$4.44 million. That’s the average cost of a data loss instance in 2025. Unless you’ve got that kind of cash just lying around, taking steps toward Data Loss Prevention will be your best option. But who’s keeping your data safe?
Intro to Data Loss Prevention
Before you get anywhere near avoiding that 4-million-dollar “hit” to the yearly budget, you first need to understand the basics of Data Loss Prevention, or DLP for short. To put it plainly, DLP is defined as “the practice of detecting potential data breaches and preventing them by monitoring, detecting, and blocking sensitive data while in use, in motion, and at rest.”
Given our modern era, we’re likely already hyper-aware of data loss and its effects on the company that suffered it and – more importantly – on the users whose potentially private information (PII) is now being held hostage or simply floating through the void, vulnerable to any potential attackers.

DLP in 3 Basic Steps
The topic of Data Loss Prevention could easily fill the pages of an entire novel. But all that information and various statistics can be boiled down into three basic steps that every executive, Data Protection Officer (DPO), and IT administrator should be practically experts on.
Step 1: Data Discovery
Any company storing data will have a hard time protecting it if they don’t know where it’s located. That’s why step #1 is quite simply Data Discovery.
All corporations and organizations that store any amount of client/employee data need a well-defined, clear data discovery plan. And this plan is typically led by a DPO, who implements some form of Data Discovery Software to sift through the mountains of 1s and 0s.
Luckily, they don’t have to go through the data discovery process alone. Useful tools like Person Cards® help by scanning their storages and automatically linking up all of the PII, PCI and PHI into rolled-up reports to be exported into a spreadsheet for easier import into other eDiscovery platforms as needed.
When choosing the right sensitive data discovery software, you should also ask yourself the following two questions:
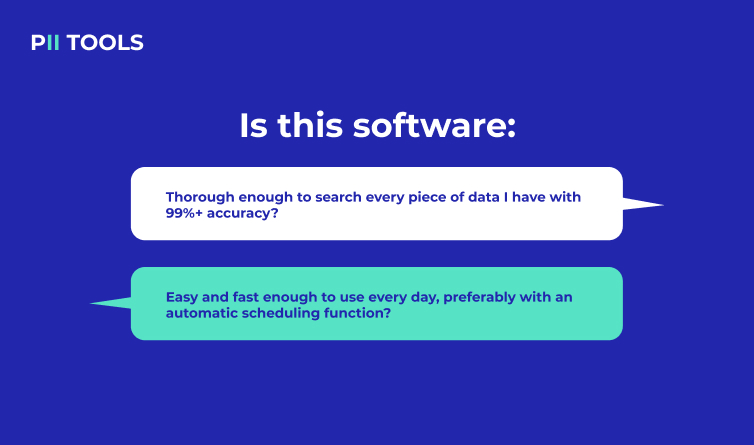
Step 2: Data Risk Assessment
Once you’ve selected a software (for additional help, read Top Features to Look For When Comparing Data Discovery Tools), the following step is to perform your first scans and go through all its discoveries. Any quality software should provide you with an easy-to-read review of every instance of potentially at-risk data that it could get its hands on.
In the beginning, you’ll likely run into loads of information that’s not really at-risk at all or false flags. Because data discovery software is trained to look for all instances of PII, it will likely flag emails with people’s names, even though it’s just your coworker’s automatic email signature.
Here’s where you’d hope the software you’ve chosen allows for Custom Detectors, meaning you can tell the software all the information that’s okay to overlook, saving you both time and money.
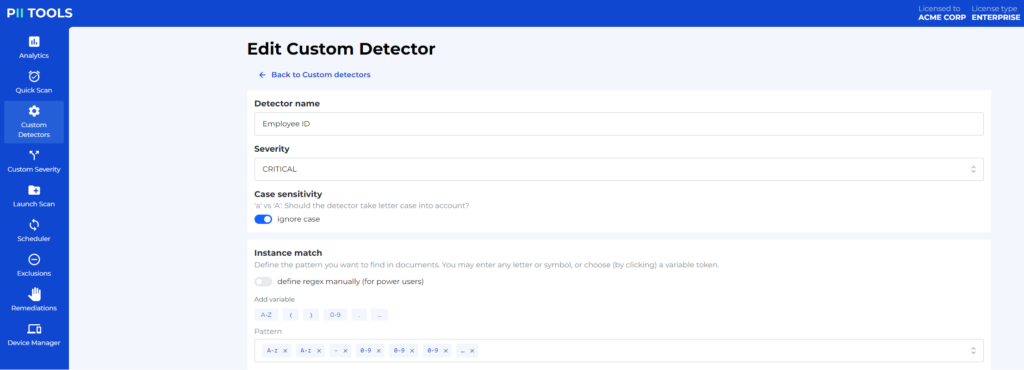
During this phase, you’ll also want to review all instances of true red-flag data. This could come as a simple mistake when someone filed Jane’s medical history in the wrong folder or something more nefarious, like an external breach or even a disgruntled ex-employee whose authorization credentials have yet to be revoked.
Step 3: Remediation
Now that we’ve discovered the data and reviewed each at-risk instance, the final step is to remediate all those red and yellow flags.
Any data discovery software should offer remediation options for all kinds of different scenarios. You may only need to move the discovered data to a more secure location, or you may need to fully liquidate that data and ensure it’s never accessible again.
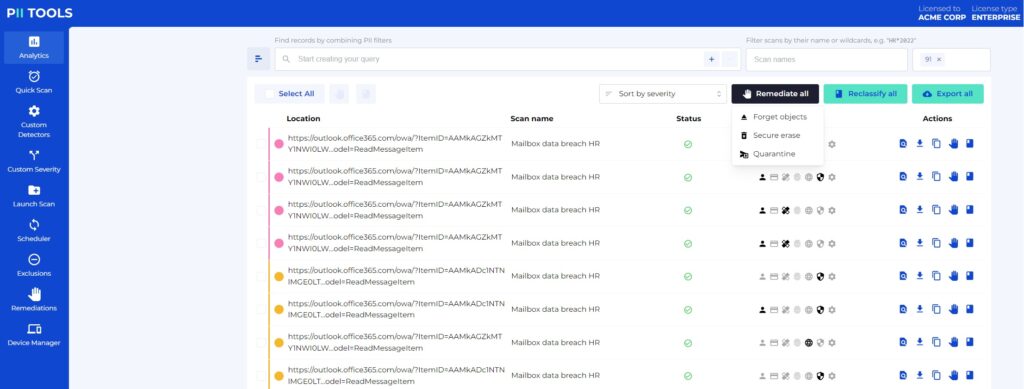
The way you choose to handle each instance can depend on several factors. For example, different countries are expected to uphold different compliances. Also, your company might advocate for specific data security procedures that other companies choose to overlook. Plainly stated, remediation is the step where you clean up any at-risk data, thus limiting the potential for data loss and breaches.
DLP + Regulatory Compliance
Preventing data loss isn’t only meant to save you and your company from that estimated $4 million. Securely storing all client, employee, and user data and taking every precaution to safeguard it forever provides a level of safety that all people deserve.
Be the kind of company that people can trust. Not only will it do wonders for your reputation and ensure your regulatory compliance, but you can go to sleep every night knowing you do everything in your power to protect your users and prevent data loss. Why? Because it’s simply the right thing to do.
Prevent Data Loss Before It Even Starts with PII Tools Data Discovery Software!




