Automate Data Protection, Ensure Compliance
Stop wasting hours manually searching for sensitive data.
PII Tools automates the discovery and protection of PII in all your files—whether PDFs, spreadsheets, or scanned contracts—at lightning speed.
Our Customers Say…

Mark Cassetta
SVP Strategy
“Our survey found that 22% of the time, humans failed to identify personal data in documents, while PII Tools succeeded in all scenarios. By integrating with PII Tools, Titus was able to significantly reduce the compliance risk for our customers.”


Shane Reid
Group Director, CEO – North America
“Partnering with PII Tools has revolutionized how Umlaut Solutions manages extensive data repositories, providing our clients with unmatched data discovery accuracy and robust protection. Our collaborative efforts help protect the sensitive data of millions of citizens.”


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”

One Unique Solution for
Your Data Discovery Needs
How Does PII Tools Help?
Optimized For Semi-Structured Files
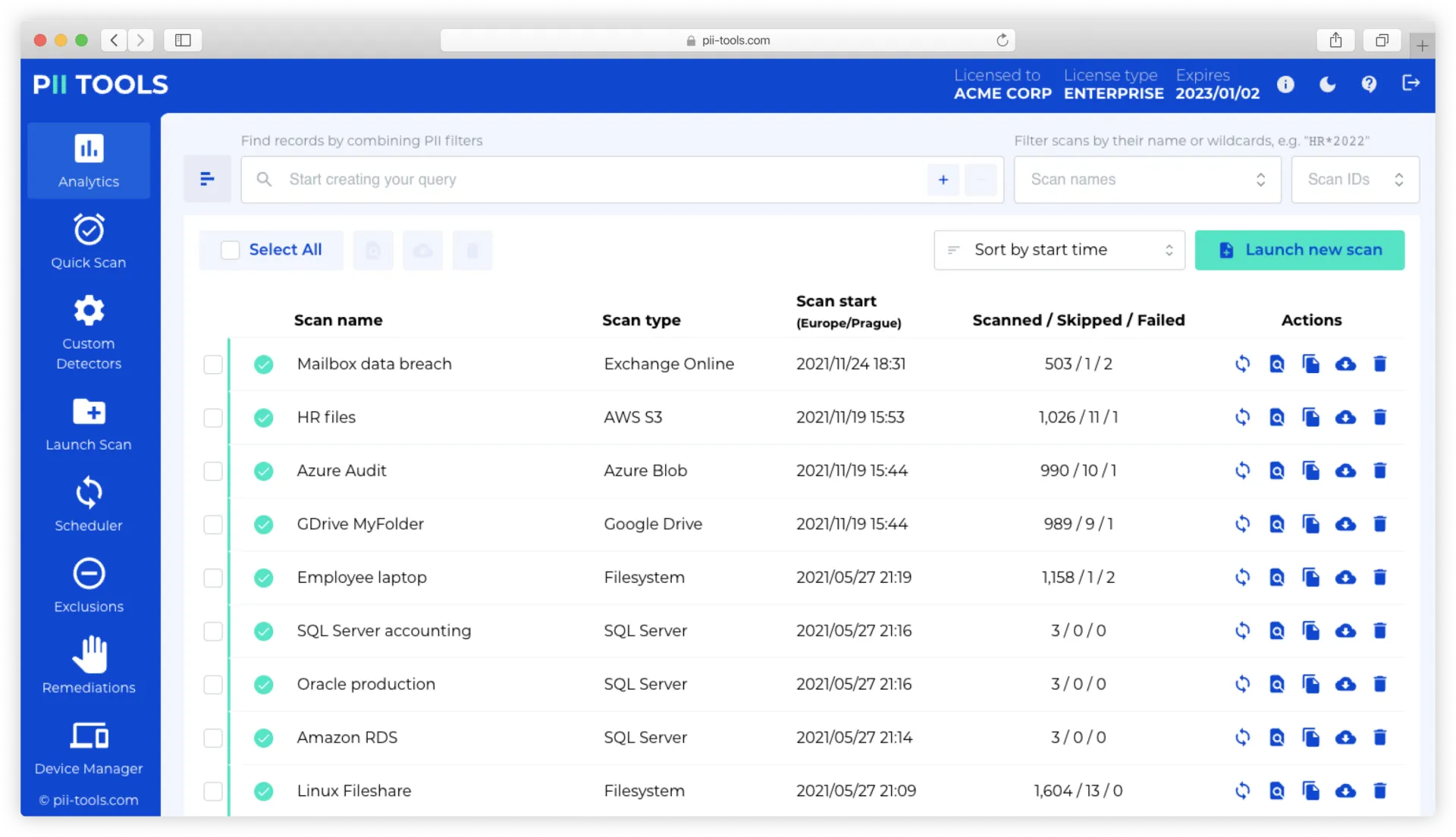
Detect PII in semi-structured documents, such as PDF forms, embedded tables, or complex spreadsheets. Use PII Tools for scanning files, emails and their attachments, and databases. Or simply find every piece of PII across all of the cloud and on-prem endpoints you use – the choice is yours, so stop digging through your data manually.
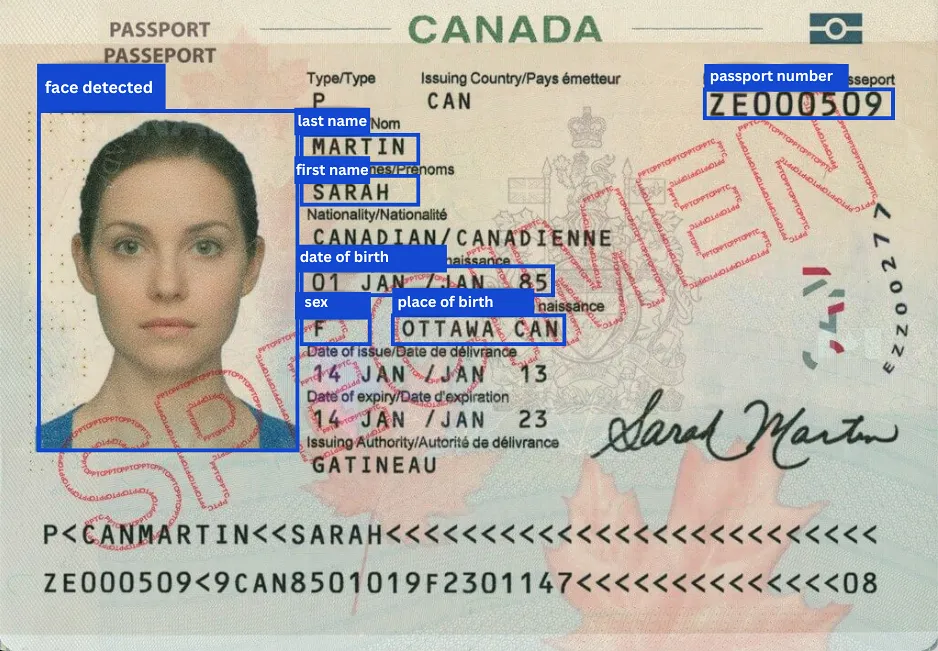
Built-in OCR
Rely on our proprietary technology to recover sensitive data from photos, images, and scanned files. The state-of-the-art AI analyzes every piece of data, structured or unstructured, to make sure you know about every possible data risk.
Lightning Speed
Run PII Tools as self-hosted software, the scanning speed is as fast as your infrastructure allows. Our clients average 2 documents per CPU core per second for file scans (~100,000 documents per hour on a 16-core machine), or 5 MiB per second for database scans.
Data Breach Management
The first step to mitigate the damage is to identify what was breached: all affected persons and their breached PII, PCI, and PHI. PII Tools helps incident response teams find the leaked personal data in seconds and at minimal cost.













