Document Redaction
Surgical AI discovery and redaction of sensitive data for files and documents.

Our Customers Say…

Mark Cassetta
SVP Strategy
“Our survey found that 22% of the time, humans failed to identify personal data in documents, while PII Tools succeeded in all scenarios. By integrating with PII Tools, Titus was able to significantly reduce the compliance risk for our customers.”


Raul Diaz
Senior Director, IT
“A manual data review would take us years and years, which was not an option. PII Tools provides us with a full report wherever there is any PII on our Sharepoint, GSuite, Microsoft Exchange, Salesforce, and physical devices.”


Shane Reid
Group Director, CEO – North America
“Integrating PII Tools has allowed Umlaut Solutions to handle petabytes of client data seamlessly, enhancing accuracy and reducing the risk of data breaches.”

How Does PII Tools Help With Document Redaction?
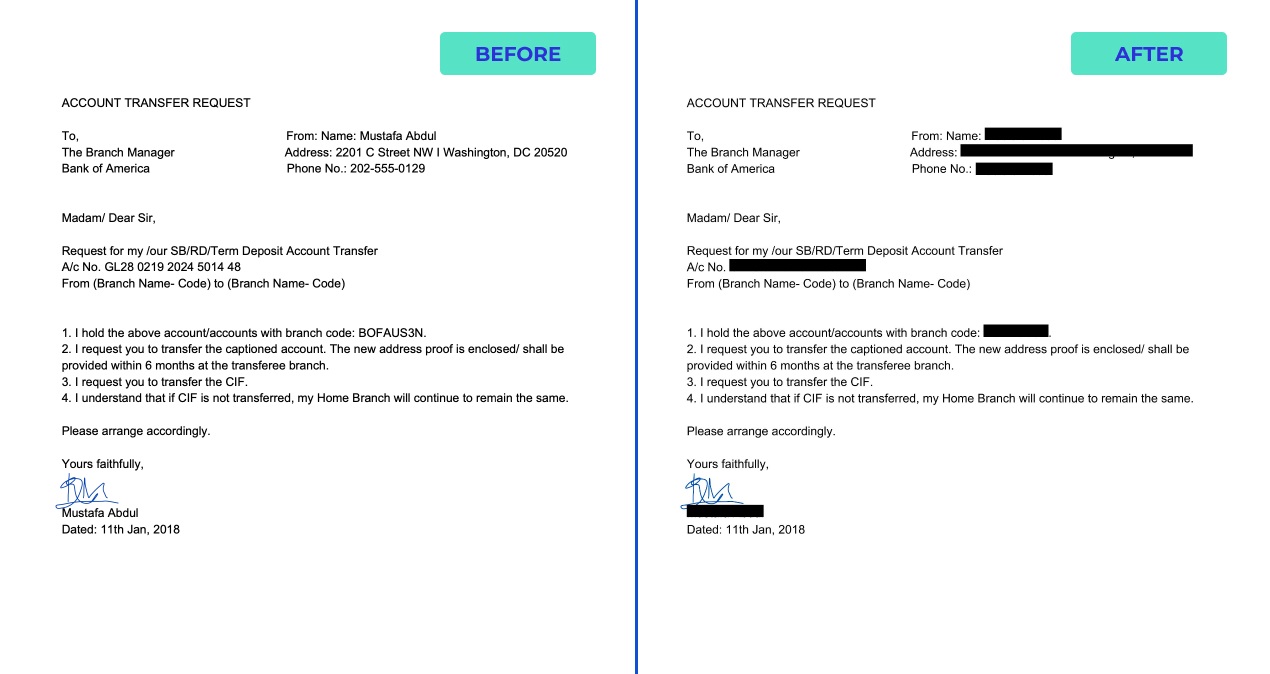
Surgical Data Redaction
PII Tools’ powerful AI identifies and redacts personal and sensitive data in documents across your inventory. Then, with a click of a button the redacted files replace the original documents in their exact locations, where your users know to find them.
You can also save the redacted copy into a new location. Or even have the unredacted original files copied to a safe quarantine location prior to redaction, for example for backup or for legal hold.
Swift Action Times
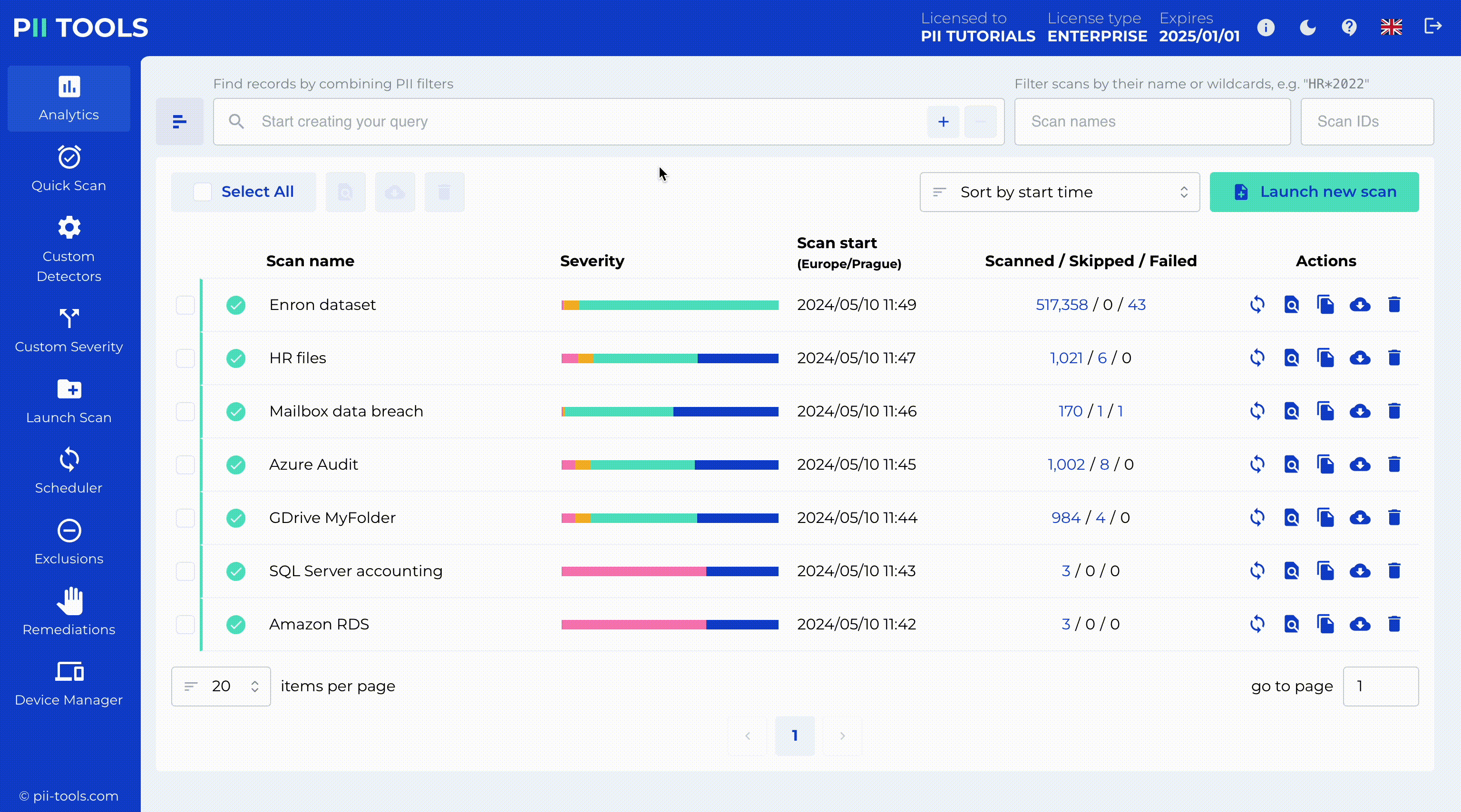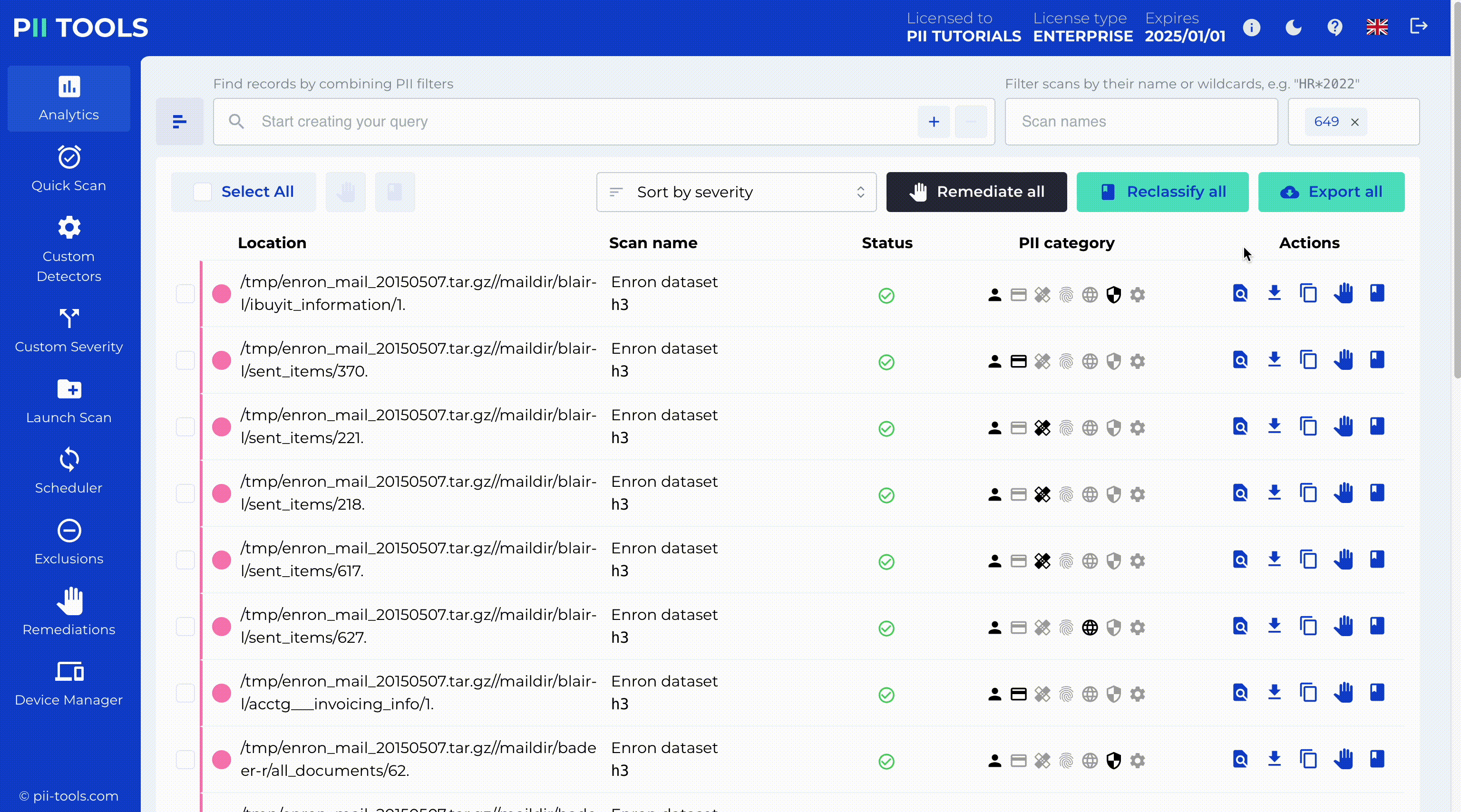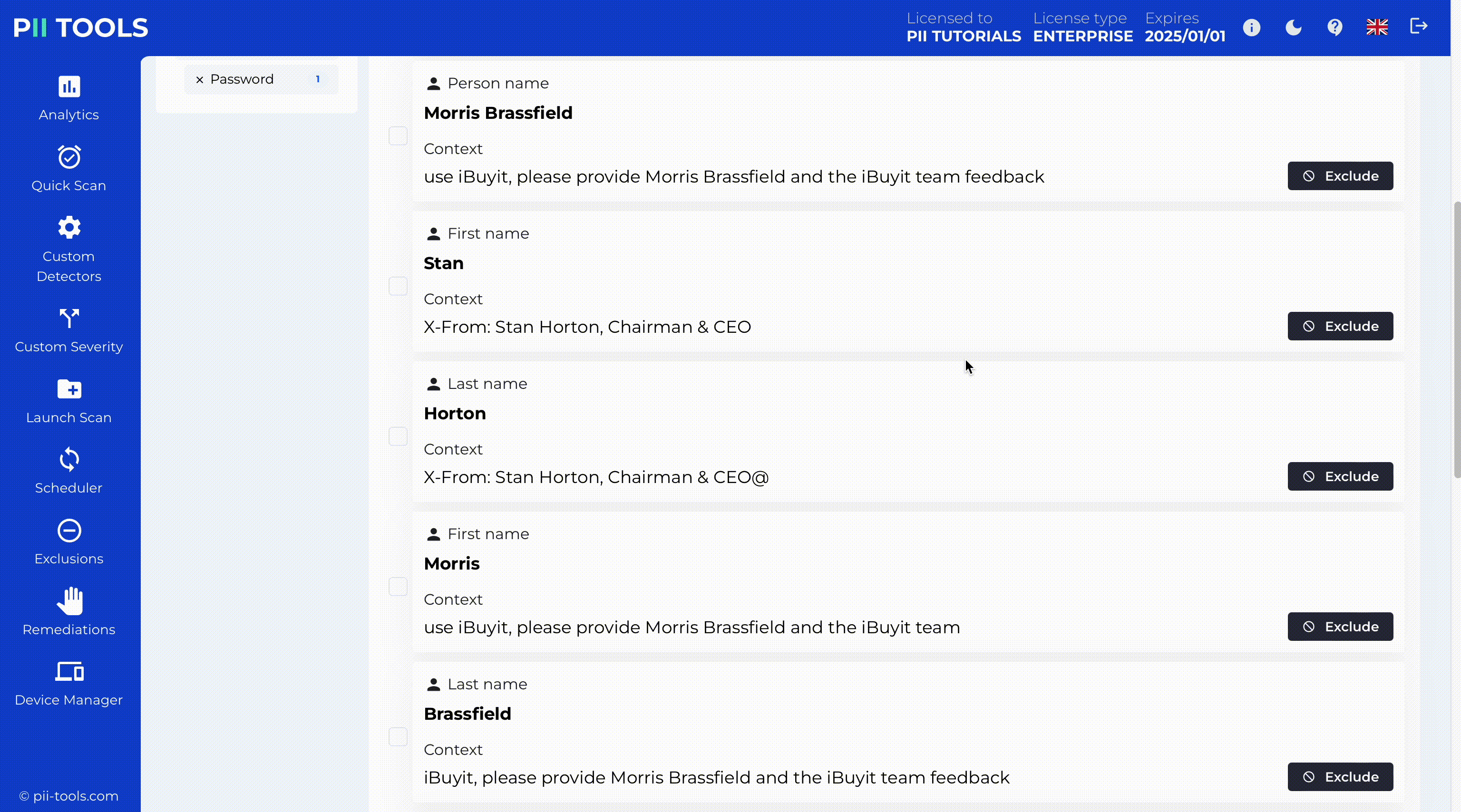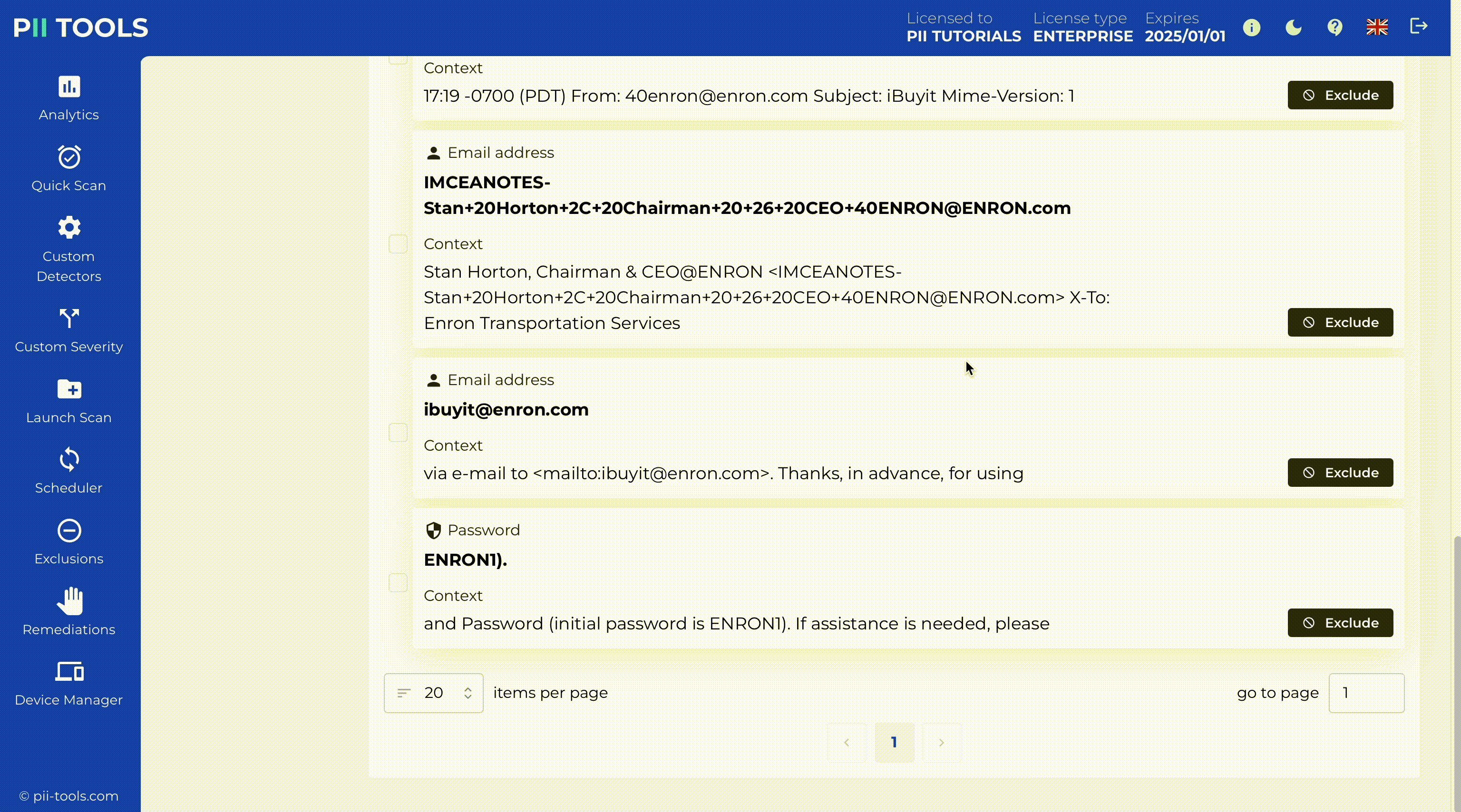
Discovery and redaction of sensitive data in your files are fast and automatic processes done by our AI.
This leaves you free to focus on the strategic management of the situation, be it a regular data audit or a breach investigation.
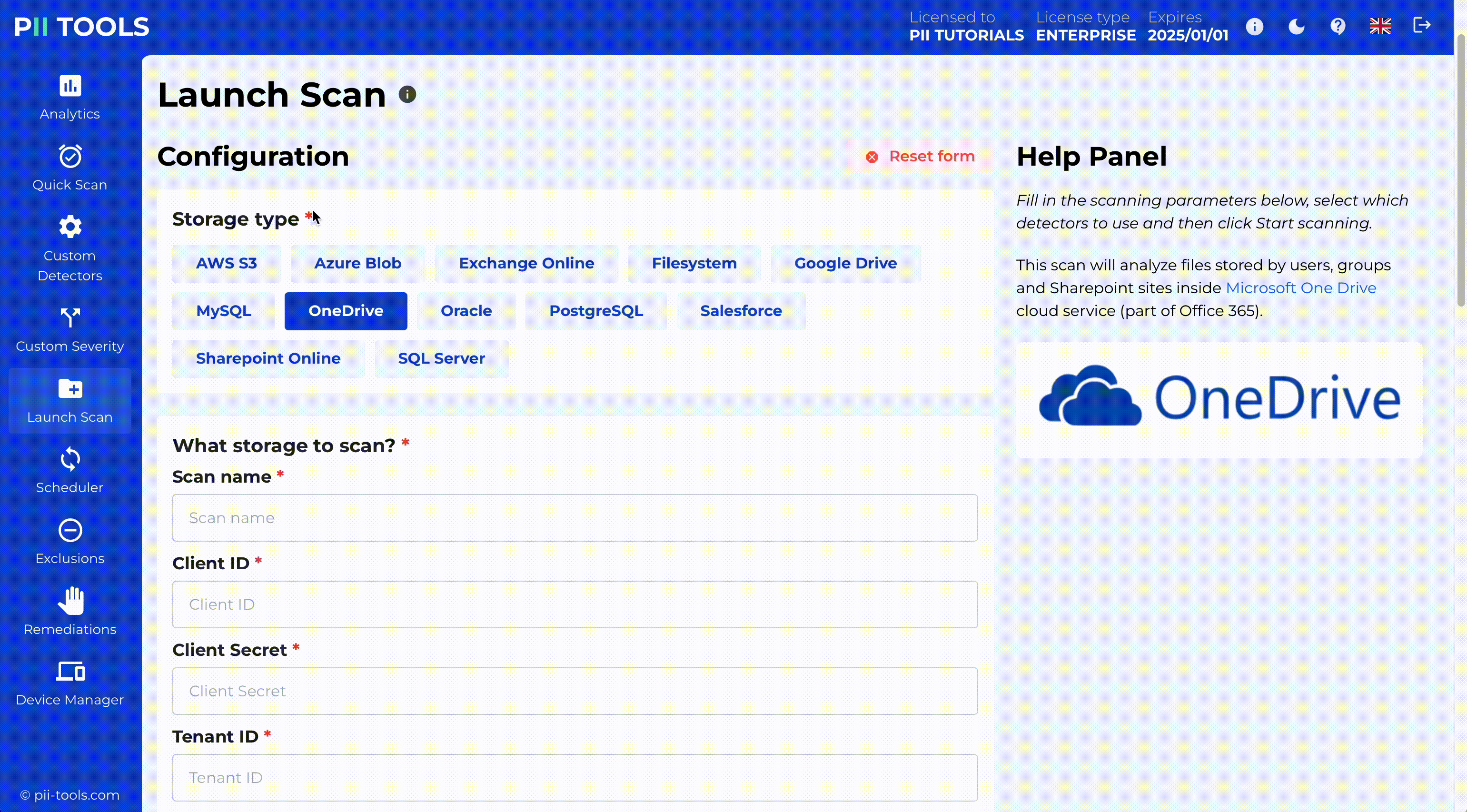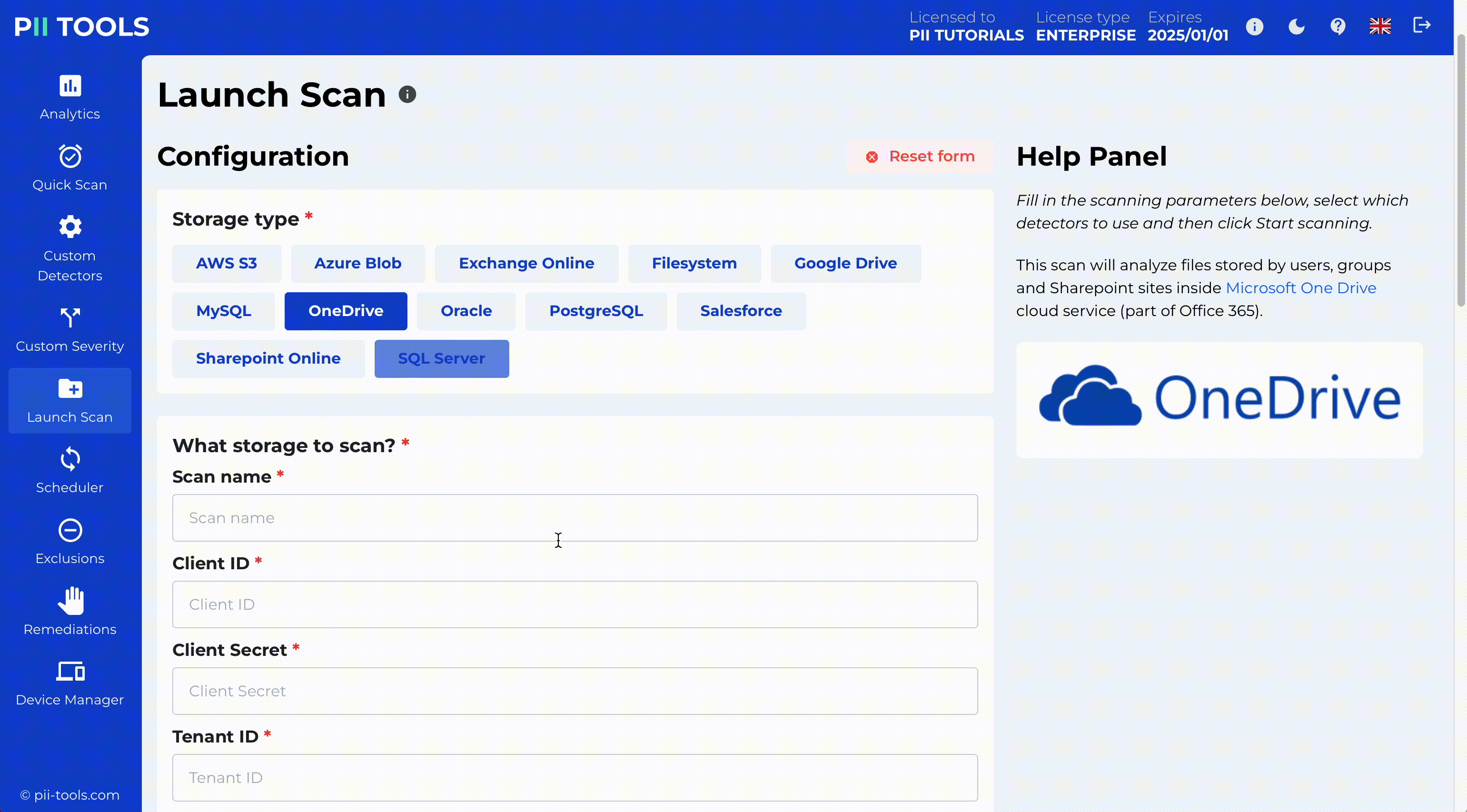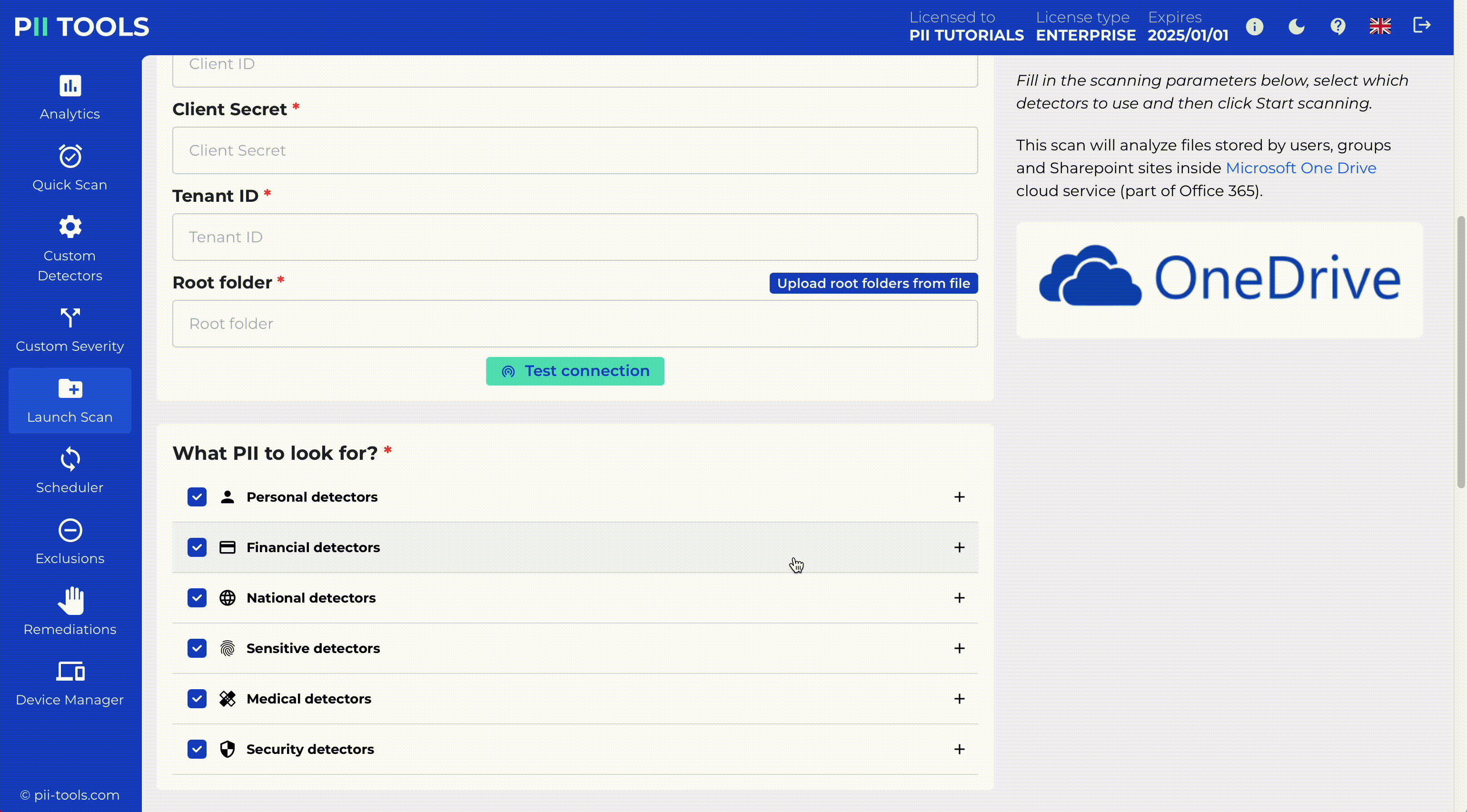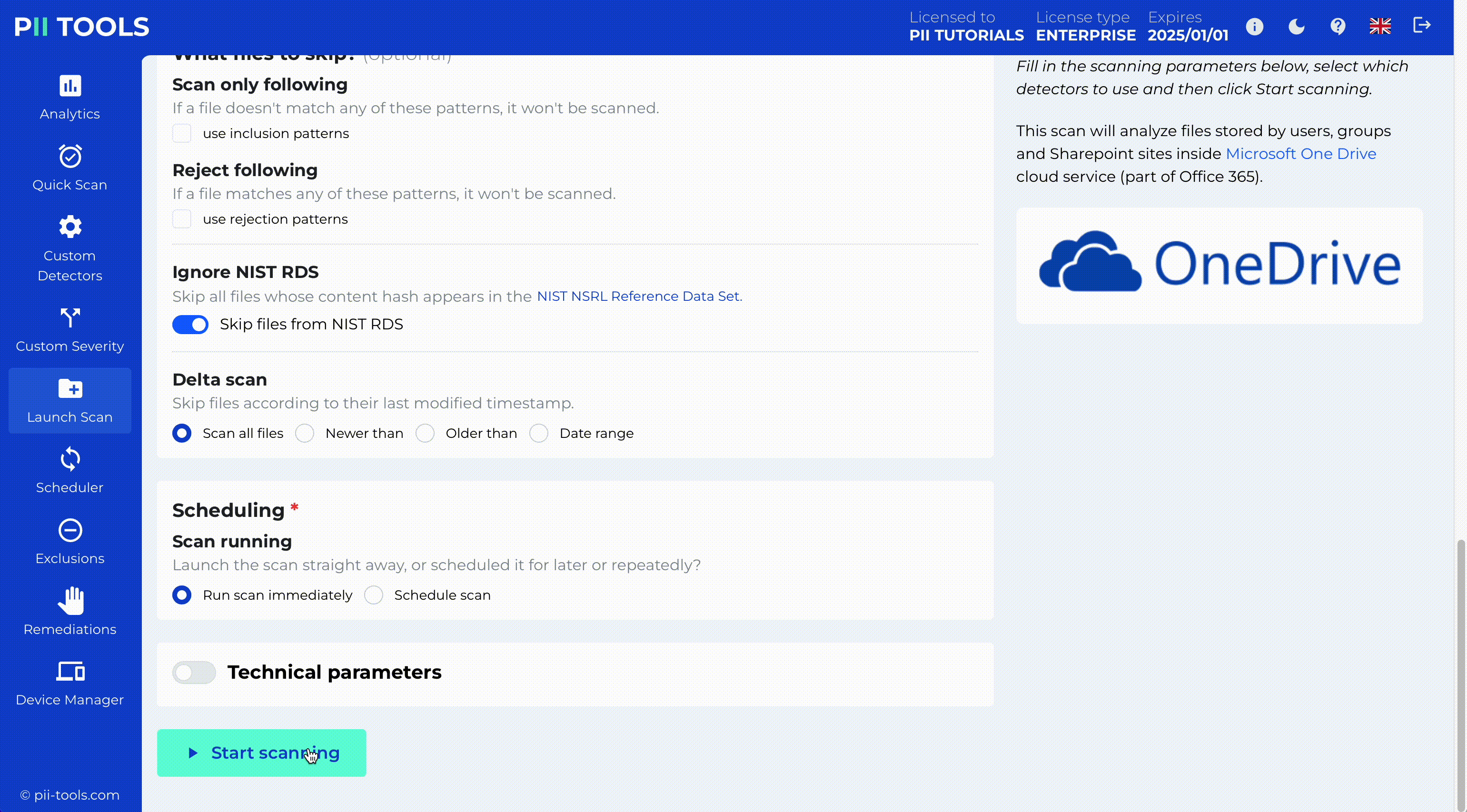
Ready for Your Environment
In-place data redaction is ready for all commonly used file formats and storages like PDFs, images, Office365 Sharepoint, Onedrive, Azure Blob or AWS S3.
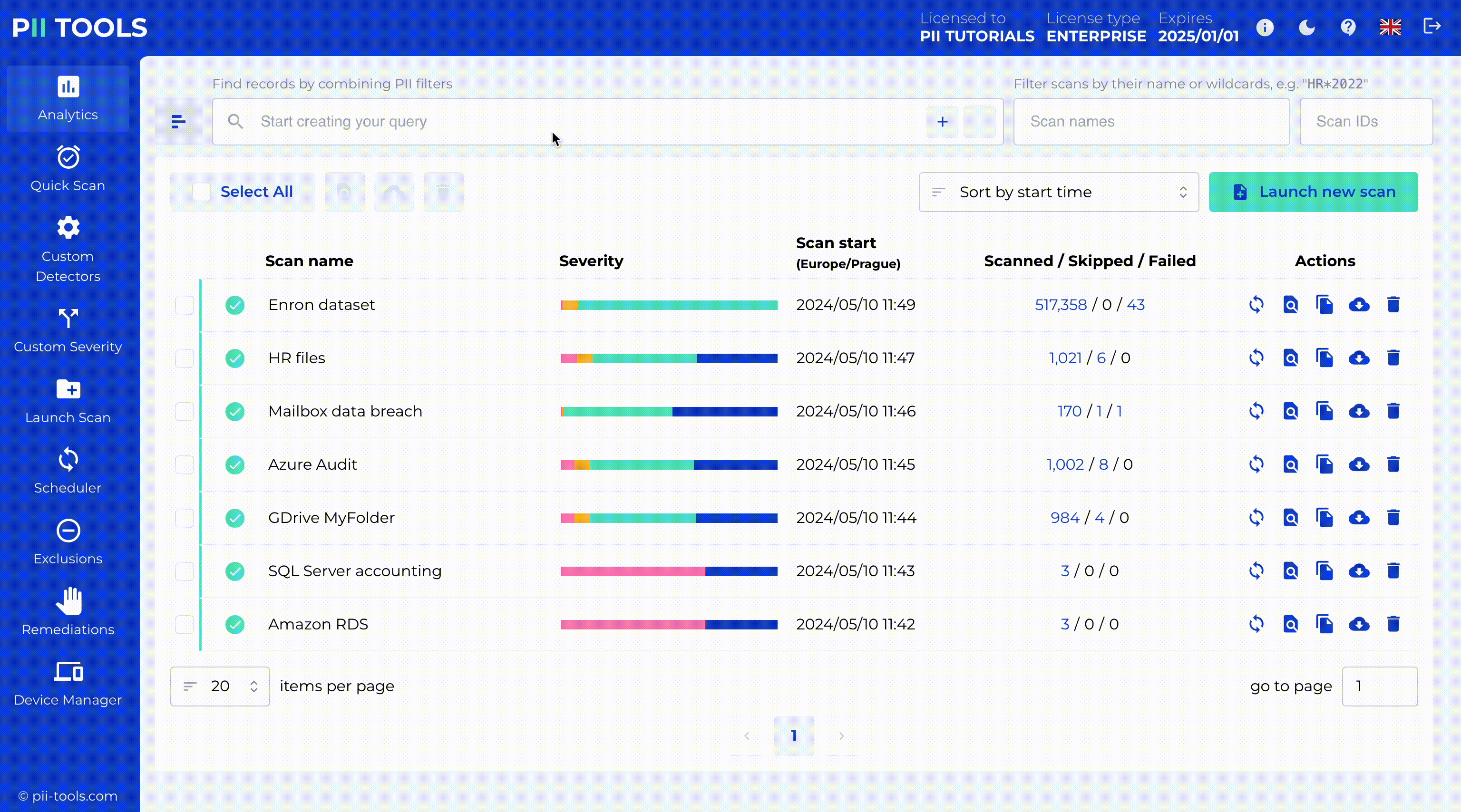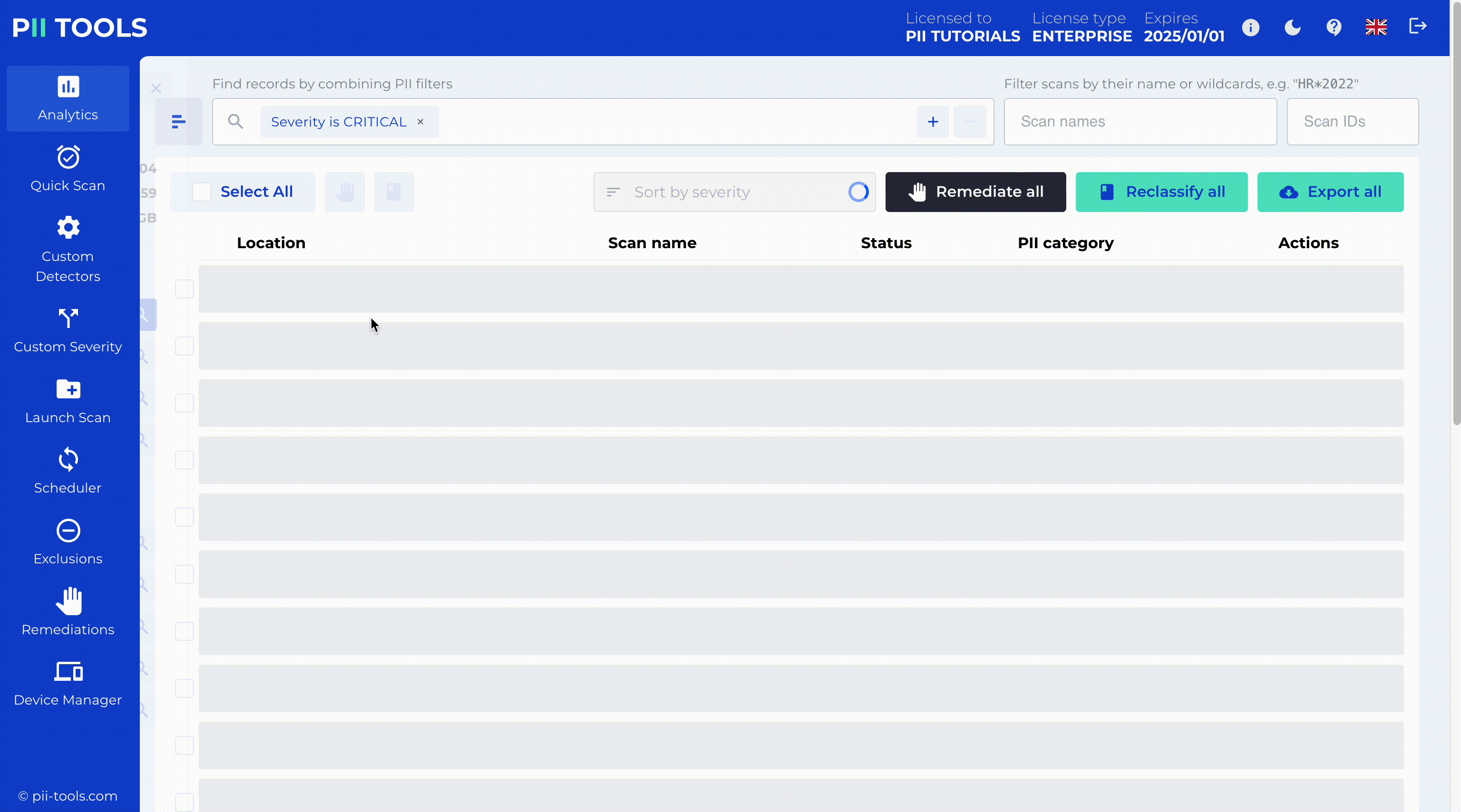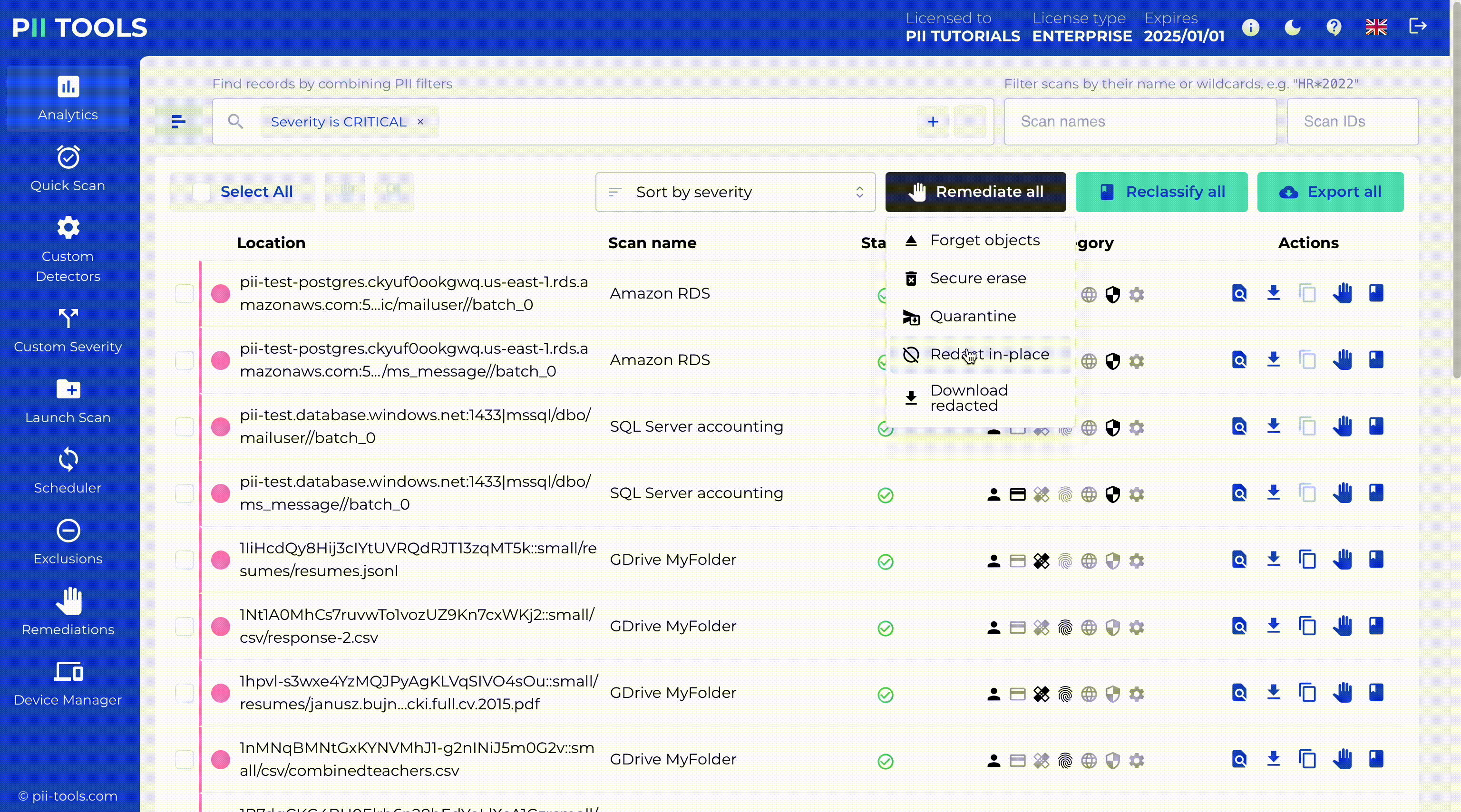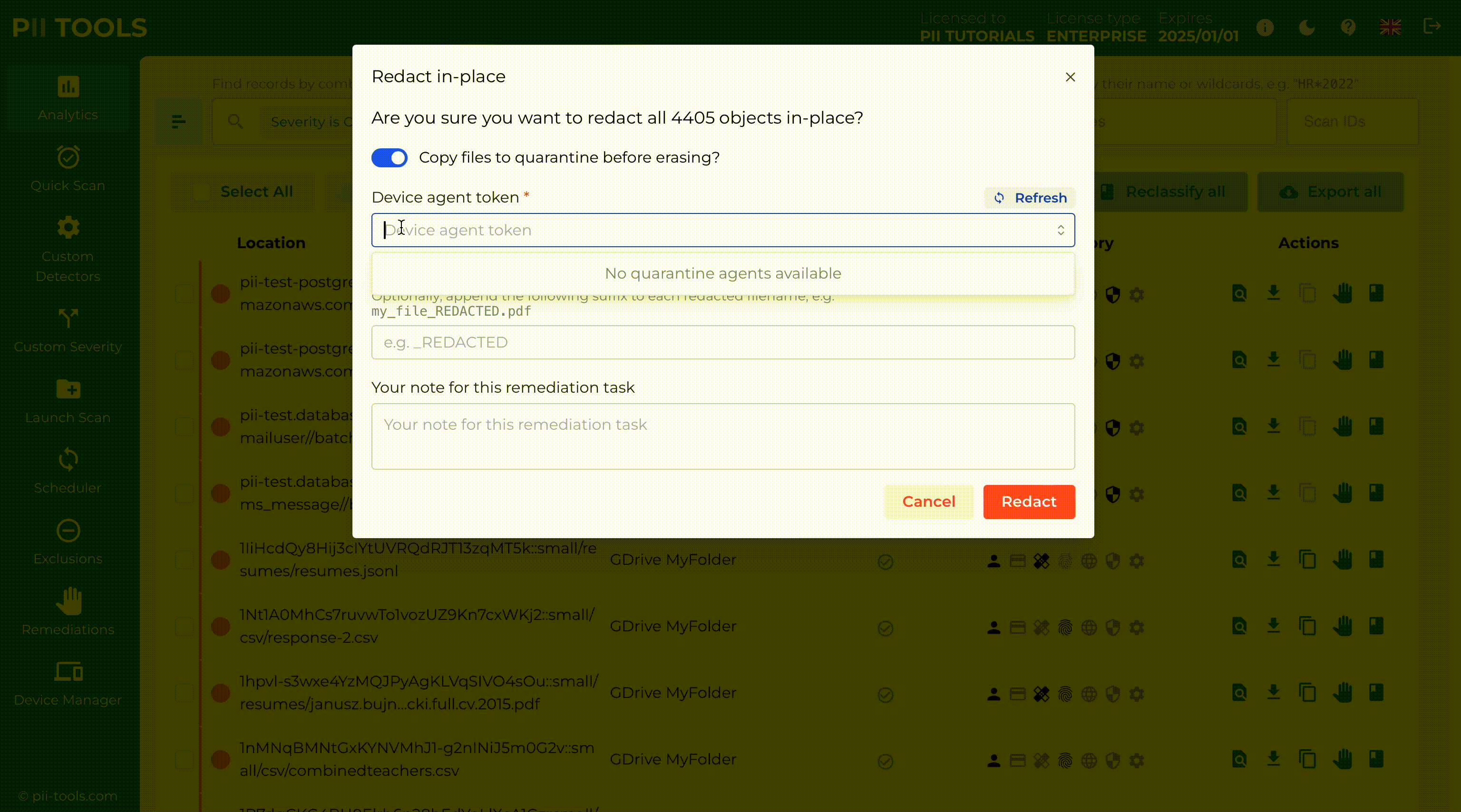
Critical Severity Detection and Redaction
PII Tools enables critical severity detection, identifying the most sensitive data for immediate action. With our intuitive interface, you can redact this data in place while copying the original files to a secure quarantine location for backup or legal hold.
Check out Our Unique Features
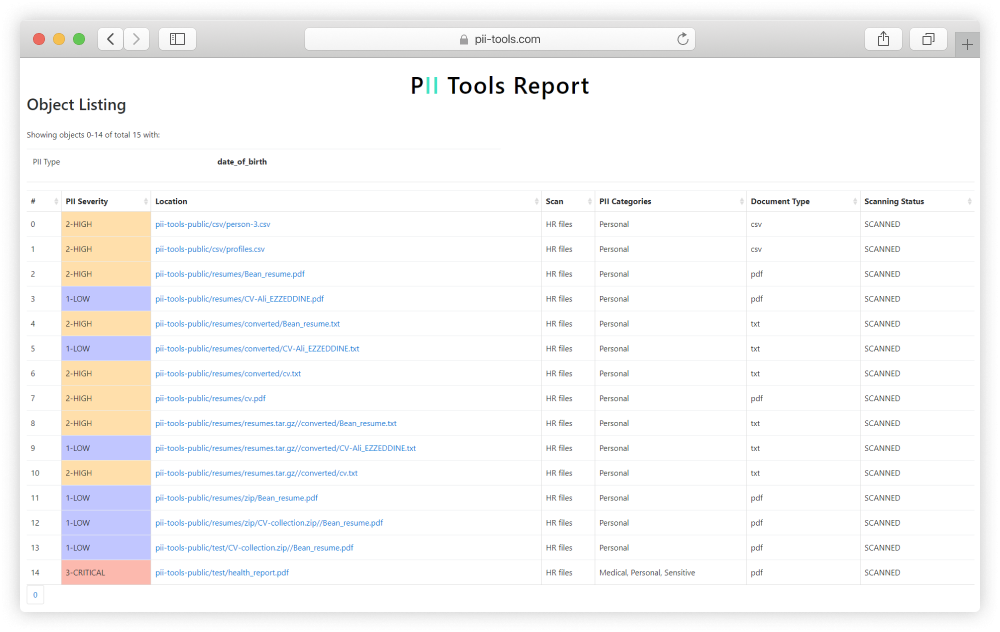
Detect PII Data in 400+ File Formats