Breach Incident Scanner
Data breach or ransomware? Our on-prem PII scanner has got you covered.
Quickly identify exposed personal data, generate detailed per-exposed-individual reports, and streamline your response process.
PII Tools gives you instant insights—eliminating delays from manual reviews.
Built for Auditing Workflows
Our Customers Say…

Shane Reid
Group Director, CEO – North America
"With PII Tools, Umlaut Solutions efficiently discovered and protected petabytes of sensitive data, revolutionizing our data governance and compliance efforts."


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”


Sean Poulter
DBA Specialist
“Your support is fantastic. I love that you fix any issue in a couple of days. It shows me that you have the drive to constantly improve the solution, unlike many other companies.”

How Does our PII Scanner Help?
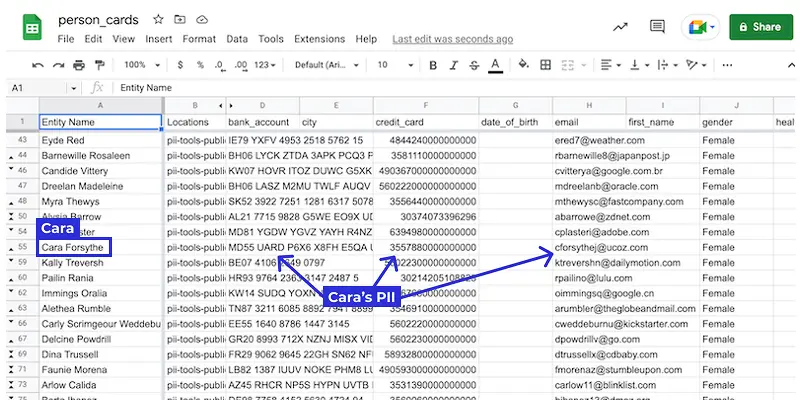
Person Cards®
Have all of the PII, PCI and PHI automatically linked up, resulting in rolled-up Person Cards that can be exported into a spreadsheet for easier import into Relativity and other eDiscovery platforms.
Lower Time to Action
Automatically find the individuals affected by a data breach or ransomware and all their PII, PCI, and PHI in seconds.
99+% Accuracy
Use proprietary AI technology to minimize false positives and take action quickly using advanced PII data discovery software.
Clear PII Data Discovery Process
Analyze and review any files, archives, emails, and images. All automatically classified according to risk.
Analytics and Reporting
Share your conclusions with colleagues or clients via interactive drill-down reports.
Check out our Unique EMAIL BREACH Feature
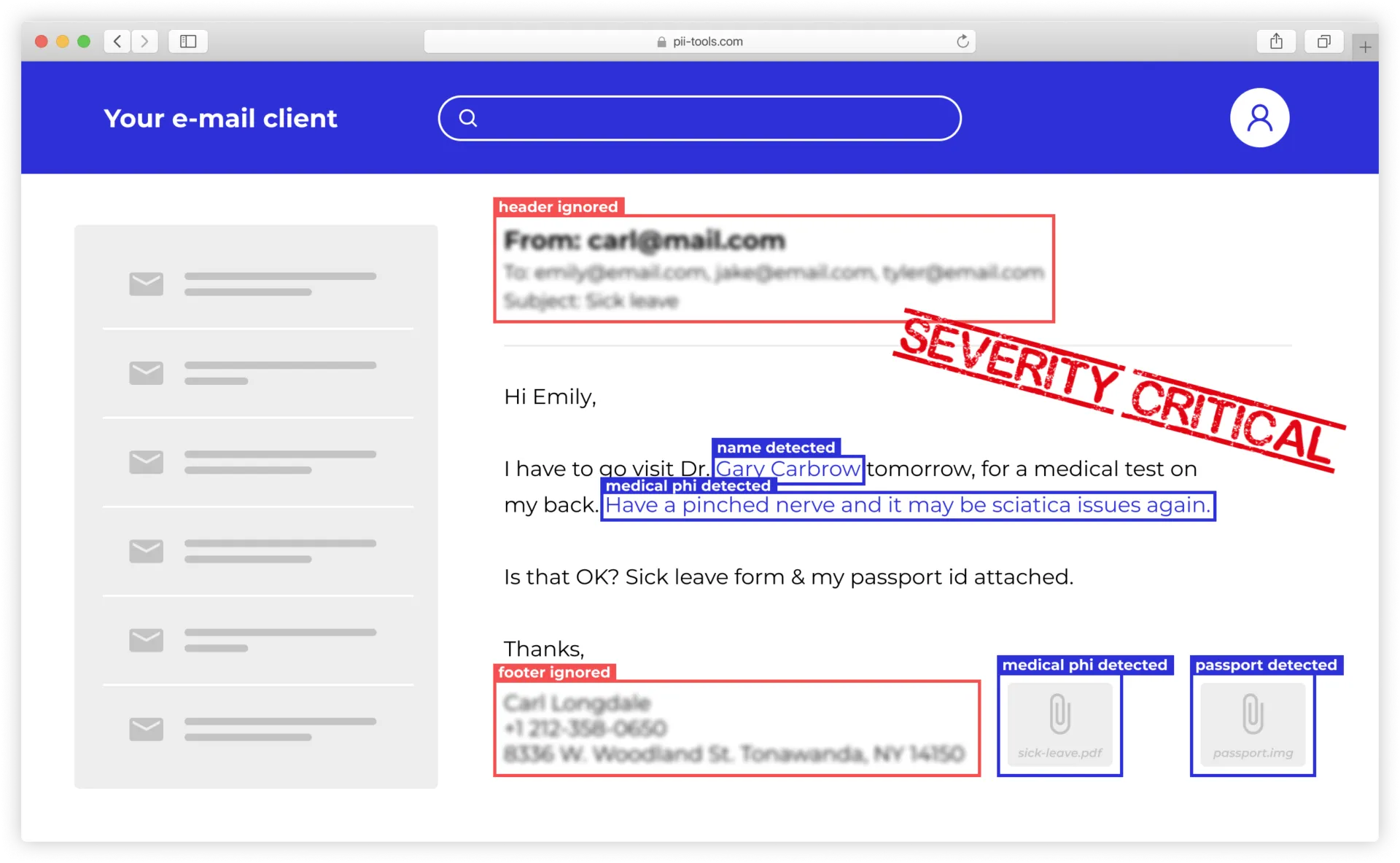
PII Data Discovery in 400+ File Formats
Take Control of Your Personal and Sensitive Data Today!
Top 3 Reasons Clients Schedule a Demo with Us:
Avoid or solve data breaches
Comply with GDPR, HIPAA, PCI DSS, and other legislation
Prepare for an audit





























