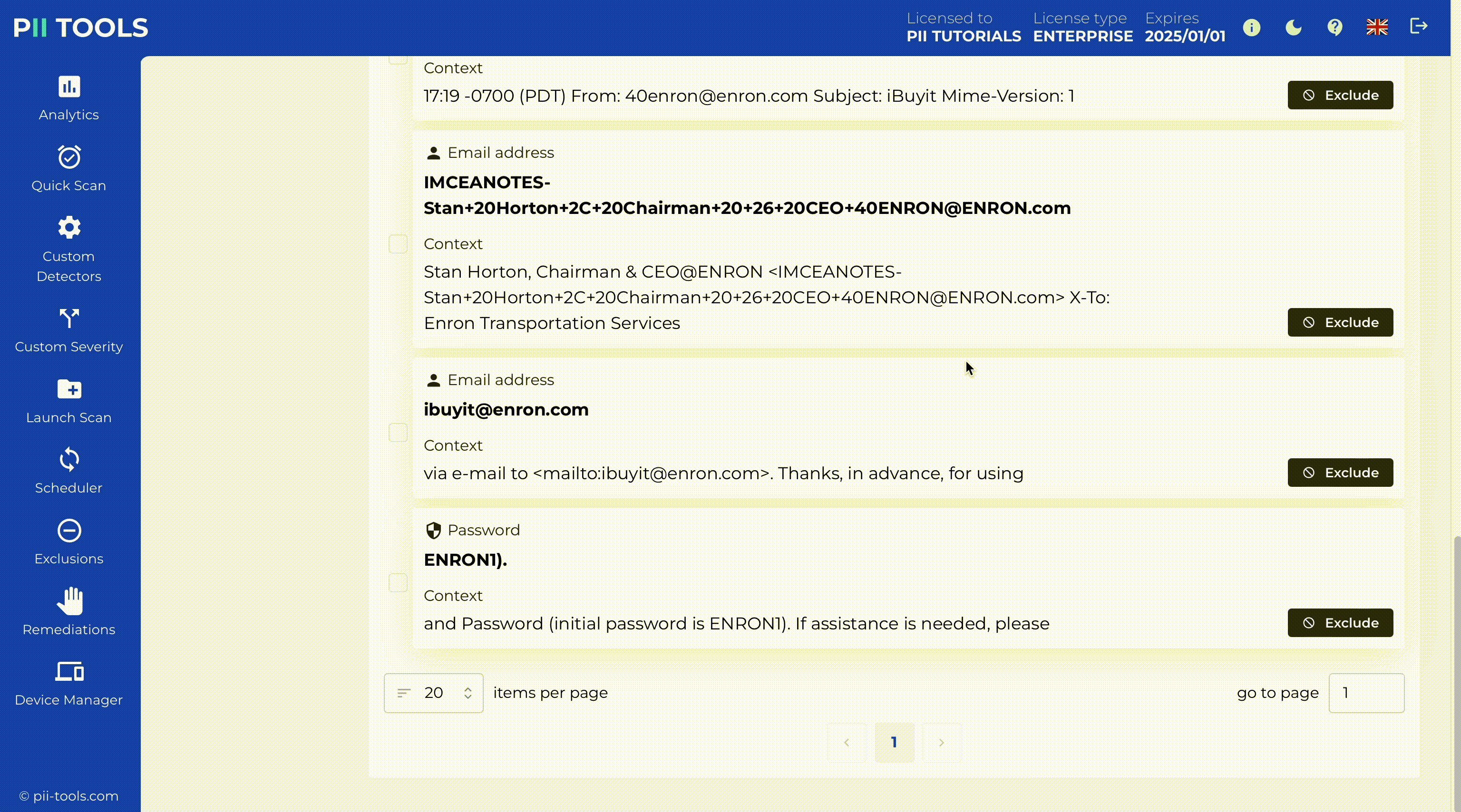
Source: PII Tools
Data Leak Management
Even after all this, however, should you still suffer a data leak of any size, PII Tools has got you covered. When your DPO or auditor uses this solution, they can react quickly to identify the affected data, analyse millions of leaked files or emails for any form of PII (including PDFs and images), generate detailed, interactive reports, and recommend actional steps to prevent this type of data leak going forward.
Sometimes, the best offence is a good defense. Don’t let your business undergo financial ruin while losing your hard-earned reputation at the same time, all because of a data leak. Utilize PII Tools today and protect your company from the start. And, should the unthinkable happen, allow PII Tools to mitigate your data leak and get you back on track as soon as possible!
Looking to Upgrade Your Company’s Data Protection? Learn How PII Tools Helps With Data Leak Management!





