“Hope for the best, prepare for the worst.” With billions of data records stolen and lost every year, these words ring truer every day. But can you ever really be “prepared” for a data breach, or are we all just waiting for the second shoe to drop?
Inevitability
Regarding data breaches, it seems the questions are more “when will the next one happen and how bad will it be?” instead of anything starting with an optimistic “if”. In layman’s terms, a data breach is a security violation where protected data is viewed, stolen, or accessed by an unauthorized party.
Any company that collects and stores sensitive information about its employees, customers, or users is responsible for protecting that data from breaches. And that’s no easy task, especially when literally every one of our online clicks and keypresses is logged forever in a database somewhere.
Data Privacy Compliance
The three Cs perfectly illustrate the number one step to being prepared for a data breach. They’re better known as Compliance, Compliance, Compliance.
Some misguided folks might look at compliance regulations as stumbling blocks, but anyone who cares about data breach prevention knows that nothing can keep them and their company out of deep water like complying with the GDPR, HIPAA, PCI DSS, etc. Not to mention how this benefits their users.
Regulatory compliance is like pulling Excalibur from the stone the moment the fire-breathing, data-stealing dragon starts attacking the town. For example, suppose you’ve followed all the guidelines for collecting, storing, and protecting sensitive, private, and confidential information. In that case, you’ve already removed countless instances of potentially damaging data getting into the wrong hands.
Simply put, it’s never good to suffer a data breach. But if one does occur, it’s incalculably better to leak 100% regulation-compliant data than all of your users’ social security numbers and health records.
Data Breach Prevention Plan
After you’ve paid compliance the attention it deserves, you’re going to want to shift your focus toward establishing a Cybersecurity Policy. Essentially, this policy lays the groundwork to reduce the likelihood of a data breach. Think of it as a “data breach prevention plan”.
But every company is different, as is the complexity of its Cybersecurity Policy. Some businesses are large enough to create an entire task force ready to spring into action the moment a breach hits, while others don’t require as much intensity.
Whatever your situation, the items below are great jumping-off points for creating an effective data breach prevention plan.
These are the preparatory steps that could pay dividends down the line. And they also lead us to our final tip on preparing for a data breach: Discovery.
Automatic Data Discovery
Even after you’ve invested the time and effort to enact all the procedures and policies listed above, you’re still vulnerable to a data breach. And you’ll never truly be prepared for one unless you have the tools to detect and respond to it.
Luckily, we’ve already gone into detail on this topic in our article How to Identify Leaked Data. But to give you a quick TL;DR, the fastest and most reliable way to manage a breach incident is to deploy a sensitive data discovery tool.
These discovery tools can be used to analyze millions of breached files or emails for all types of PII in seconds. Often, they also offer automatically generative reports with interactive features, allowing your Data Response Team to clearly see all the damage and any “red-hot” areas that require their immediate attention.
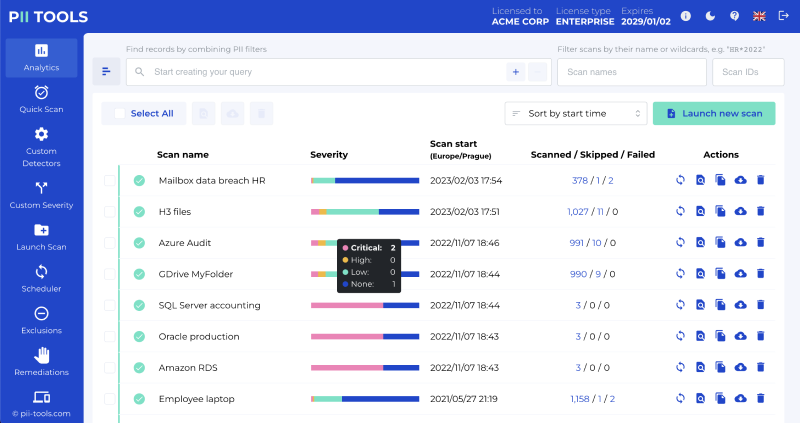
If you’re interested in taking a deep dive into data breach reports and how you can actually create your own, we’ve prepared a step-by-step guide on using the PII Tools software to do just that.
Control over Your Data
For any company, data breaches can be pretty frightening, and rightfully so. But in many cases, it’s the users or customers who are affected the most. For example, it’s safe to say that anyone with a Facebook account has had their data leaked by this point.
That means it’s our job to take the necessary steps in advance to prevent data breaches and their negative impact. Nothing is more effective in achieving this goal than compliance, followed closely by implementing the right cybersecurity policy and data discovery software.
We never feel 100% safe from the threat of data breaches, but the amount of harm they cause is entirely in our hands. An efficient and thorough response to a data breach can mean the difference between protecting and maintaining your clientele or losing your users’ trust forever.
Are You Prepared For a Data Breach? Take the PII Tools Demo Now and Instantly Discover All At-Risk Data!




