Person Cards®
The holy grail of data discovery you’ve
been waiting for. A true game changer for
breach & ransomware investigations, DSAR requests, and privacy practice in general.

Our Customers Say…

Mark Cassetta
SVP Strategy
“Our survey found that 22% of the time, humans failed to identify personal data in documents, while PII Tools succeeded in all scenarios. By integrating with PII Tools, Titus was able to significantly reduce the compliance risk for our customers.”


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”


Shane Reid
Group Director, CEO – North America
“Integrating PII Tools has allowed Umlaut Solutions to handle petabytes of client data seamlessly, enhancing accuracy and reducing the risk of data breaches.”

What Are Person Cards®?
PII Tools automatically links up all of the PII, PCI and PHI that its AI detectors found on each individual, such as their name, email, DoB or credit card, from both structured and unstructured data, files, emails and databases.
The resulting rolled-up Person Cards can be exported into a spreadsheet for easier import into Relativity and other eDiscovery platforms. Unassigned PII is included as well of course, for manual review and quality control.
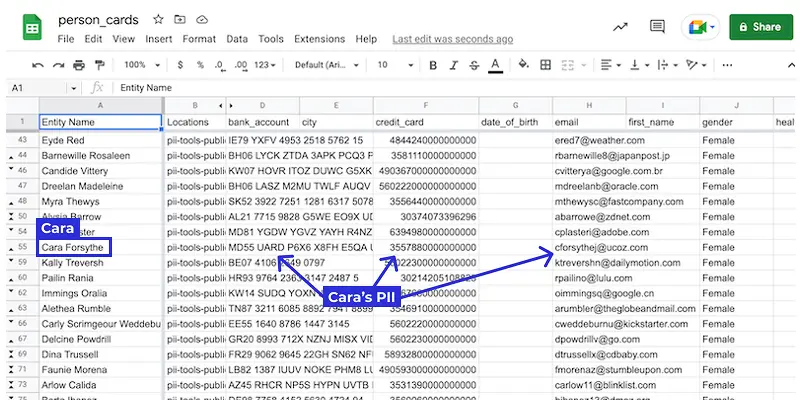
The PII detection and linking is completely automatic and aggregates PII across the whole inventory, not just within one document.
For example, a Person Card may list that person's SSN as discovered in a PDF form, plus their DoB and address found in a SQL table, and credit card and passport as OCRed from an email attachment.
All rolled up neatly into one row – for easy export and review.
"Who was in the data and what information do we keep on them?"
First, automatically discover all of the people who appear in a dataset, along with all PII & PCI & PHI instances in the dataset.
Then let PII Tools link up PII instances to individuals. Export the created Person Cards to guide incident response teams and answer subject access requests quickly and with confidence.
Check out Our Unique Features
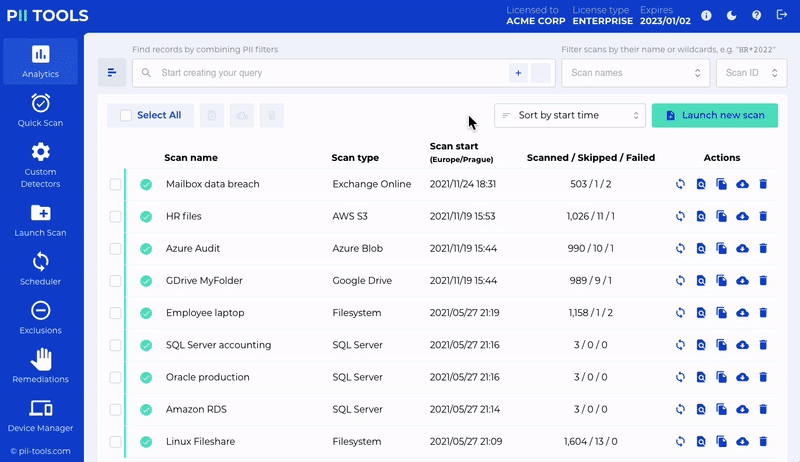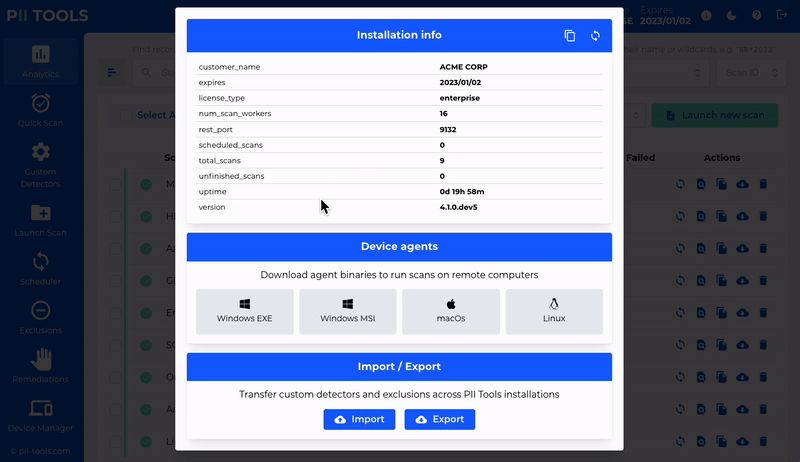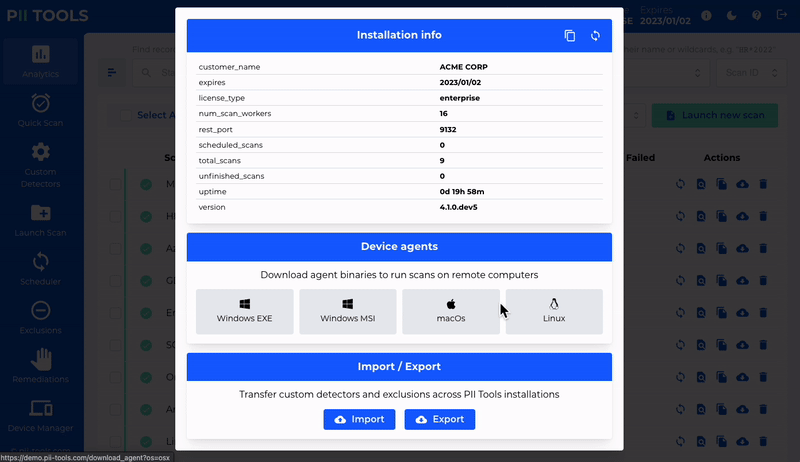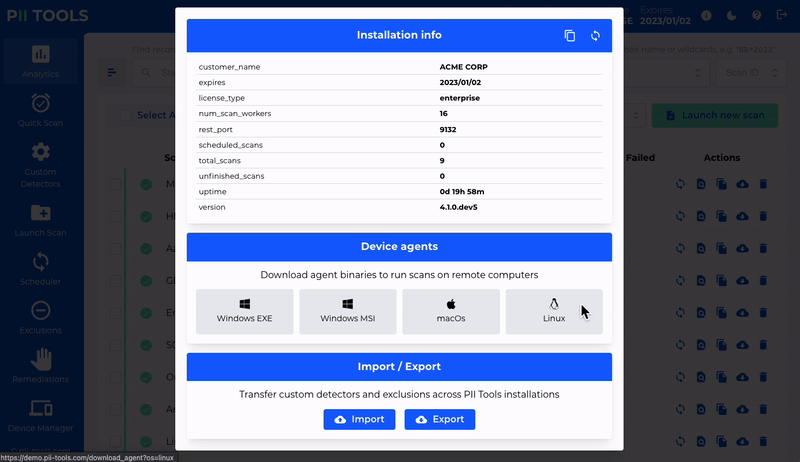
Detect PII Data in 400+ File Formats