GLBA – Gramm-Leach-Bliley Act
Make your mandatory data protection and compliance as easy as it gets.
Our Customers Say…

Mark Cassetta
SVP Strategy
“Our survey found that 22% of the time, humans failed to identify personal data in documents, while PII Tools succeeded in all scenarios. By integrating with PII Tools, Titus was able to significantly reduce the compliance risk for our customers.”


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”


Shane Reid
Group Director, CEO – North America
“Integrating PII Tools has allowed Umlaut Solutions to handle petabytes of client data seamlessly, enhancing accuracy and reducing the risk of data breaches.”

How PII Tools Helps with GLBA
360° Data Discovery
Find all the sensitive data in your environment. Scan local and cloud storages, emails, databases, archived and password-protected files, images, signatures, and more (see the complete list). Rely on built-in OCR to analyze scanned or rotated documents.
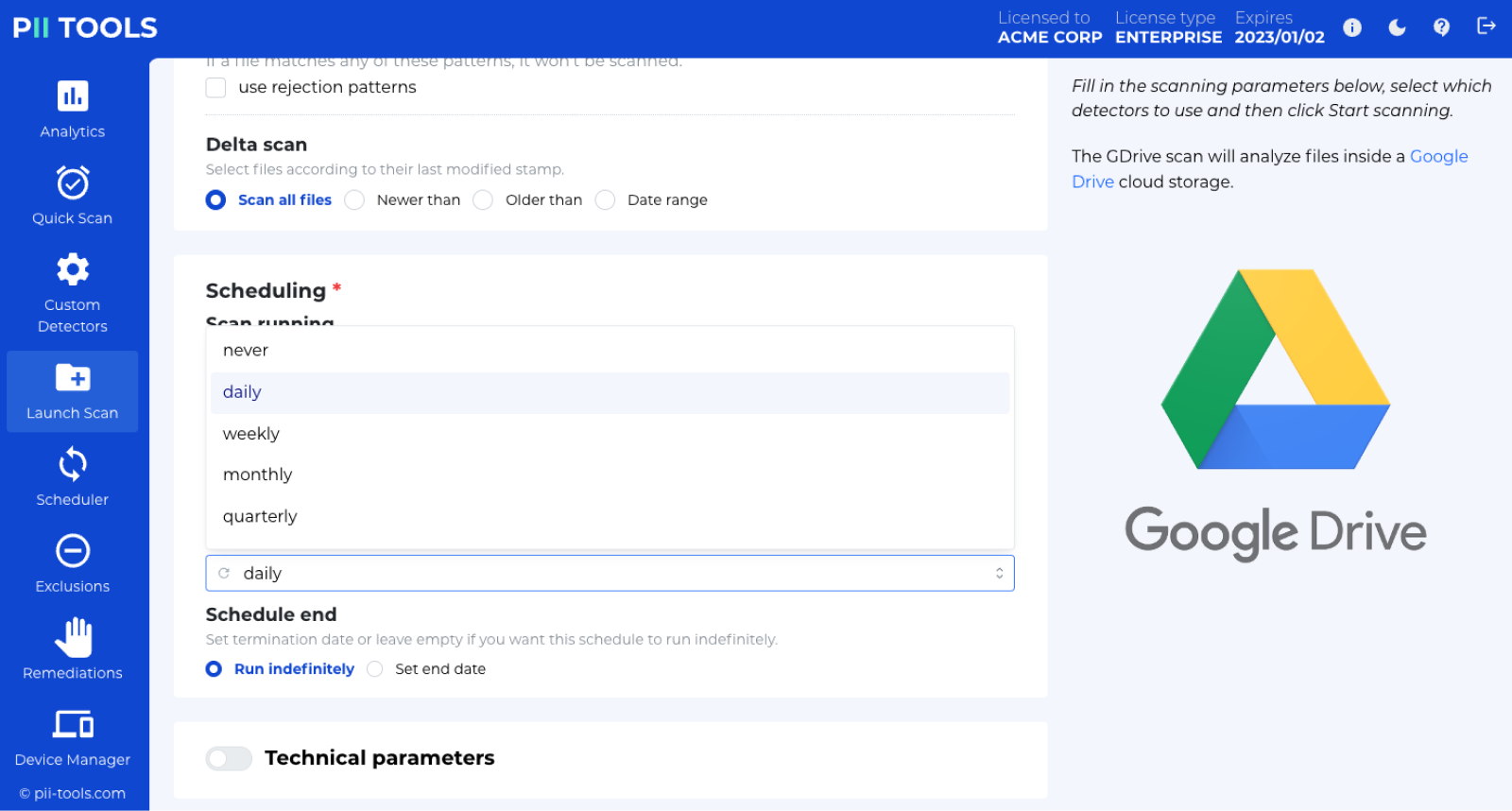
Continuous Compliance
Set up scheduled scans of your environment to confirm no sensitive data lives outside the designated locations. Plan automatic daily, weekly, or monthly recurring scans, or run an on-demand scan to monitor the PII data in your systems.
Risk Classification
Analyze and sort PII data based on its severity, content, or context. PII Tools performs an automatic risk classification for each scanned file. This helps you to evaluate PII data in context and improves your review experience, as not all personal information is created equal.
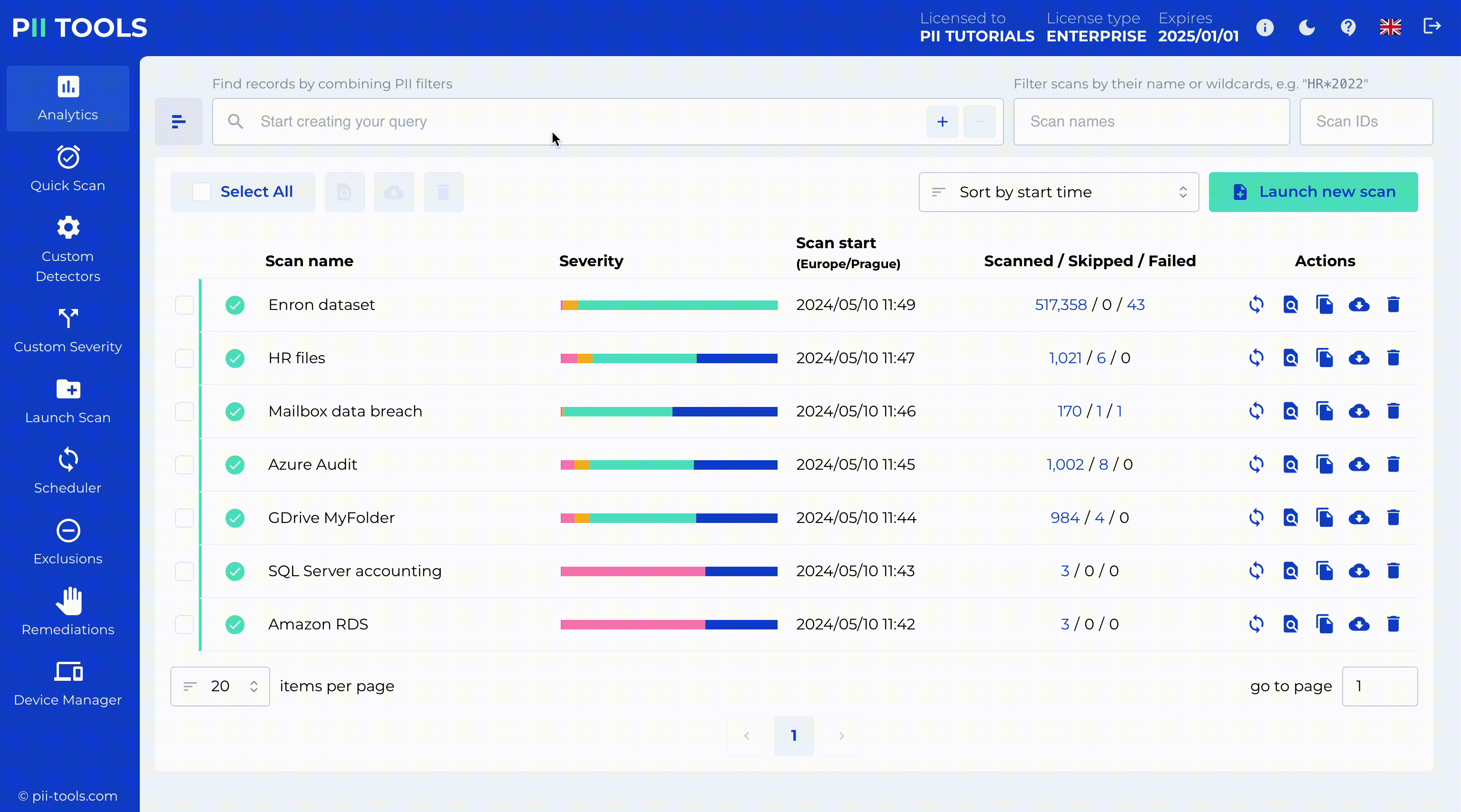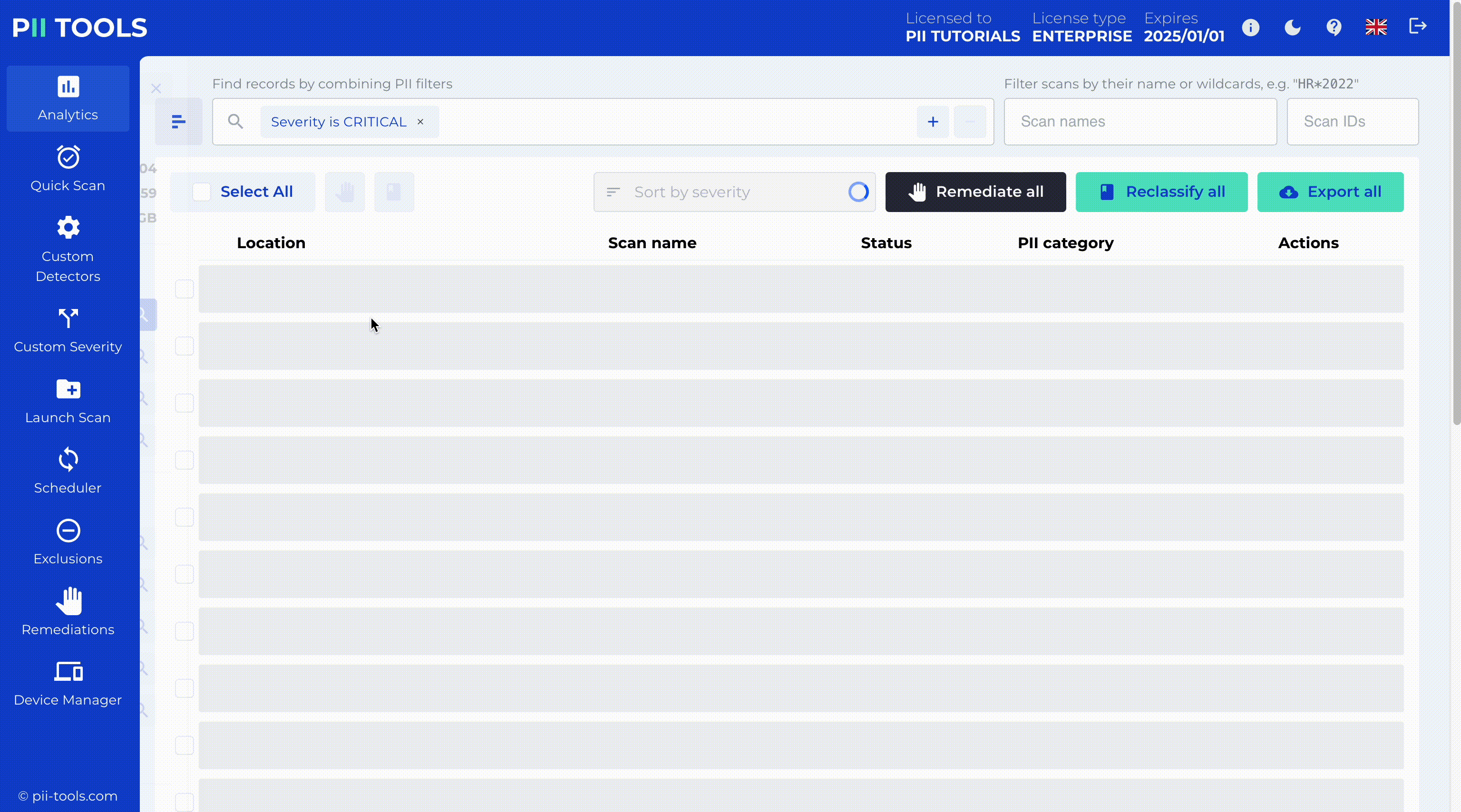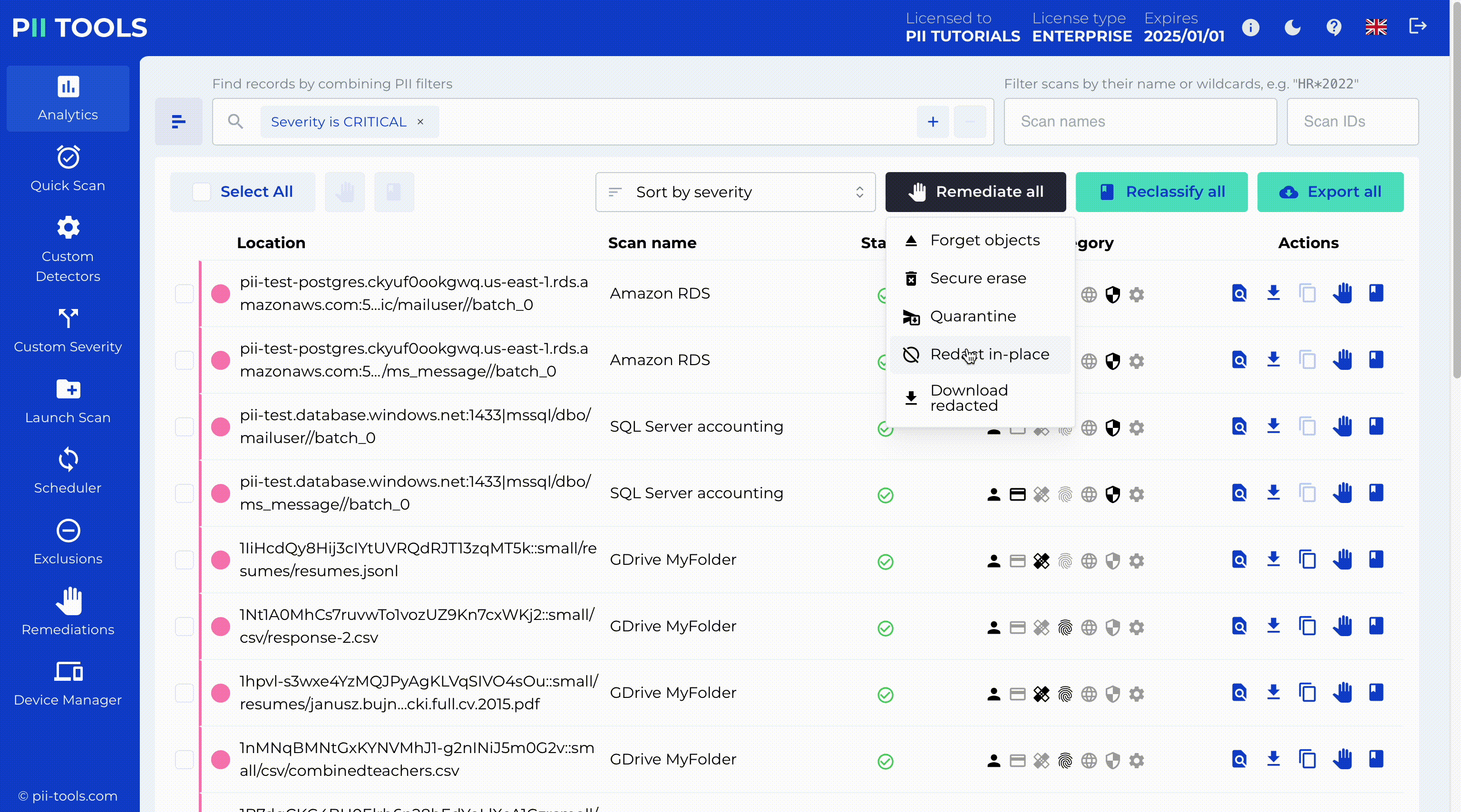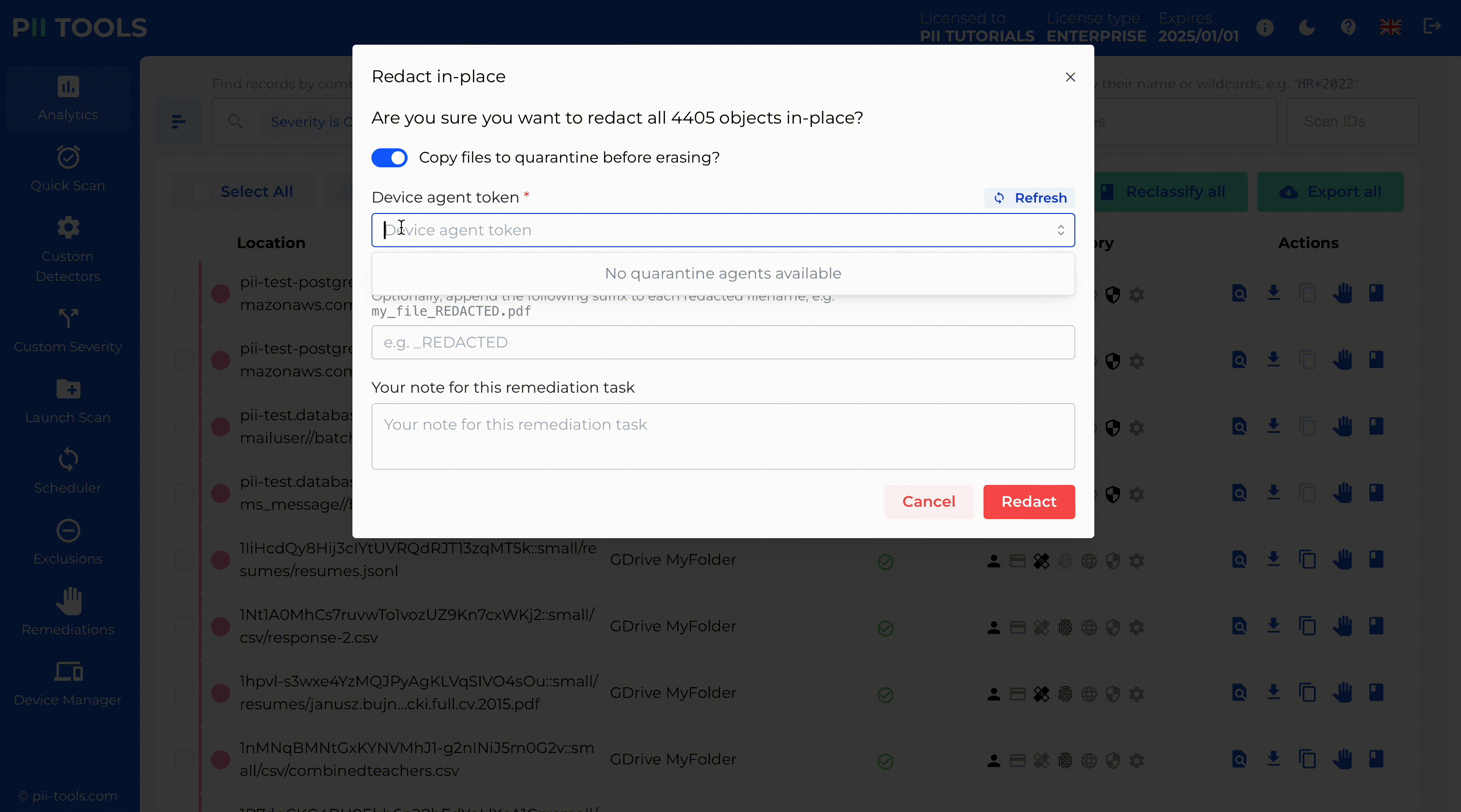
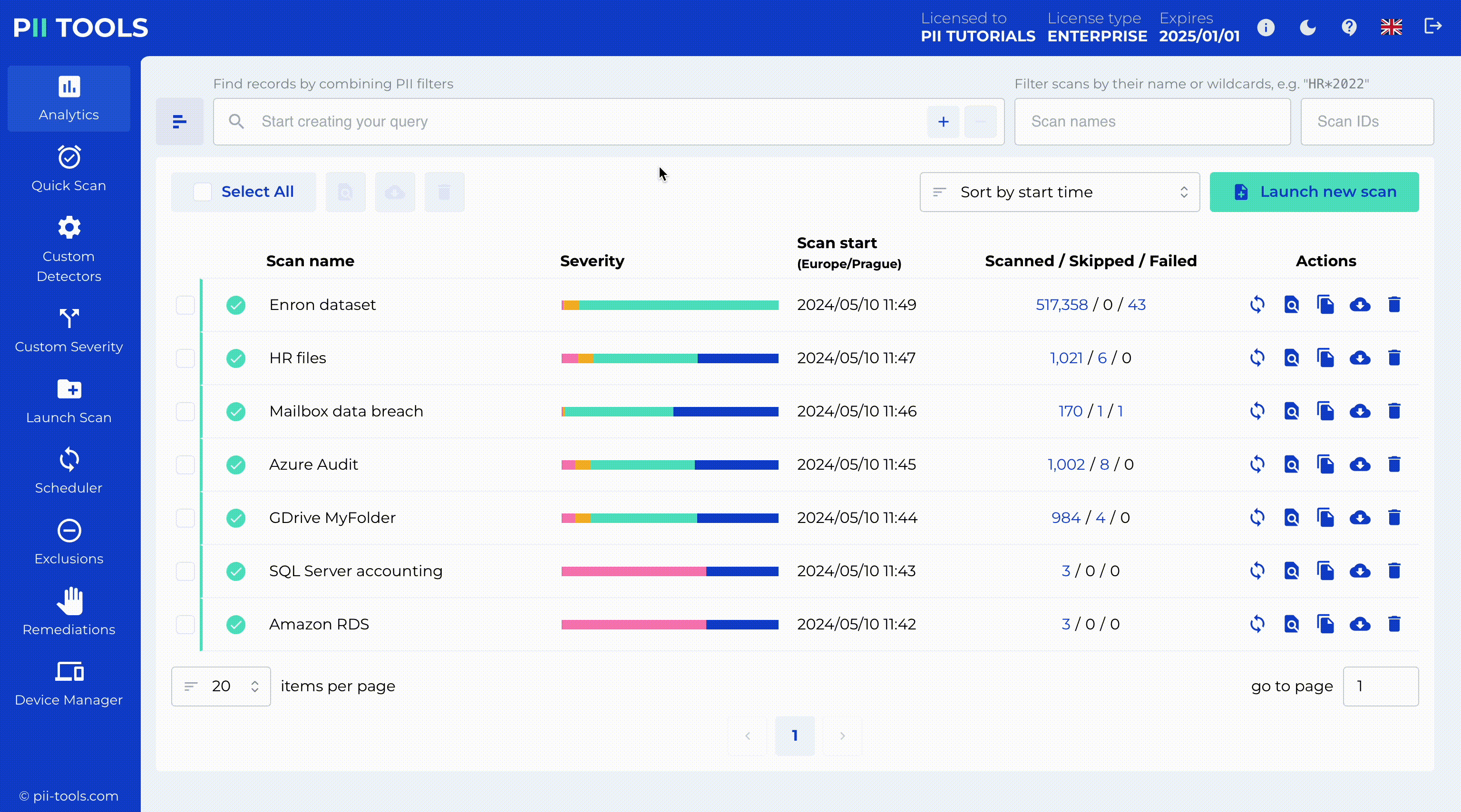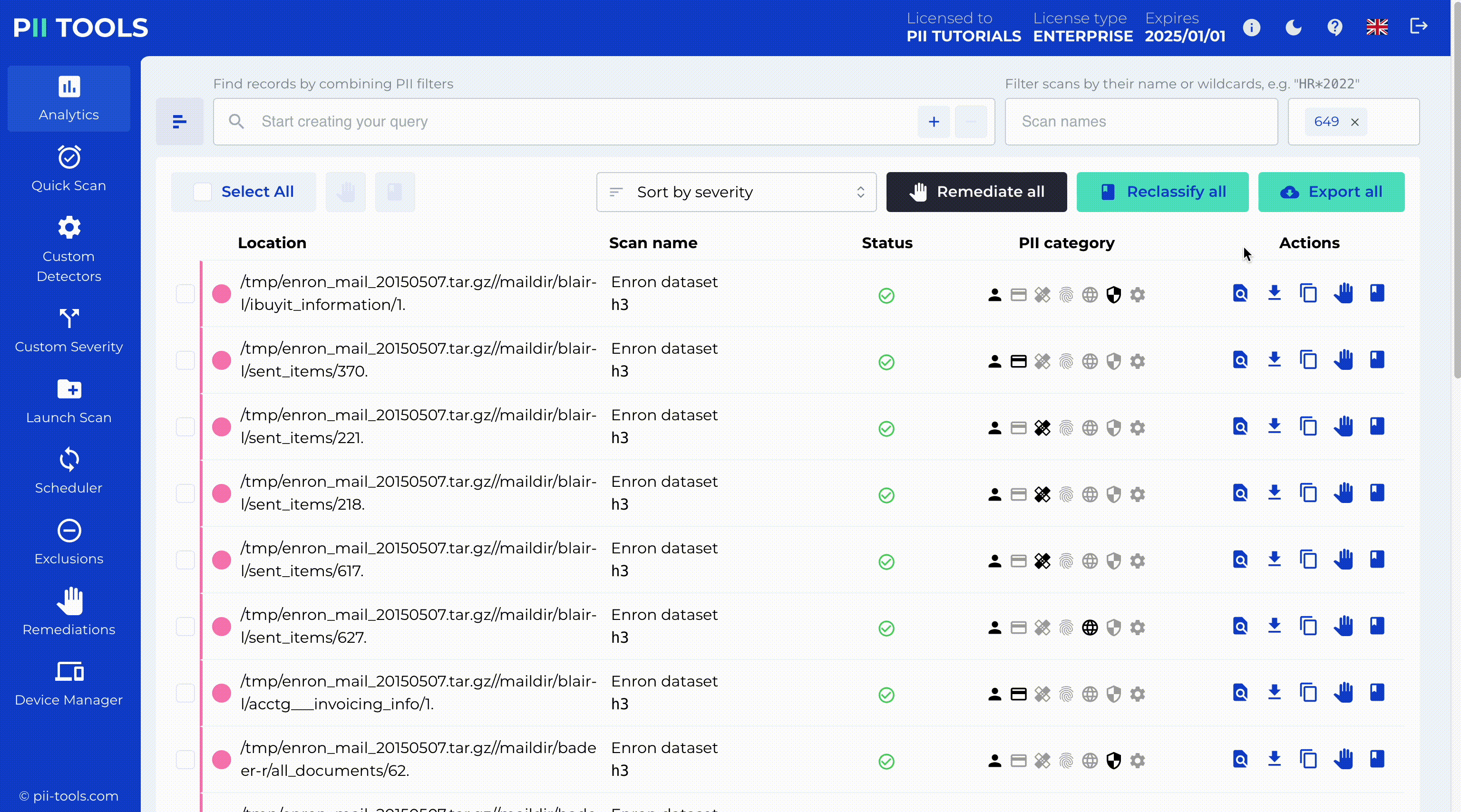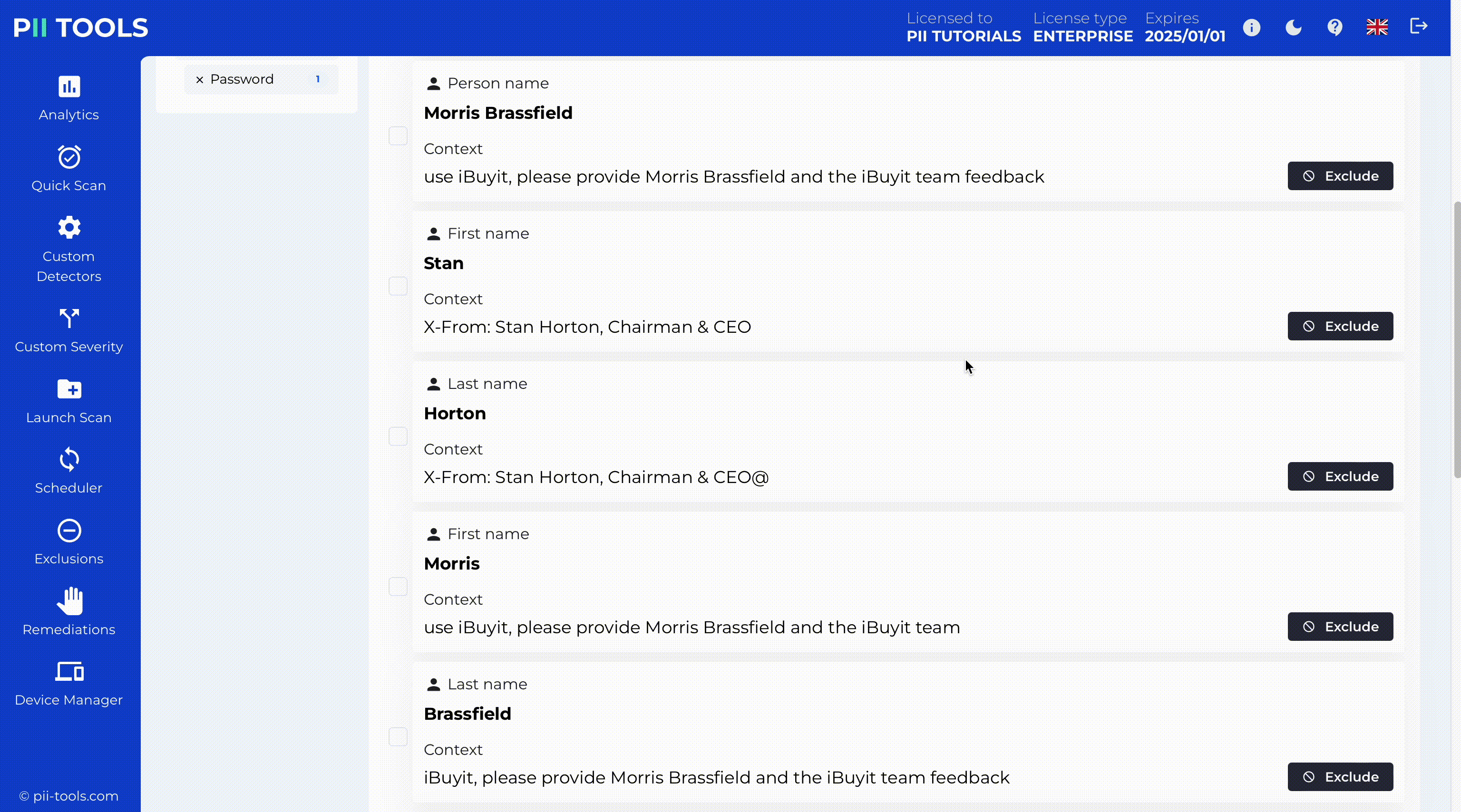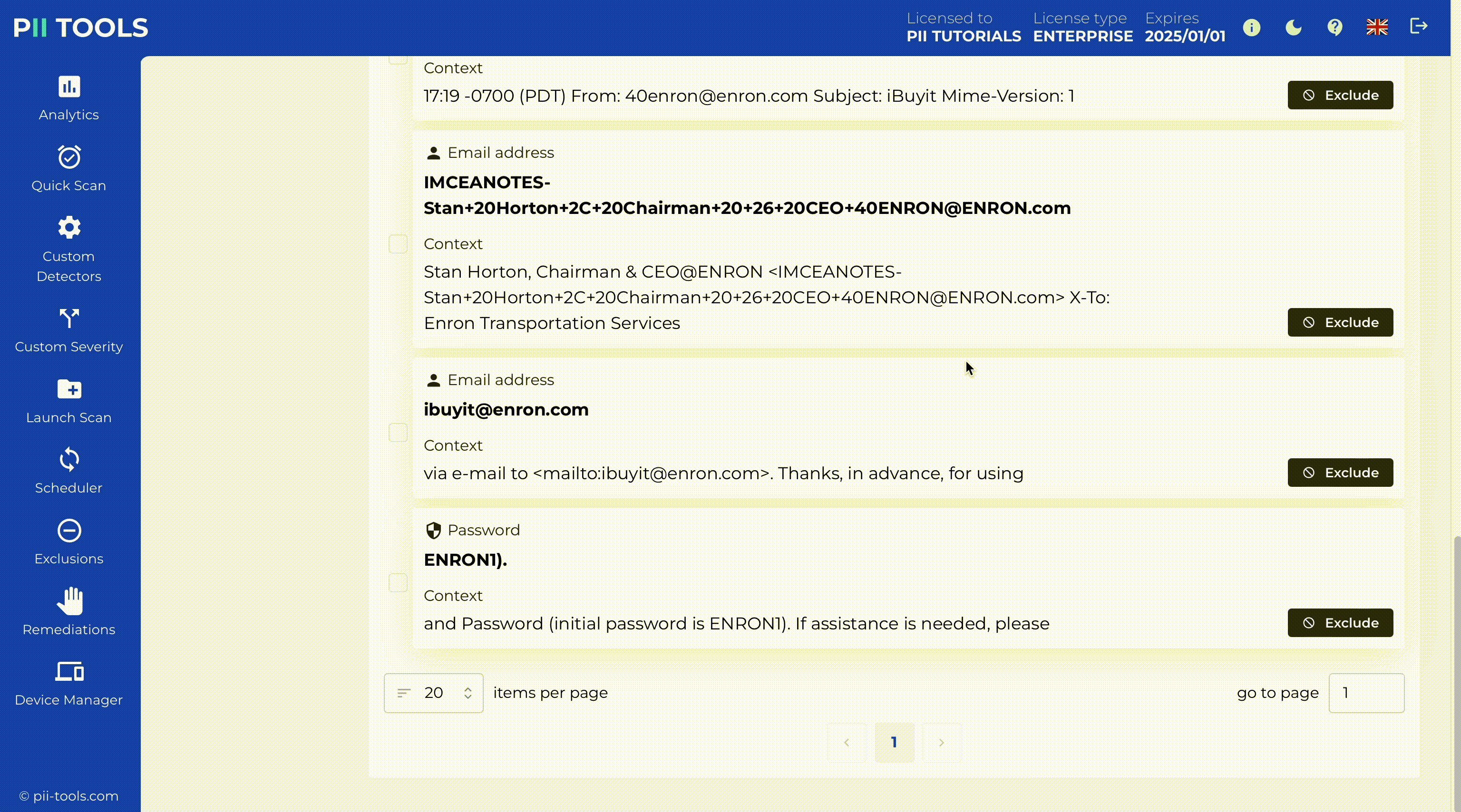
Data Breach Management
The first step to mitigate the damage is to identify what was breached: all affected persons and their breached PII, PCI, and PHI. PII Tools helps incident response teams find leaked personal data in seconds and at a minimal cost.
Audits and Compliance Reports
Thanks to the state-of-the-art technology backing PII Tools, you know the precise position of each personal identifier (names, credit card numbers, etc.). Create clear and interactive reports showing which files or databases contain PII data to share with your colleagues, clients, or auditors.
Need Help with GLBA compliance?
Take control of your personal and sensitive data today!
Top 3 Reasons Clients Schedule a Demo with Us:
Avoid or solve data breaches
Comply with GLBA, GDPR, PCI DSS, and other legislation
Prepare for an audit














