Virtual Product Tour
Get a quick look at PII Tools in action—explore the basics of data discovery and remediation.
For the full experience, turn on your sound!
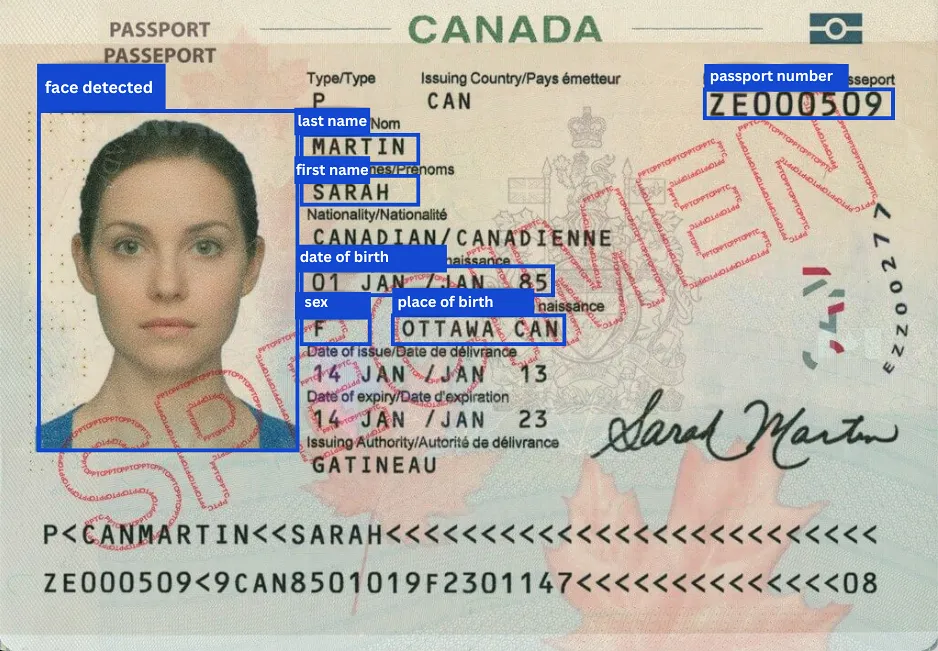
Context-Aware Detectors for GDPR, LGPD, CCPA, PCI-DSS, HIPAA, KVKK and More.
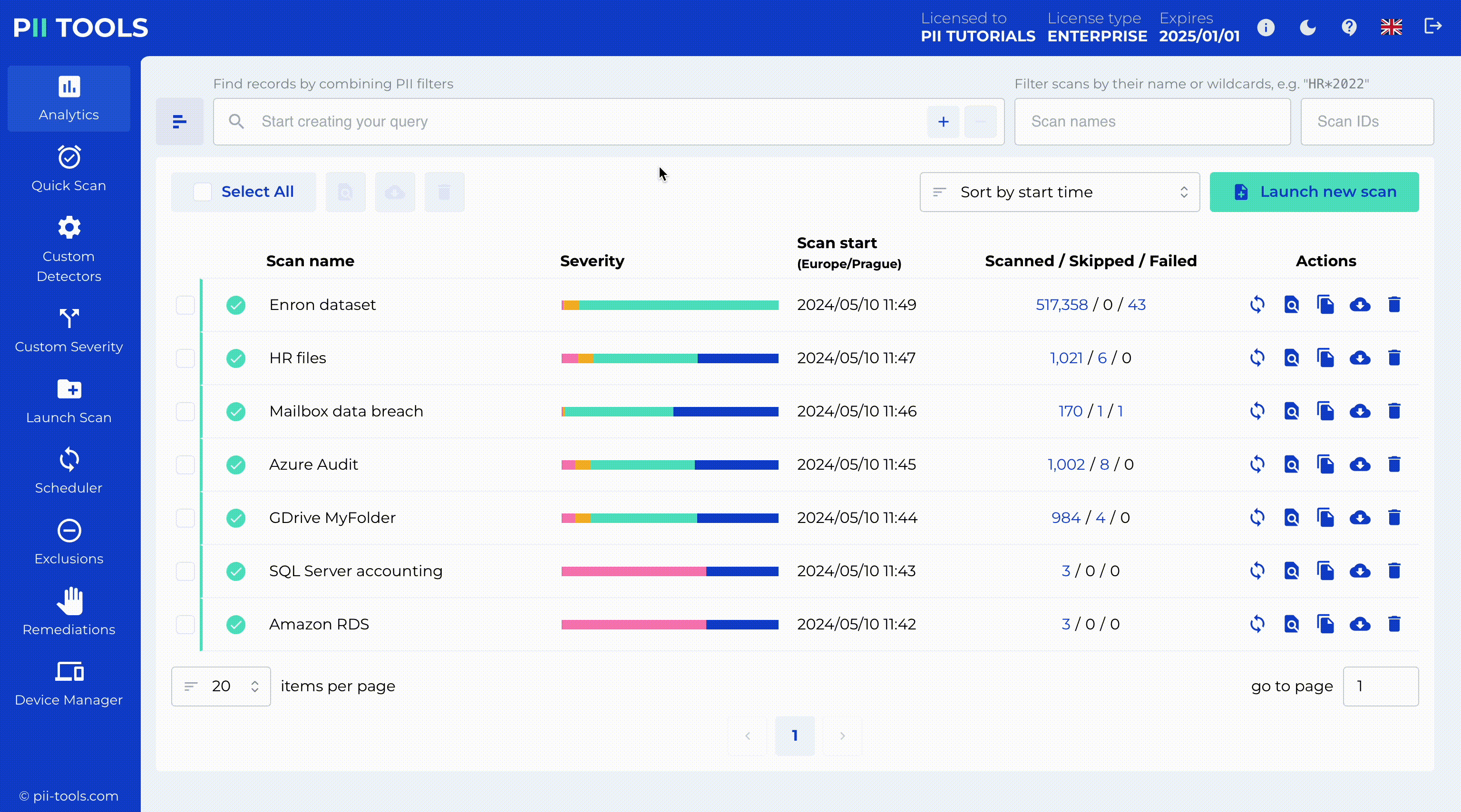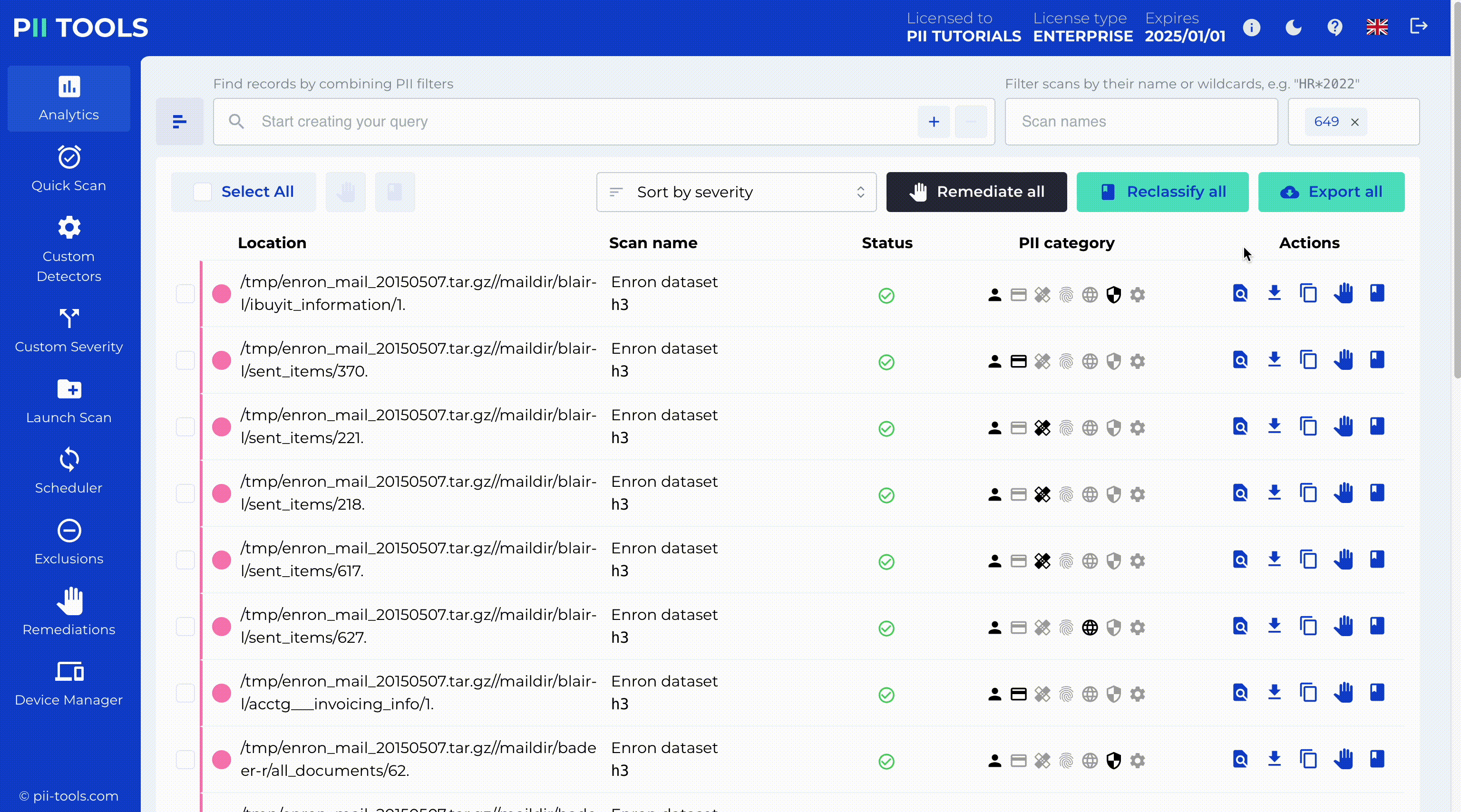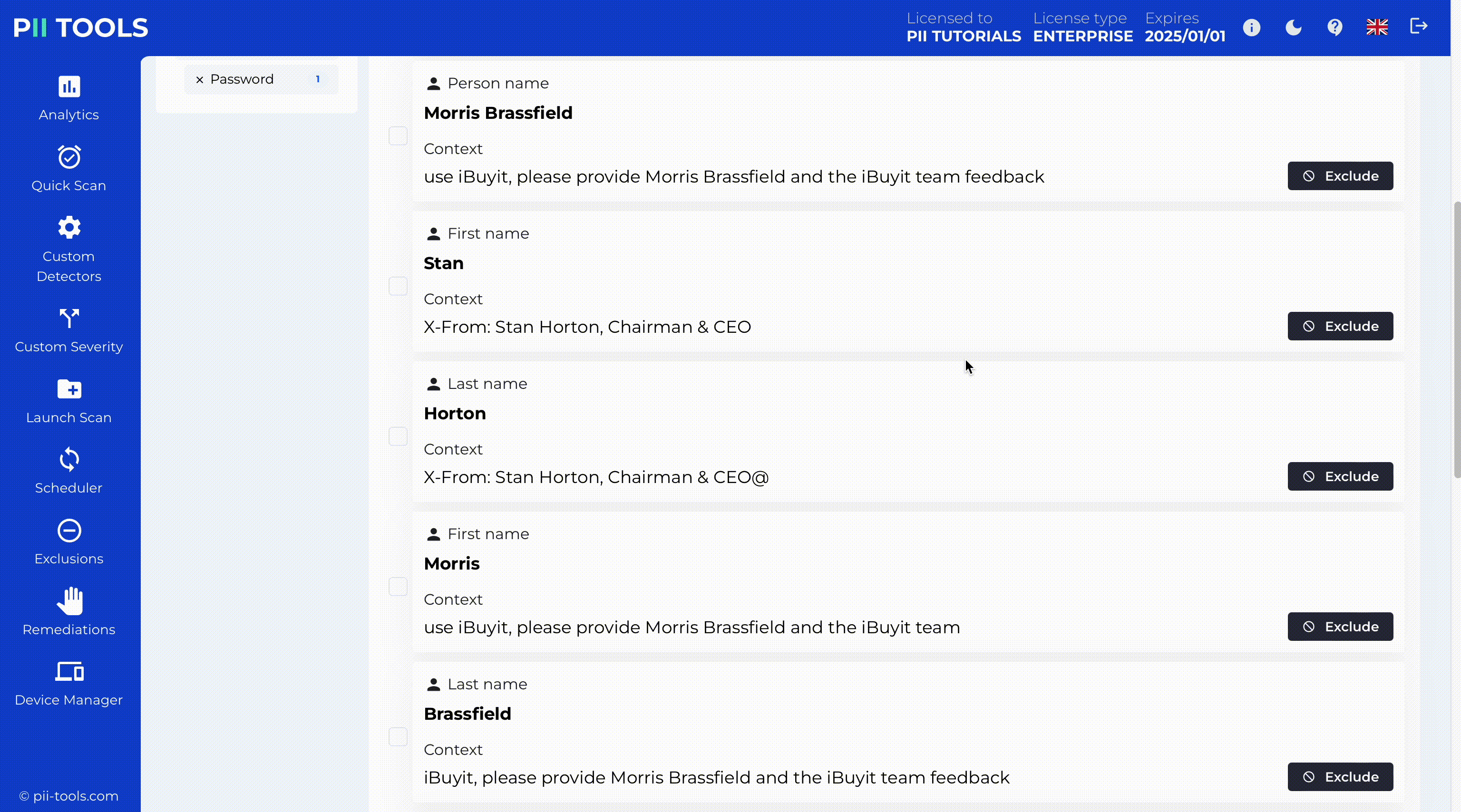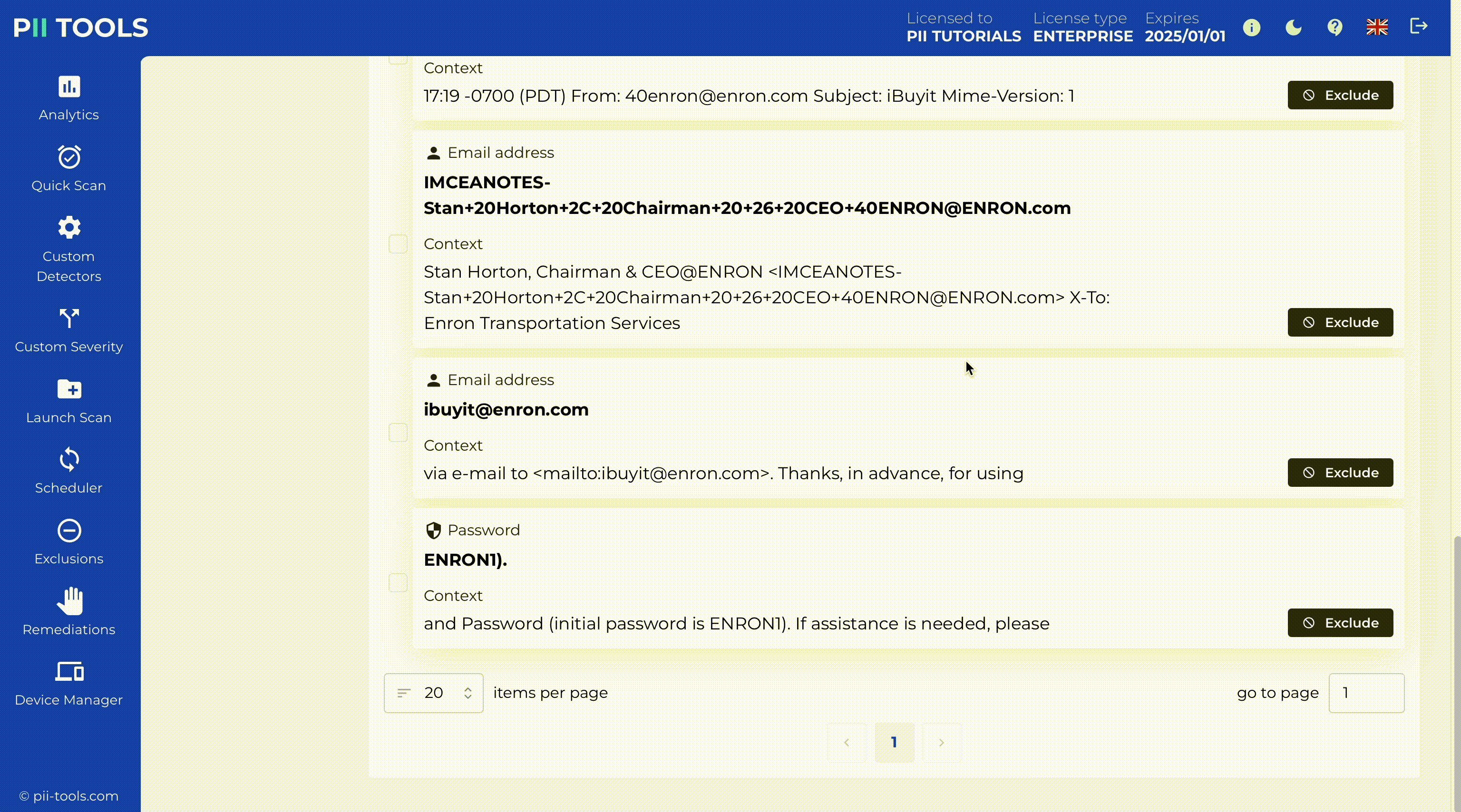
From people’s faces and passports in images, to passwords, credit cards, home addresses and names, email, telephone, health information, to sexual preferences and political views. In multiple languages.
Each instance of personal data is detected in context and with severity. You can even define your own custom detectors.
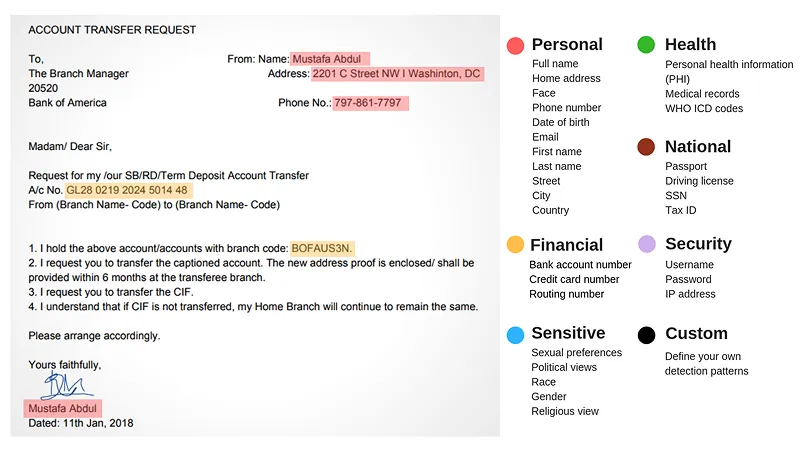
Find All Sensitive Data, Local or Remote, Structured or Unstructurd.


Scan Devices and Workstations.
Stolen laptops are a common source of security breach headaches, and employees sometimes store sensitive data in the darnedest places. Are you sure you know what your employee’s Documents or Download folder really contains?
PII Tools comes with Device Agents to scan any end devices, remote or on-site. These small Device Agents securely communicate with your PII Tools server, allowing you to scan, review and remediate files and folders on individual laptops and workstations centrally.
Supported platforms include Windows, Linux and Mac OSX.
Slice & Dice Your Inventory With a Powerful Analytics Dashboard.
Enter a person’s name, phone or home address, and get back a list of all their detected records. Relevant context is displayed right next to each hit, to speed up reviews. Use to answer a GDPR Subject Access Request (SAR).
More generally, the interactive analytics UI allows you to slice & dice all scanned data, including by PI severity, storage type, file type, date, and of course any detected PI instances.
Share Interactive Reports With Colleagues and Customers.
Start with a bird-eye-view summary of the discovered sensitive data. Then drill down by PI type and severity, all the way down to individual objects and PI instances in their context.
These interactive drill-down reports can also be downloaded in a stand-alone HTML format, for easy sharing with colleagues as email attachments for discussion and remediation.
Sensitive Data in Motion: Real-Time Streaming Environments.
Send a single document into PII Tools, get back the extracted privacy metadata formatted as JSON right away.
This stream scanning mode complements the larger storage scans, and is ideal for detections in logging, real-time environments and data-in-motion in general.
Self-Hosted Data Discovery
Deploy PII Tools on your own servers or into your own private cloud, whether on-prem or hosted. The choice is yours. Self-hosted PII Tools runs 100% air-gapped and needs no internet access.
Supported install environments include Windows 10, Linux (Ubuntu, Debian, Redhat), OSX, Microsoft Azure, Amazon EC2 and Google Compute Engine.
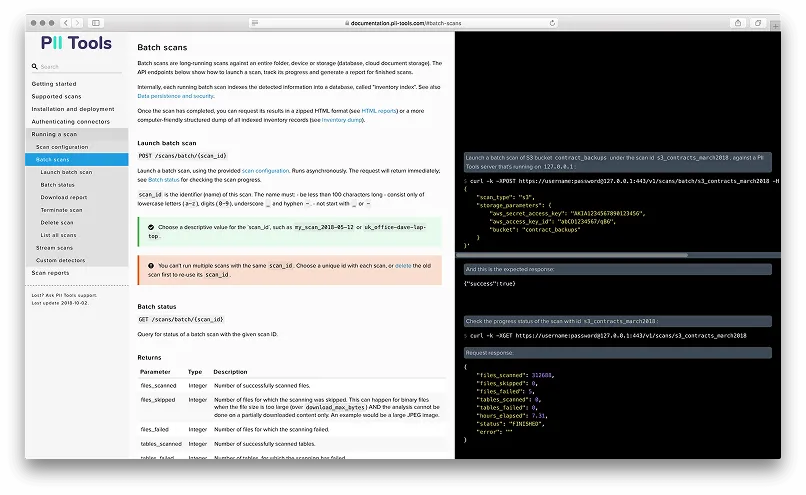
Powerful Developer API for Scanning Automation.
This PII detector is built with automation in mind. All functionality is exposed through REST APIs.
This means seamless integration: machines talking to machines. Your IT can use the API of PII Tools to launch scans, run analytics, generate reports and remediate programmatically, without any human input or clicking on web pages.
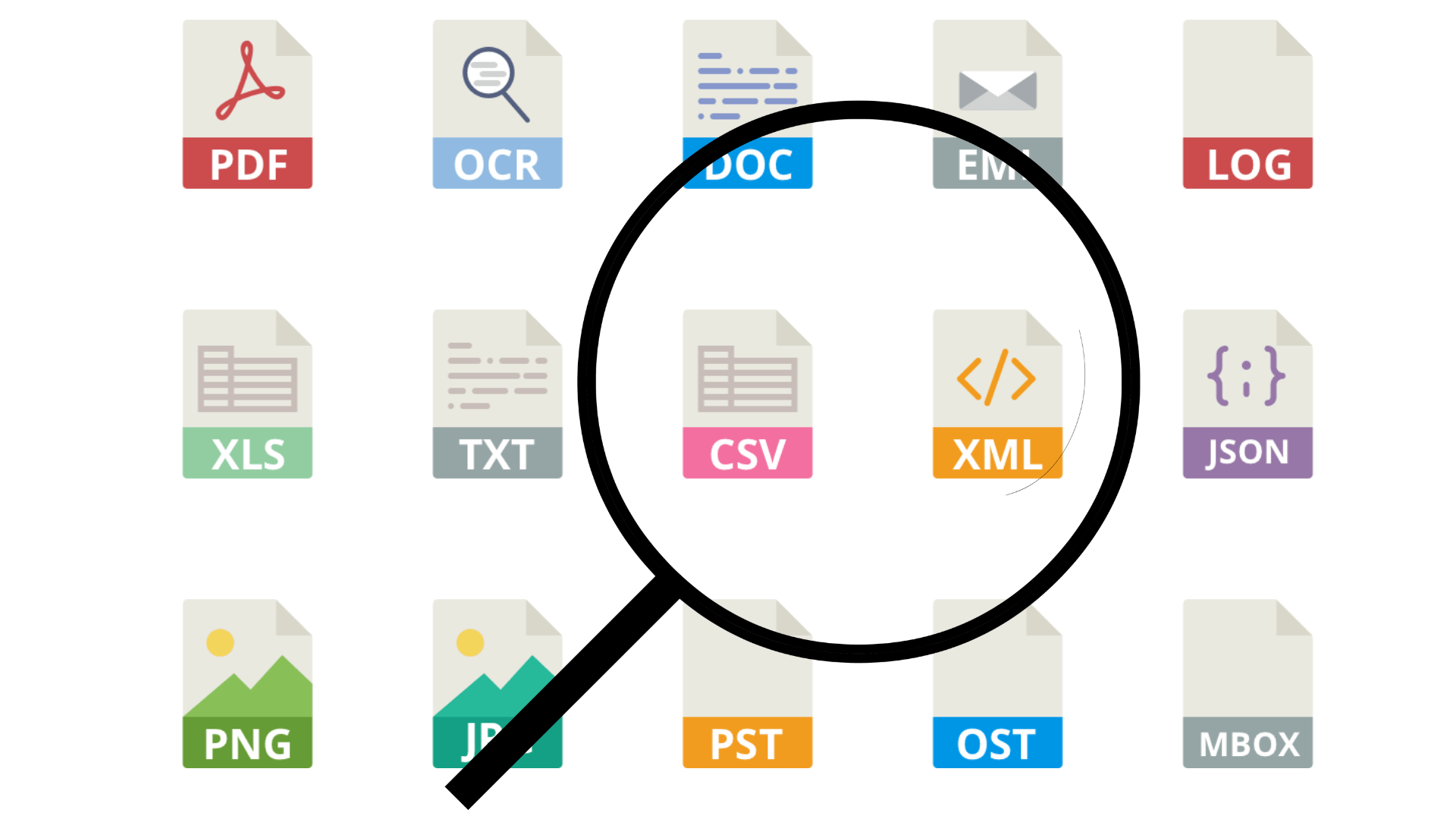
Will PII Tools Analyze OCR on a Rotated PDF Scan? You Bet.
PII Tools looks inside email attachments, embedded images inside Word documents, archives like ZIP or RAR and PST. Built-in OCR for PDFs and image scans goes without saying.
In total, this PII scanner covers over 400 file formats, including most structured (CSV, Excel) and unstructured (PDF, Word, JPEG, PNG, email, log…) files.
Save on Network Cost With Large Files.
PII Tools will only download and analyze parts of data as needed, efficiently streaming contents of large files.
This allows efficient on-the-fly handling of extremely large file archives. Such archives often represent long-forgotten backups, hiding explosive sensitive information risk.
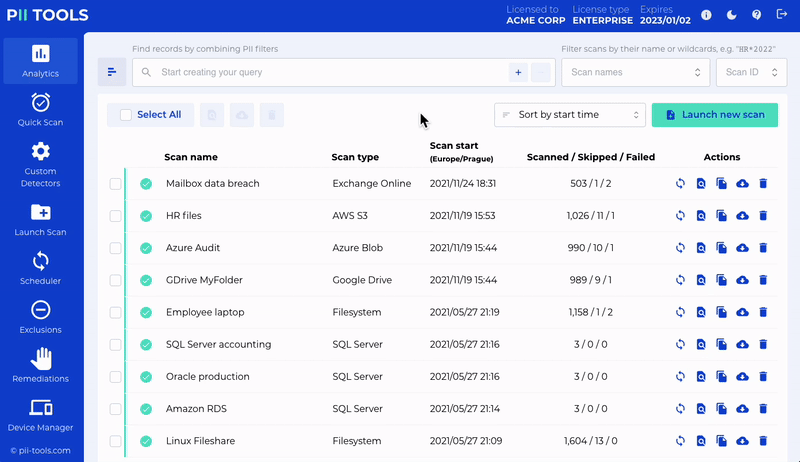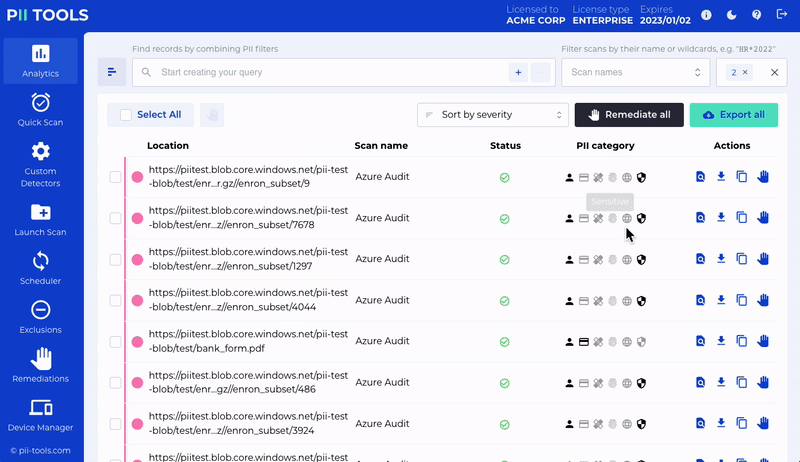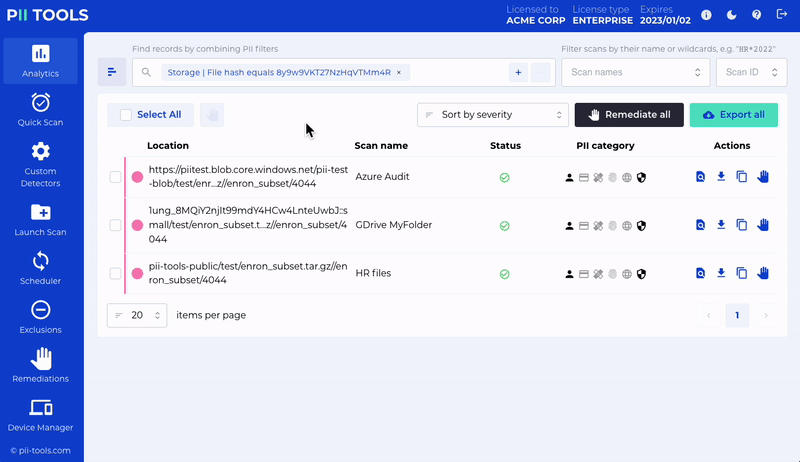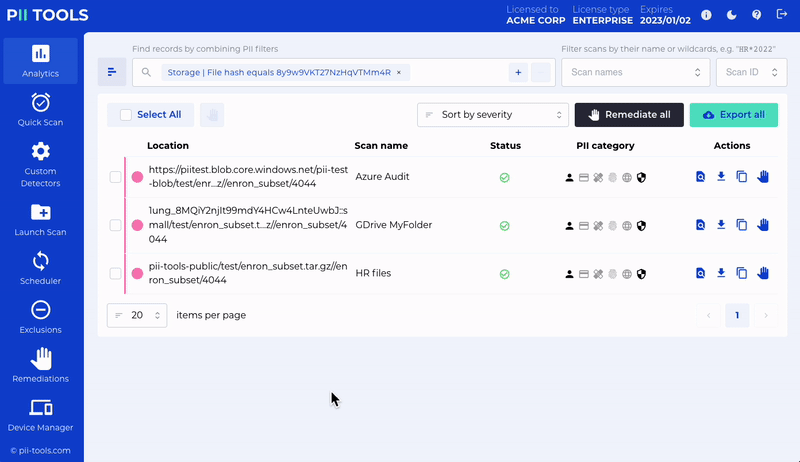
Take Action: Delete and Quarantine Unwanted Files.
While PII Tools never deletes or modifies any data on its own, it can export and remediate data on request.
After filtering scanned files by severity, location or any PII detections, you can delete or (optionally) quarantine the result directly from the PII Tools dashboard.
You can also export information from PII Tools into a CSV or JSON file, for later import into a BI tool for additional graphing and integration.
Find Duplicate Files
PII Tools automatically identifies file duplicates (device, email, attachment…) based on the actual file content.
Erase all copies of potentially harmful files with a single click, no matter their filename or location: endpoints, emails, cloud. Decluttering your inventory means less files and less space, which translates to less risk and reduced storage costs.
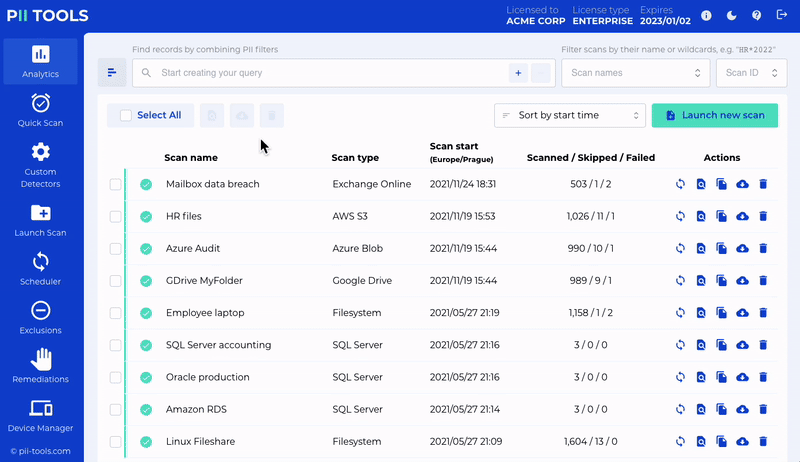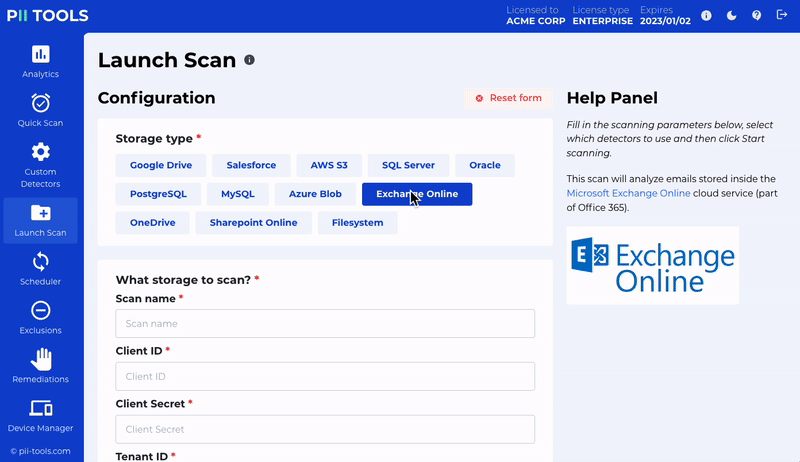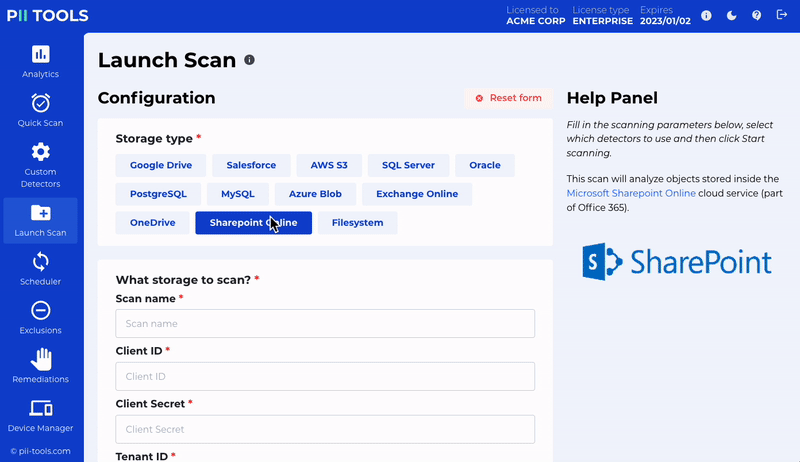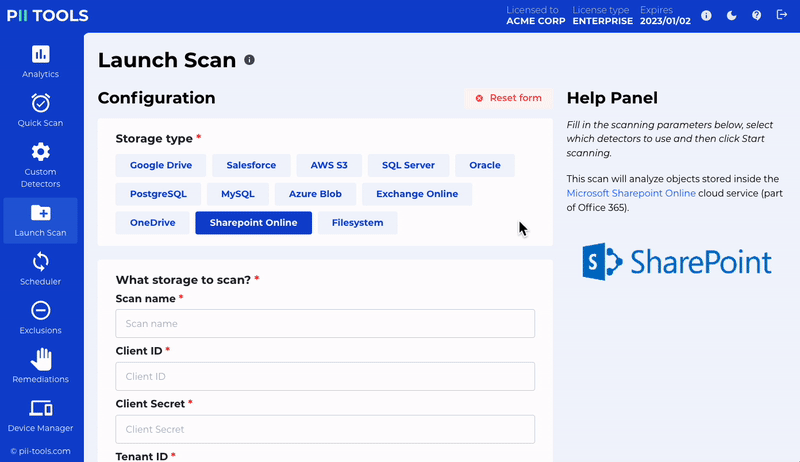
Office 365 Remediation
Quarantine and erase files within Office 365 – including Exchange Online, Sharepoint Online and OneDrive.
The quarantine process retains all metadata from any erased original – meaning you see the original permissions, owners, email headers, etc. It is also possible to delete individual email attachments independently while keeping the rest of the email.
Pre-Configured and Ready to Run. From Purchase to First Scan in 30 Minutes.
PII Tools comes packaged as a turn-key virtual appliance. Same everywhere. Less time wasted on installation issues means more time invested into understanding your data and its implications.
Technically, PII Tools is distributed as a fully configured Docker image. Once the Docker image is deployed on your machine, you’re ready to access your private PII Tools web interface and start scanning.

Person Cards®
The holy grail of data discovery. PII Tools automatically links up all PII, PCI, and PHI on each individual.
This creates a rolled-up Person Card spreadsheet to import into Relativity and other eDiscovery platforms for convenient review and quality control.
Document Redaction
Surgical discovery and in-place redaction of sensitive data from documents, including PDFs, images across all common data storages.
- Windows, Linux and MacOS servers and endpoints
- Office 365 OneDrive
- Office 365 Sharepoint Online
- Azure Blob
- AWS S3
The Data Redaction feature also offers a REST API for an even easier integration into your workflows.